Được tin cậy bởi những nhà đổi mới trong đám mây





HuMaIND












HuMaIND












HuMaIND







Bảo Vệ Container của Bạn với Sự Tự Tin
Bảo vệ ứng dụng container từ xây dựng đến runtime. Phát hiện lỗ hổng, cấu hình sai, và mối đe dọa trong thời gian thực để đảm bảo triển khai bền vững và tuân thủ.
Image & Registry Scanning
Ngăn chặn lỗ hổng và bí mật trước khi chúng được triển khai.
Quét hình ảnh container Docker, phát hiện CVE, bí mật mã hóa, và rủi ro tuân thủ trên các registry.
Kubernetes Policy Enforcement
Ngăn chặn cấu hình sai trước khi chúng đến sản xuất
Thực thi RBAC, Tiêu chuẩn Bảo mật Pod, và chính sách mạng tự động.
Runtime Threat Detection
Chặn các cuộc tấn công đang hoạt động trong thời gian thực.
Phát hiện cryptojacking, leo thang đặc quyền, và di chuyển ngang với các hành động phản hồi tự động.
Supply Chain Security
Xây dựng niềm tin từ đầu
Tạo SBOMs, xác thực giấy phép, và ký hình ảnh container để bảo vệ chuỗi cung ứng của bạn.
CI/CD Integrations
Bảo mật được tích hợp vào quy trình của bạn
Kết nối Plexicus vào GitLab, Jenkins, hoặc GitHub Actions để giám sát bảo mật container trong quá trình phát triển.
Bảo Mật Container Đa Giai Đoạn
Bảo vệ toàn diện qua xây dựng, triển khai, và runtime với khả năng hiển thị và phòng thủ thời gian thực.
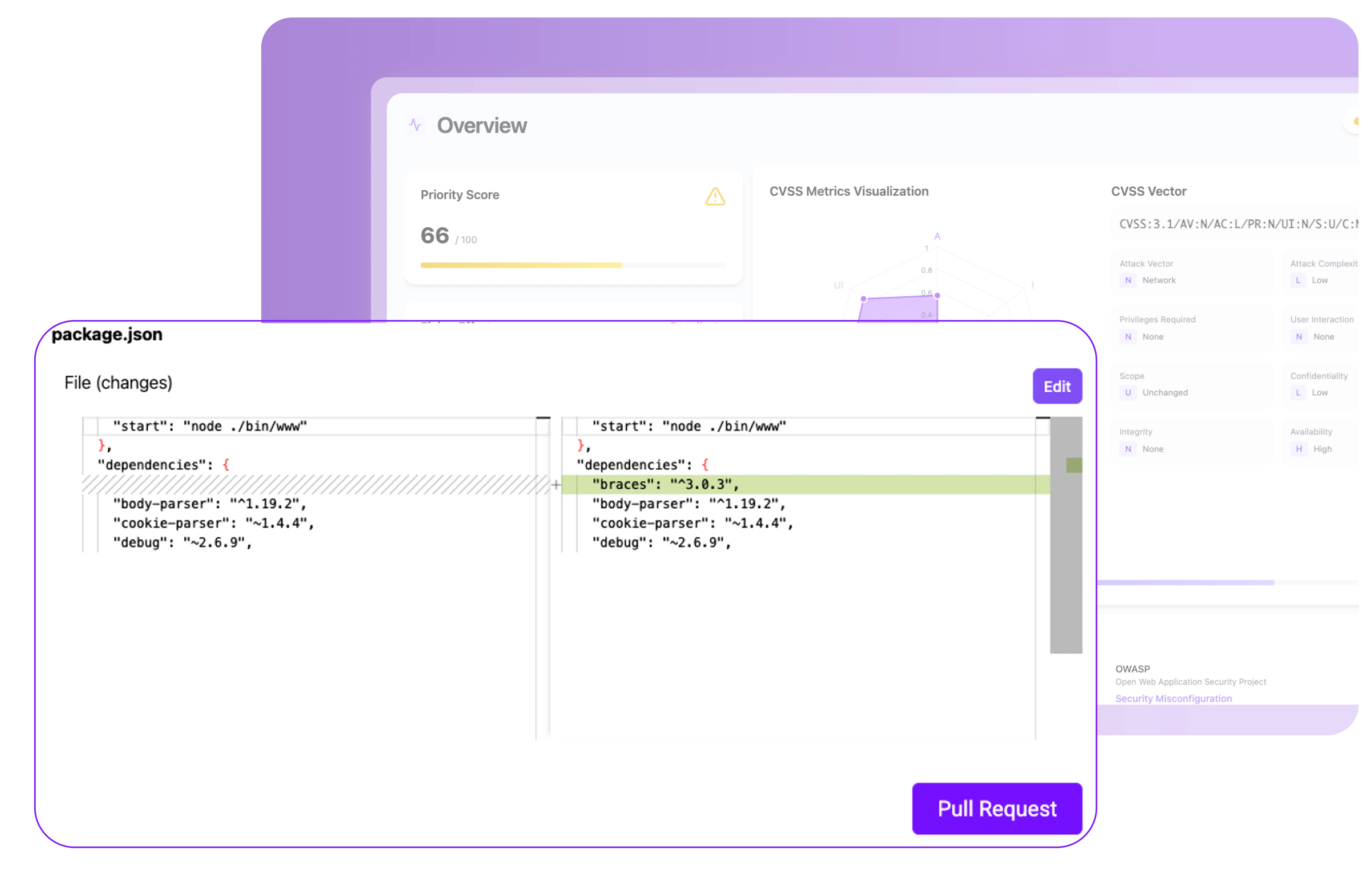
Bảo vệ Container trong 3 bước đơn giản
Plexicus làm cho bảo mật container ứng dụng trở nên dễ dàng, từ xây dựng đến thời gian chạy.
Step 1
Kết nối các kho lưu trữ & cụm của bạn
Cài đặt Bảo mật Container Plexicus trong các kho lưu trữ & cụm
Step 2
Quét & thực thi chính sách
Phát hiện sớm các lỗ hổng và cấu hình sai.
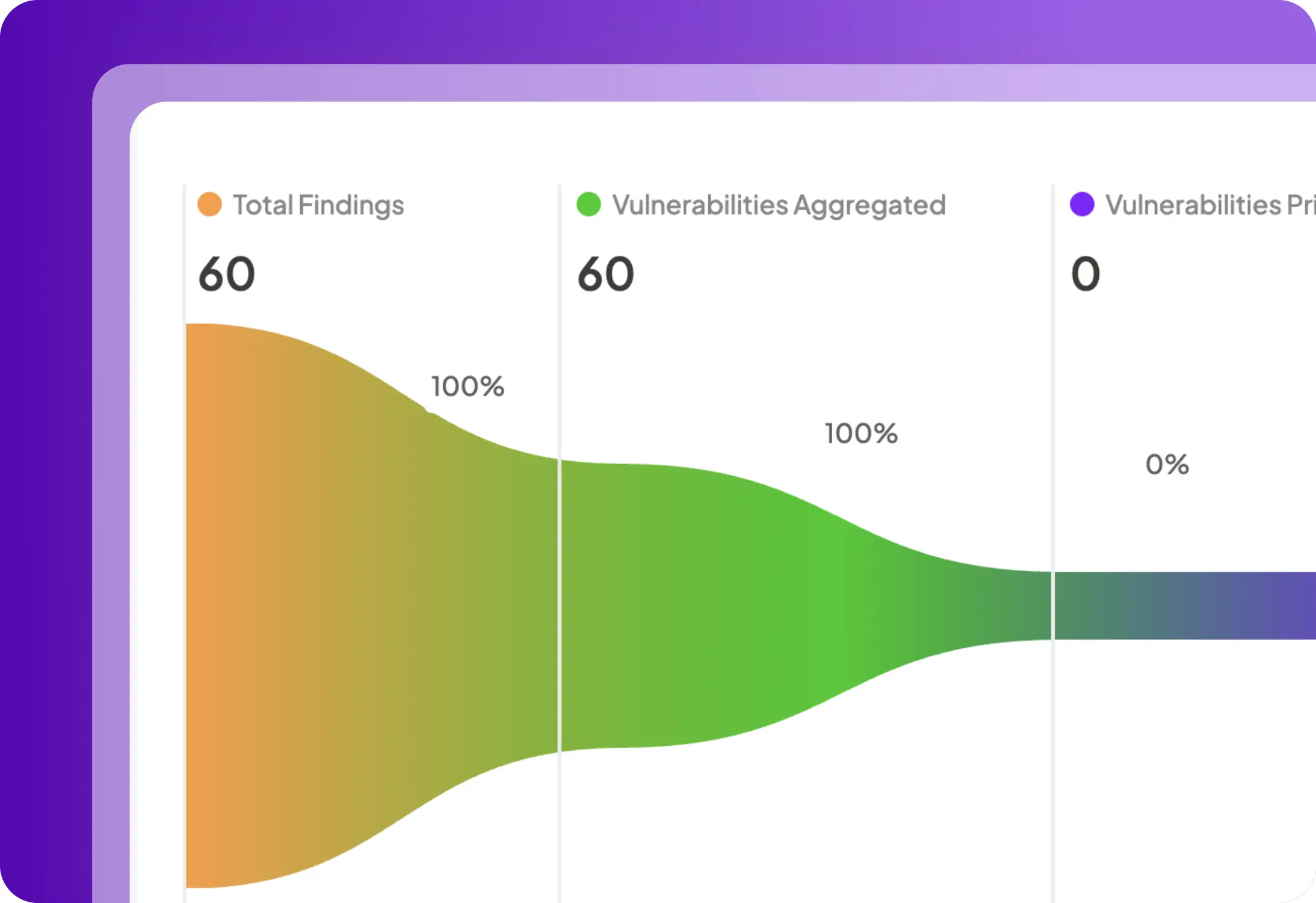
Step 3
Phát hiện & tự động phản hồi
Chặn các mối đe dọa thời gian chạy trước khi gây thiệt hại
Xem Khách Hàng Của Chúng Tôi Đang Nói Gì
Tìm hiểu cách các giải pháp của chúng tôi đã giúp khách hàng đạt được thành công!

"Khả năng của tác nhân AI tự động tạo ra các bản sửa lỗi cho các lỗ hổng đã biến đổi quy trình làm việc của chúng tôi."

David Wilson
Head of Security, HuMaIND