Never Build Permissions Again
Your applications ship with vulnerabilities.
Static scanners miss 40% of critical flaws.
Manual security reviews bottleneck releases.
Plexicus ASPM fixes the broken application security lifecycle.
Source Code
- Secrets
- SAST Issues
- PII Exposure
Build Pipeline
- Dependencies
- IaC Misconfig
- License Risks
Production
- Runtime Vulns
- API Exposure
- Supply Chain
Plexicus ASPM
Technical Problem: Fragmented Security Tools
Traditional security approaches create more problems than they solve
Key Challenges:
Complex Architectures
Managing security across microservices, containers, and cloud-native environments
73% increase in complexityFast-Paced CI/CD
Addressing vulnerabilities within rapid deployment cycles
5x faster deploymentsAlert Fatigue
Reducing noise from disparate security tools
1000+ daily alertsSecurity vs Speed
Ensuring security empowers rather than hinders development
40% slower releasesTraditional security approaches struggle with these challenges, highlighting the need for a more intelligent and integrated security posture management solution.
Security Team
Facing Modern Challenges
Complex Architectures
73% increase
Core Capabilities
Comprehensive security coverage across your entire application lifecycle
Code Analysis Flow
Source Code
AST Parser
Rule Engine
Codex Remedium
Languages Supported:
Vulnerability Types:
AI-Powered Remediation
Codex Remedium Agent: Your AI security engineer that fixes vulnerabilities automatically
Codex Remedium Workflow
Vulnerability Detected
Context Analysis
- • Code structure analysis
- • Business logic understanding
- • Framework pattern recognition
Fix Generation
Testing & Validation
Example Fix Generation
Before (Vulnerable)
After (Codex Remedium)
Generated Artifacts:
Plexicus ASPM: Your Intelligent Security Co-Pilot
Plexicus ASPM is engineered to overcome modern security challenges by providing a unified, AI-driven platform that integrates seamlessly into your development workflows. We transform application security from a reactive chore into a proactive, intelligent, and automated process.
Complete Visibility
Gain comprehensive insights across your entire application security landscape
AI-Powered Intelligence
Advanced machine learning algorithms that understand context and prioritize threats
Smart Automation
Automated workflows that integrate seamlessly into your development process
Proactive Protection
Stay ahead of threats with predictive security measures and real-time monitoring
Key Benefits:
ASPM Integration
NewSeamlessly integrate security across your entire software development lifecycle with intelligent automation and continuous monitoring.
Code: Static Analysis & Secret Detection
Real-time vulnerability scanning and secure coding pattern enforcement directly in your IDE and repositories.
Build: Dependency & Container Security
Automated scanning of dependencies and container images with vulnerability blocking before deployment.
Testing: Dynamic Security Testing
Intelligent security test generation and automated penetration testing with comprehensive coverage.
Deploy: Infrastructure Security Validation
Configuration scanning and compliance checks ensuring secure deployment practices.
Monitor: Runtime Protection & Monitoring
Continuous threat detection and automated incident response with real-time security insights.
Code Analysis
Static code analysis identifies security vulnerabilities, coding errors, and compliance issues directly in your source code.
- Detect security vulnerabilities early
- Enforce secure coding standards
- Identify sensitive data exposure risks
AI Security Analysis
Real-time vulnerability detection and analysis
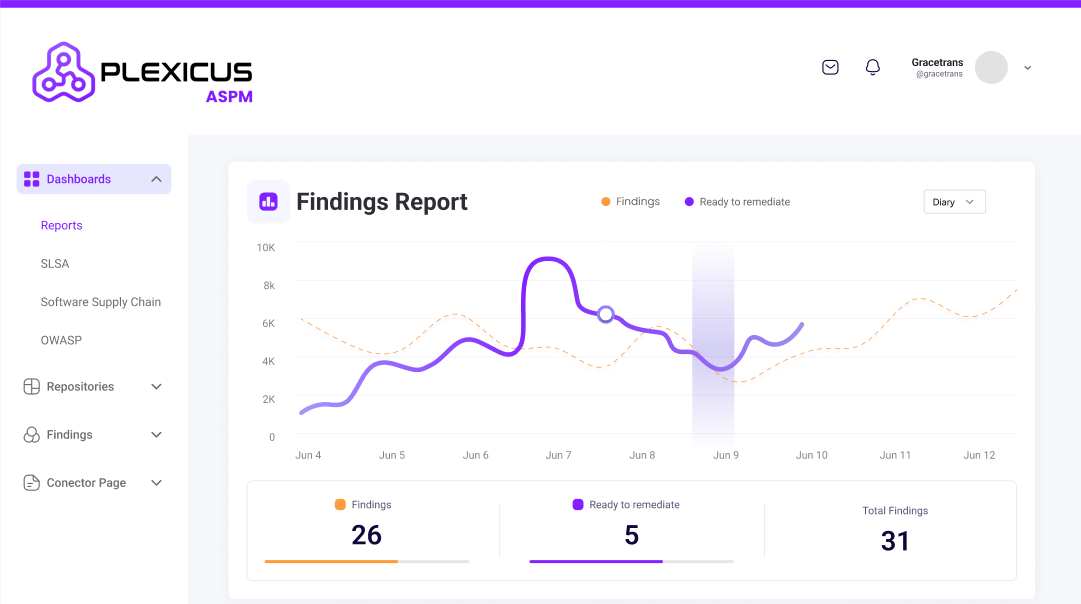
Security Findings
Compliance Automation
Automated compliance monitoring and reporting for industry standards
SOC 2 Type II
Automated Controls:
ISO 27001:2022
Automated Controls:
Automated Compliance Reporting
Real-time compliance status and audit-ready documentation
Real-World Impact
Measurable improvements in security posture and developer productivity
Security Alerts
Weekly Triage Time
False Positive Rate
Average Fix Time
Transform Your Security Posture
Get Started
Choose your path to implementing Plexicus ASPM in your organization
For Developers
Scan your local repository for vulnerabilities
# Scan your local repository for vulnerabilities
python analyze.py --config=aspm-dev-config.yaml --files="./" --output=pretty
For DevSecOps Teams
Integrate ASPM into your CI/CD pipeline
# Integrate ASPM into your CI/CD pipeline
curl -X POST "https://api.plexicus.com/receive_plexalyzer_message" -H "Authorization: Bearer {PLEXICUS_TOKEN}" -H "Content-Type: application/json" -d '{
"request": "create-repo",
"request_id": "cicd-aspm-setup",
"extra_data": {
"repository_name": "{CI_PROJECT_NAME}",
"repository_url": "{CI_PROJECT_URL}",
"auto_fix_enabled": true,
"fail_on_severity": "high"
}
}'
For Security Architects
Configure custom security policies and rules
# Configure custom security policies and rules
curl -X POST "https://api.plexicus.com/receive_plexalyzer_message" -H "Authorization: Bearer {PLEXICUS_TOKEN}" -H "Content-Type: application/json" -d '{
"request": "configure-aspm",
"request_id": "architect-aspm-setup",
"extra_data": {
"repository_id": "{MASTER_REPO_ID}",
"custom_rules_path": "./security/rules.rego",
"policy_inheritance": true
}
}'
