Betroet af innovatorer i skyen





HuMaIND












HuMaIND












HuMaIND







Sikr dine containere med tillid
Beskyt containeriserede applikationer fra opbygning til kørsel. Opdag sårbarheder, fejlkonfigurationer og trusler i realtid for at sikre robuste og overholdelsesvenlige implementeringer.
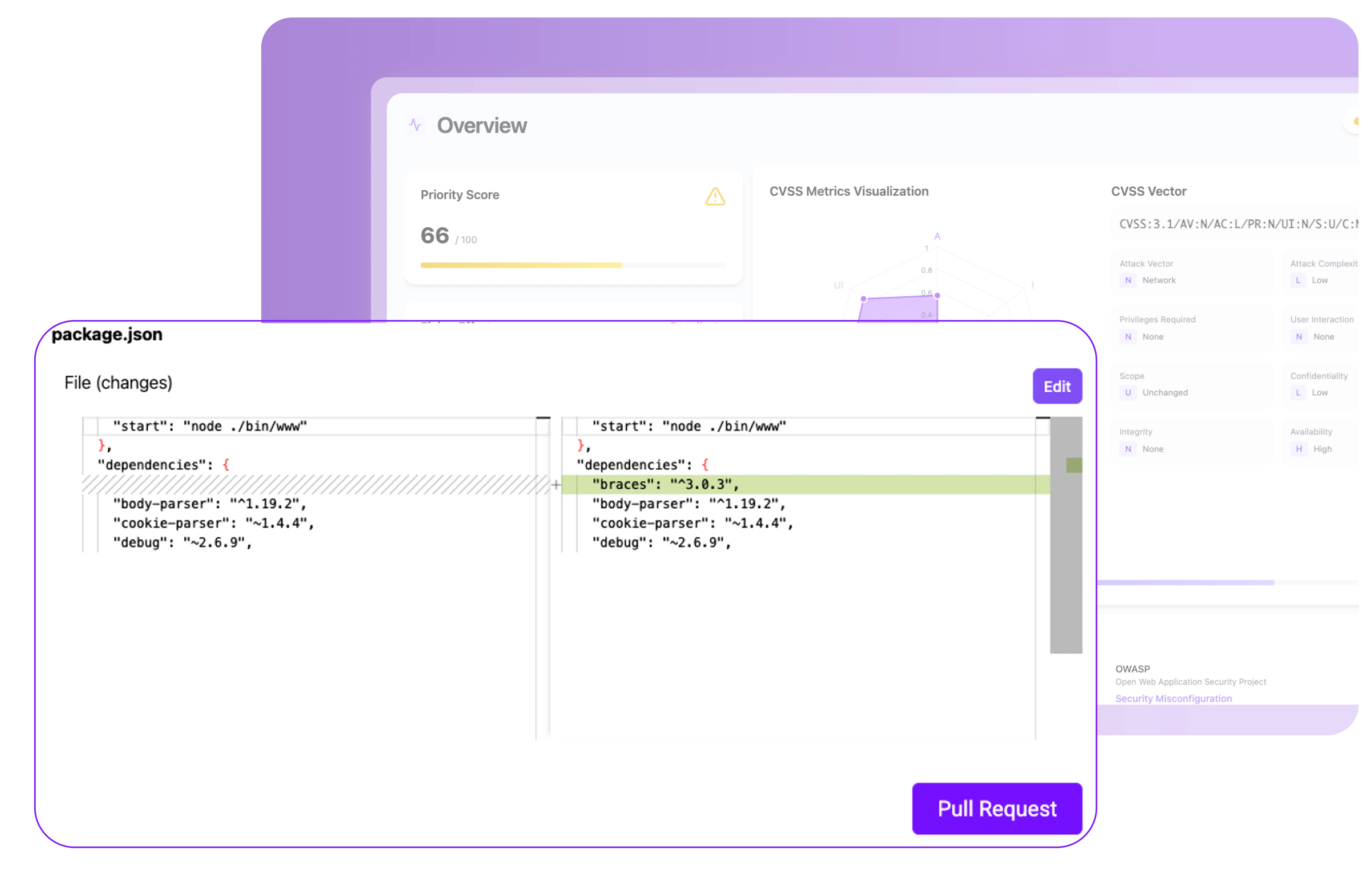
Image & Registry Scanning
Stop sårbarheder og hemmeligheder før de sendes.
Scan Docker container billeder, detekter CVE'er, hardkodede hemmeligheder, og overholdelsesrisici på tværs af registreringer.
Kubernetes Policy Enforcement
Forhindre fejlkonfigurationer før de når produktion
Håndhæv RBAC, Pod Security Standards, og netværkspolitikker automatisk.
Runtime Threat Detection
Bloker aktive angreb i realtid.
Detekter kryptojacking, privilegieeskalering, og lateral bevægelse med auto-respons handlinger.
Supply Chain Security
Opbyg tillid fra starten
Generer SBOM'er, valider licenser, og signer container billeder for at sikre din forsyningskæde.
CI/CD Integrations
Sikkerhed indbygget i din pipeline
Tilslut Plexicus til GitLab, Jenkins, eller GitHub Actions for container sikkerhedsovervågning under udvikling.
Multi-Stage Container Security
Omfattende beskyttelse på tværs af opbygning, implementering og kørsel med realtids synlighed og forsvar.
Sikr beholdere i 3 enkle trin
Plexicus gør applikationsbeholdersikkerhed nem, fra bygning til kørsel.
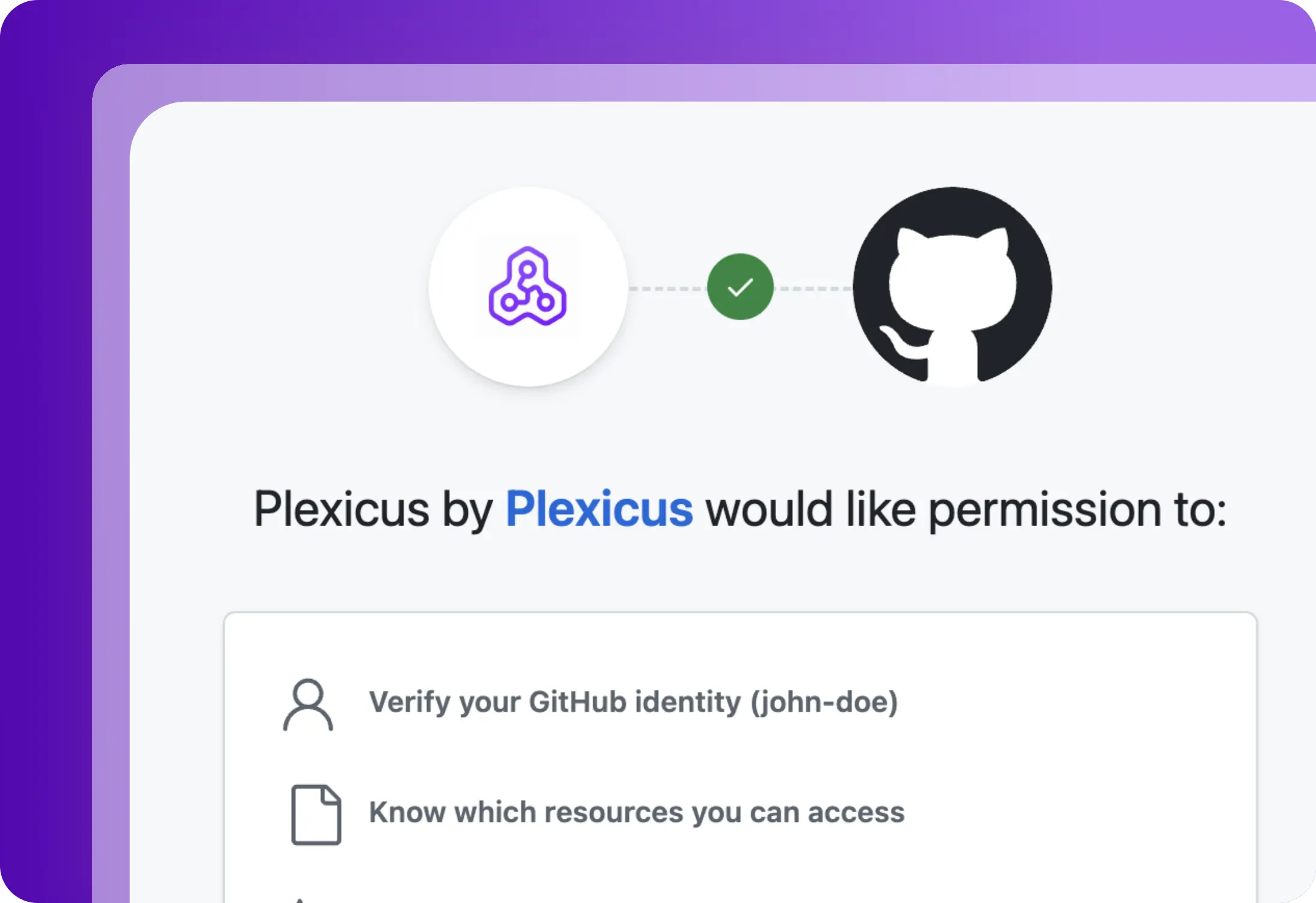
Step 1
Forbind dine registre & klynger
Installer Plexicus Container Security i registre & klynger
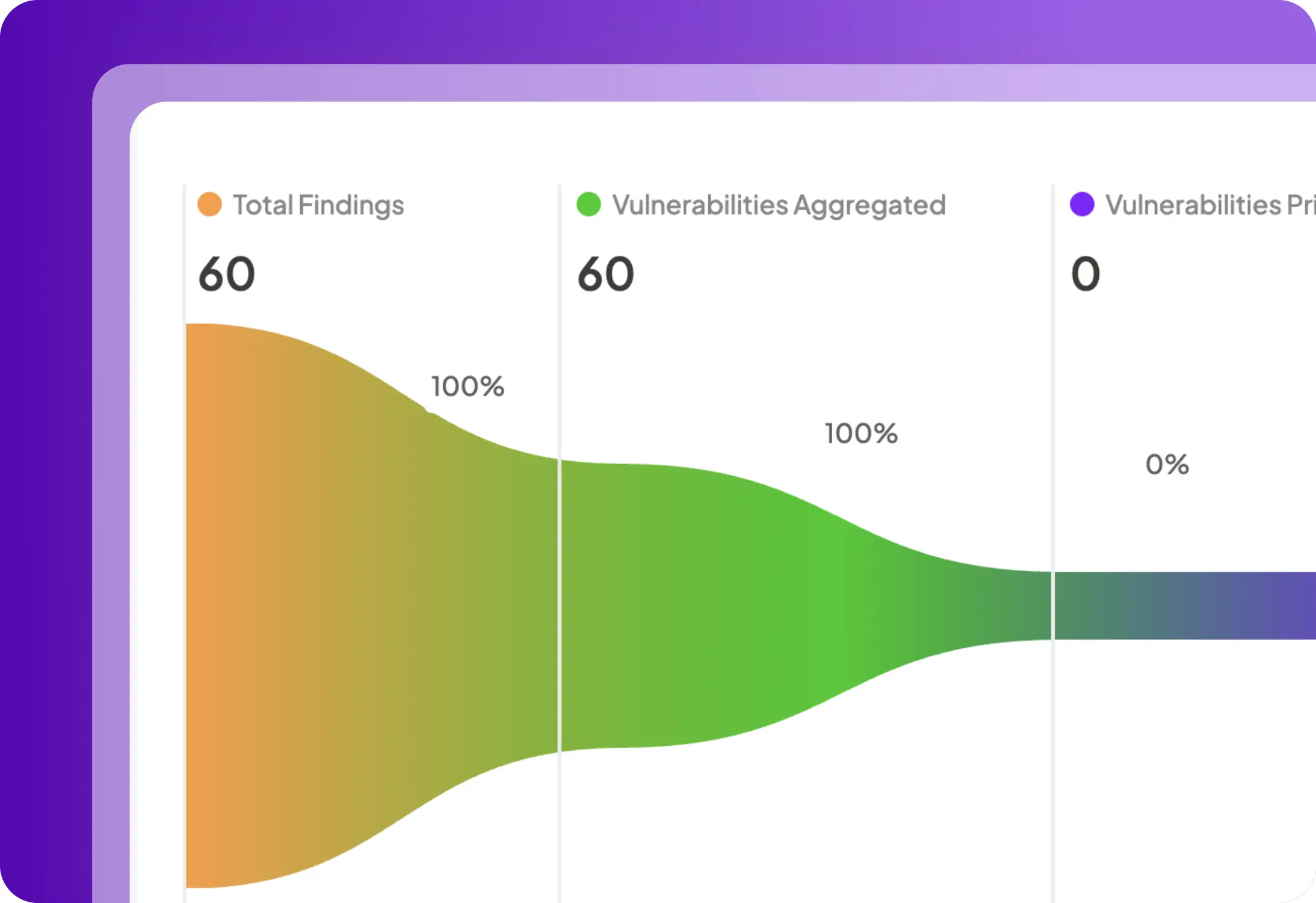
Step 2
Scan & håndhæv politikker
Fang sårbarheder og fejlkonfigurationer tidligt.
Step 3
Registrer & auto-reager
Bloker trusler i kørsel før skaden er sket
Se hvad vores kunder siger
Lær hvordan vores løsninger har styrket vores kunder til at opnå succes!

"AI-agentens evne til automatisk at generere rettelser for sårbarheder har transformeret vores arbejdsgang."

David Wilson
Head of Security, HuMaIND