Plexicus vs. Jit: Which AI DevSecOps Tool Actually Fixes Your Backlog?
By 2026, DevSecOps discussions have changed. Finding vulnerabilities is not the main challenge anymore. Now, the biggest issue is the large amount of security debt that developers do not have time to address.
If you are comparing Plexicus and Jit, you are considering two main approaches: Autonomous Remediation and Unified Orchestration. Both platforms try to make things easier, but they have different philosophies and provide distinct experiences for your engineers.
This guide gives a straightforward, unbiased comparison of Jit and Plexicus within real-world DevSecOps workflows.
Quick Comparison Summary
| Feature | Plexicus | Jit |
|---|---|---|
| Core Philosophy | Remediation-First: Uses AI to fix the code it finds. | Orchestration-First: Unifies the “Security-as-Code” stack. |
| Automation Level | High: Autonomous AI agents generate/test PR patches. | Moderate: AI-assisted triage and “one-click” fixes. |
| Key Differentiator | Codex Remedium: AI that writes functional code. | Security Plans: YAML-based multi-tool orchestration. |
| Primary User | DevSecOps & Teams with high security debt. | Developers & Teams building a stack from zero. |
| Cloud Support | AWS, Azure, GCP, Oracle Cloud. | AWS, Azure, GCP. |
What Is Plexicus?
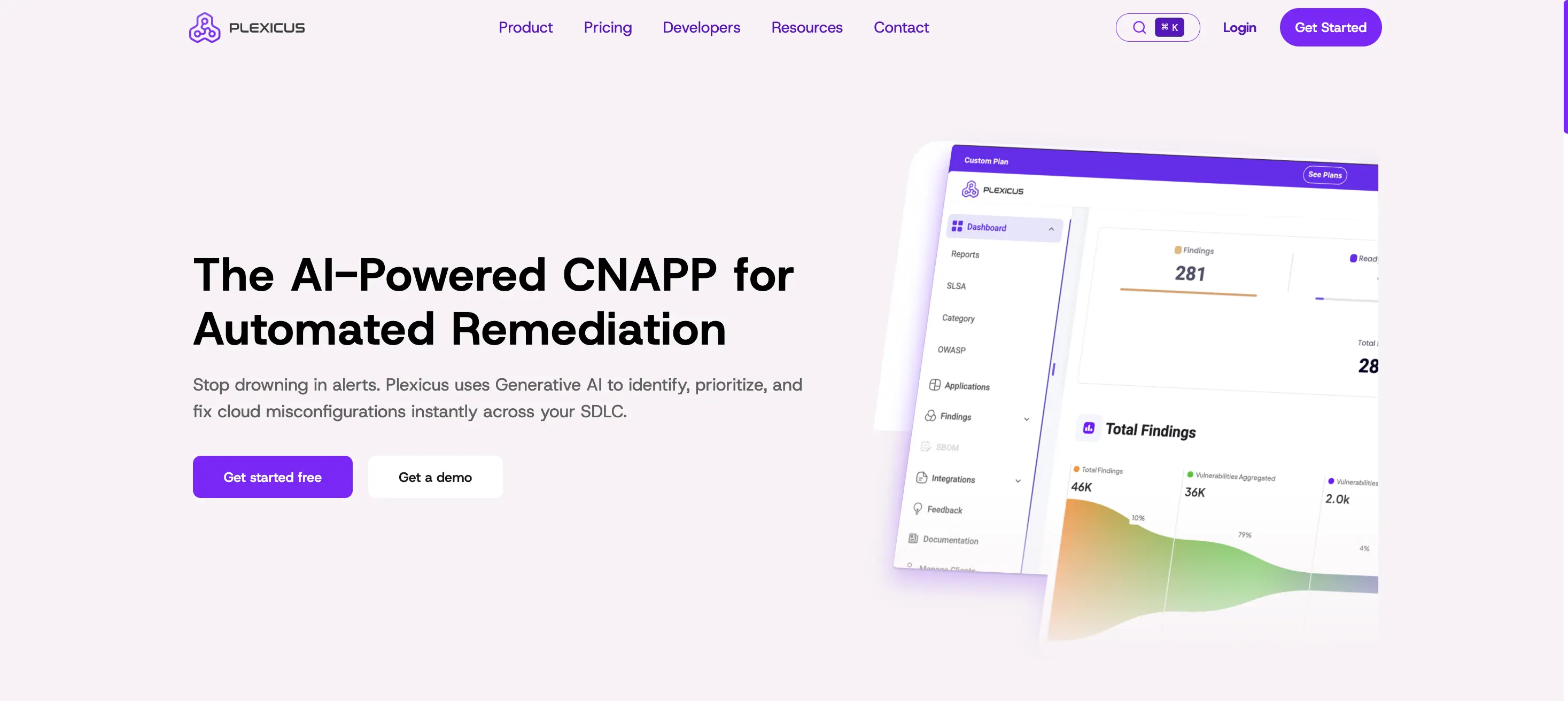
Plexicus is an AI-based Cloud-Native Application Protection (CNAPP) and Application Security Posture Management (ASPM) platform designed for what it calls the era of ‘automated silence.’
- The problem is that traditional scanners create too much noise. They generate tickets that developers commonly end up ignoring.
- Plexicus tackles this by using its Codex Remedium AI engine to connect detection and remediation. Instead of just sending alerts, it analyzes the code, understands the logic, and creates a working Pull Request (PR) with the fix.
- The goal is to lower Mean Time to Remediation (MTTR) by automating the routine work of patching. This lets developers spend more time reviewing and approving fixes instead of writing them.
What Is Jit?
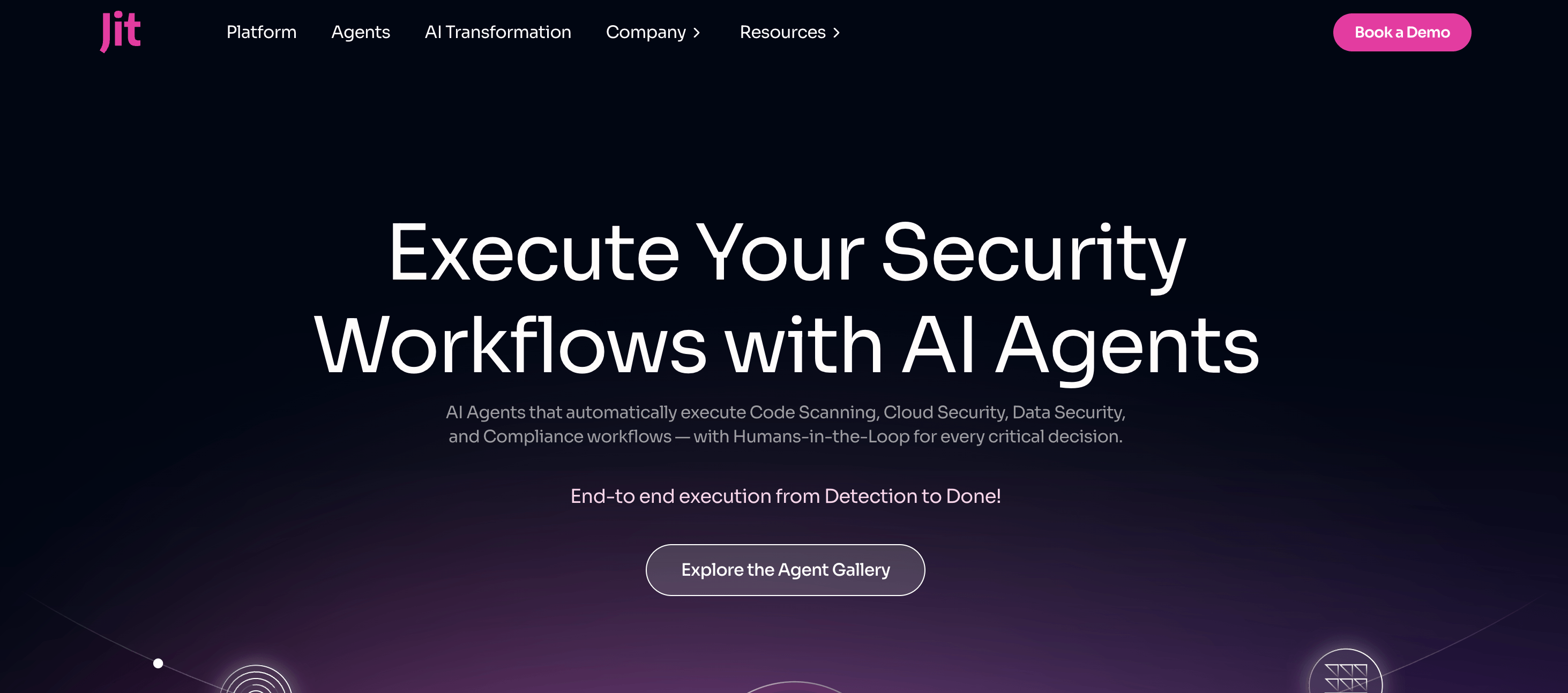
Jit (Just-In-Time) is an Application Security Orchestration platform that makes the “Minimum Viable Security” stack effortless to deploy.
- The problem is that managing separate tools for SAST, SCA, secrets, and IaC can be a major operational headache.
- Jit solves this by combining popular open-source tools like Semgrep and Trivy into one developer-friendly platform. With its Security Plans, you can set up a complete security process across your GitHub organization in just a few minutes.
- The goal is to give developers a single, unified view of all application security findings right in their workflow.
Core Differences at a Glance
- “The Fixer” vs. “The Manager”: Plexicus is an AI agent that does the work (writing code). Jit is a management layer that coordinates the tools (running scans).
- Native Reachability: Plexicus includes Plexalyzer, which determines if a vulnerability is actually “reachable” in production. Jit uses “Attack Path” analysis to visualize risk, but Plexicus focuses more on using that data to order which AI fixes to run first.
- Tooling Depth: Jit relies heavily on orchestrating other tools (open-source or commercial). Plexicus is a more unified platform, where the intelligence is baked into the remediation agent itself.
Feature-by-Feature Comparison
1. Remediation Workflow
-
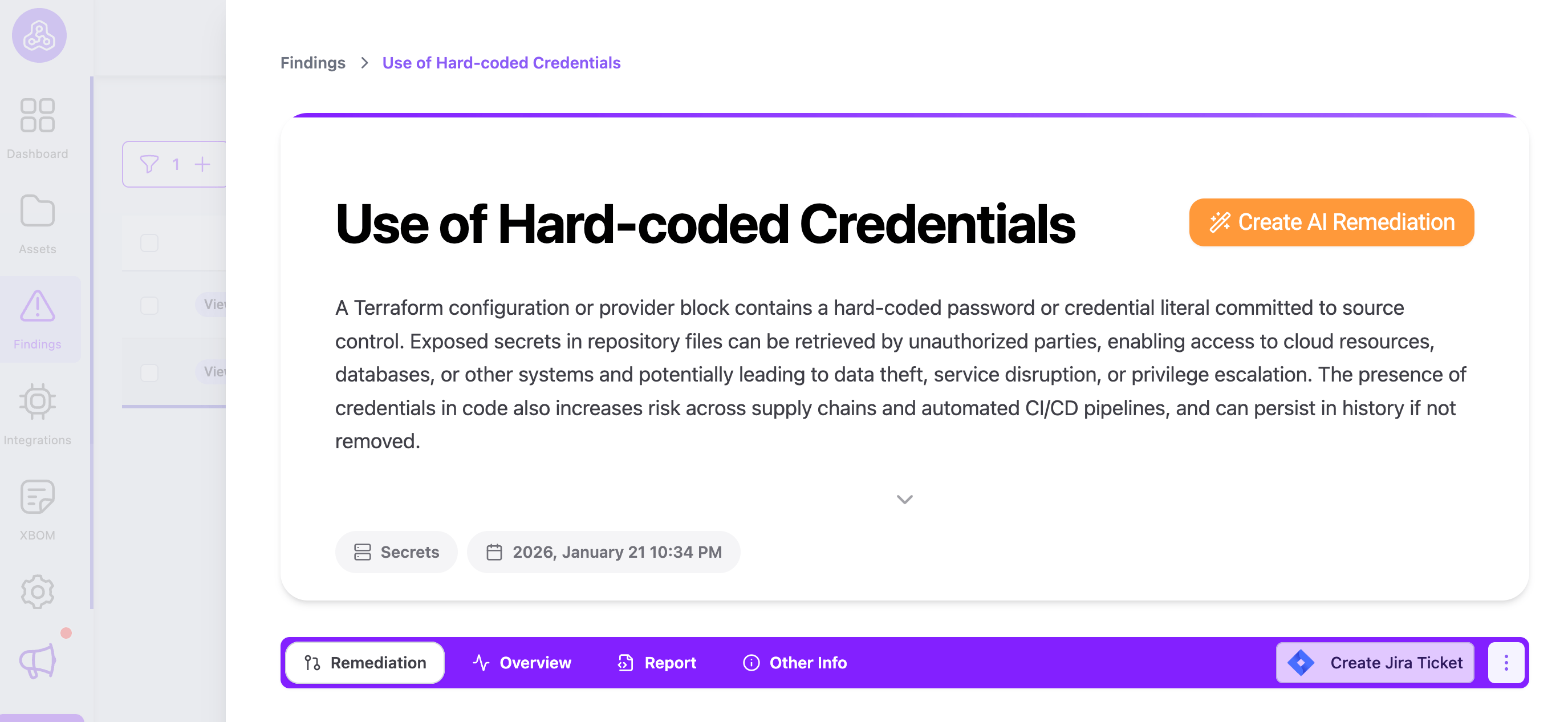
Plexicus: This is its “Killer Feature.” When a vulnerability is detected, Plexicus triggers its Codex Remedium AI engine. This agent clones the repository to a temporary directory, generates a code-level fix using AI in an isolated Docker sandbox, extracts the changes as a git diff, and automatically opens a pull request with the remediation. The PR can then be validated in your existing CI/CD pipelines (such as GitHub Actions) to ensure there are no regressions before merging.
-
Jit: Focuses on “Inline Fixes” and “One-Click Remediation.” For common issues (such as an outdated library), Jit can automate the version bump. For more complex code vulnerabilities, it provides a suggested fix that the developer can review and apply with a click.
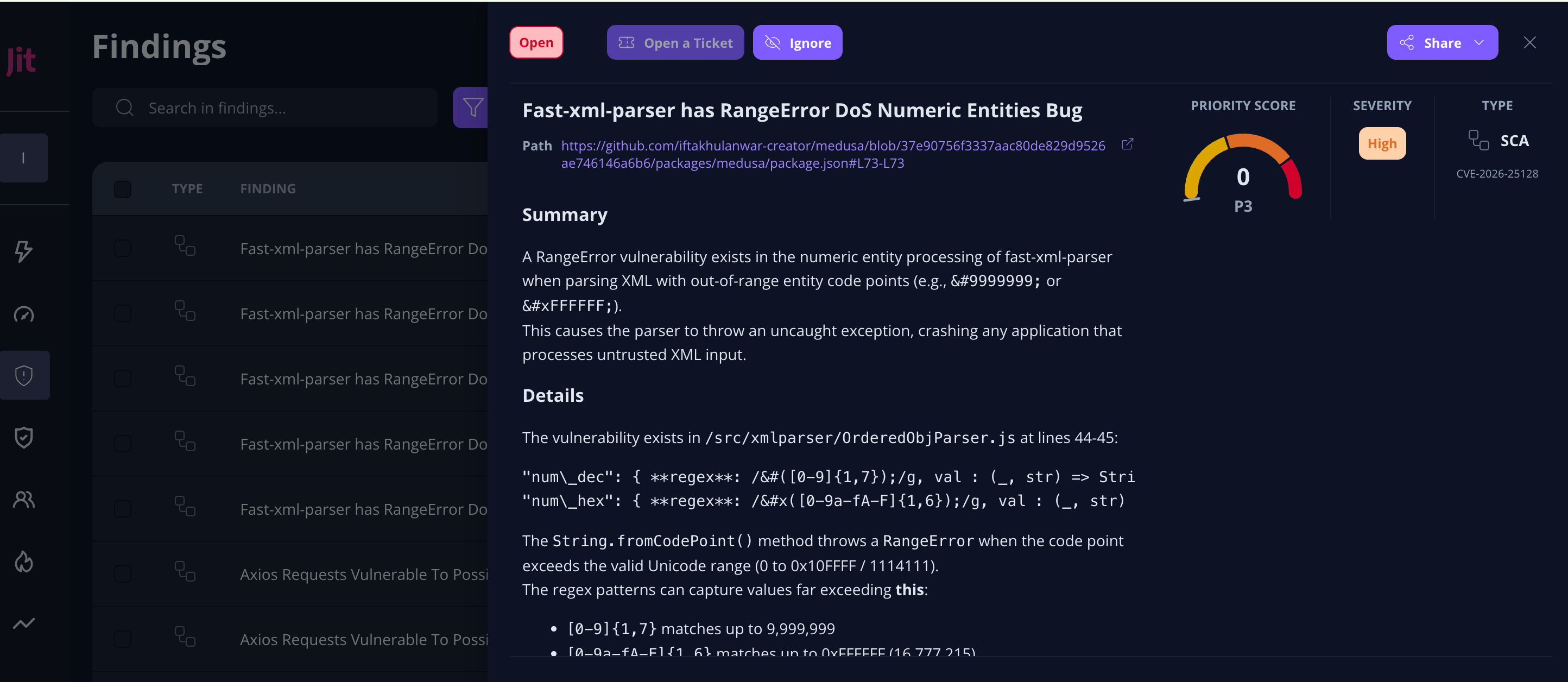
2. Developer Experience (DX)
- Jit: Optimized for the Shift Left movement. It lives in the PR. If a developer includes a secret or a vulnerable package, Jit comments immediately. The experience is designed to be “invisible” until a fix is needed.
- Plexicus: Optimized for “Security Silence.” By automating the remediation, Plexicus aims to keep the developer’s Jira/Ticket queue empty. The developer primarily interacts with Plexicus at the Merge stage rather than the Triage stage.
3. Integration & Scalability
- Jit: Excellent for teams that love open-source. It lets you swap tools (e.g., swapping one SAST engine for another) without changing the developer workflow.
- Plexicus: Supports multi-cloud environments via integrating with commonly used cloud security tools (Prowler and CloudSploit) and providing native scanning capabilities for AWS, Azure, GCP, and Oracle Cloud Infrastructure. The platform is built for enterprise environments, with features such as role-based access control (RBAC), multi-tenancy support, and webhook integrations for custom ticketing systems.
Automation & Developer Impact
In 2026, the highest cost in security isn’t the license; it’s engineering time.
- Jit saves time on setup and visibility. You no longer need a dedicated person to manage 10 different security tools.
- Plexicus saves time on execution. It removes the “Research -> Patch -> Test” loop that currently consumes roughly 20% of an average developer’s week.
Pros & Cons
Plexicus
Pros:
- Autonomous AI-powered remediation: Generates code fixes through the Codex Remedium engine and automatically creates pull requests for review
- Comprehensive security coverage: Integrates 26+ tools across SAST, SCA, secrets detection, container scanning, and multi-cloud security (AWS, Azure, GCP, Oracle OCI)
- Three-tier remediation strategy: Intelligently routes findings to mutes (false positives), library updates, or AI-generated patches based on finding type
Cons:
- Requires PR review process: AI-generated patches need human review before merging, requiring team buy-in for AI-assisted workflows
- Higher cost than DIY open-source: Advanced features carry a higher initial investment than basic open-source setups.
Jit
Pros:
- Fastest “Zero-to-One” setup in the industry.
- Unified view of all open-source security tools.
- Transparent, per-developer pricing.
Cons:
- Limited by the scanners it orchestrates, it can’t fix what the scanner doesn’t fully understand.
- A high volume of alerts can still lead to triage fatigue.
When Plexicus Makes More Sense
Plexicus is the better fit for scaling engineering teams that are already “security aware” but are drowning in a backlog of vulnerabilities.
If your security team spends all day chasing developers to “please update this library,” Plexicus will solve that problem by simply doing the update for them.
When Jit Might Be a Better Fit
Jit is the better choice for startups and lean teams that currently have no security tooling. If you need to pass a SOC 2 audit next month and need to get SAST, SCA, and Secret scanning running across 50 repos by tomorrow morning, Jit is the most efficient path.
Keys Takeaway
The decision between Plexicus and Jit comes down to a simple question: Do you need more eyes on the problem, or more hands on the keyboard?
Jit provides the eyes to deliver a unified, crystal-clear view of your risks.
Plexicus provides the hands, an AI partner that actually writes the code to close those risks.
Frequently Asked Questions (FAQ)
1. Does Jit actually fix code the way Plexicus does?
Not really. Jit has come a long way with its “Agentic AppSec” approach, but it’s still primarily focused on helping developers fix issues. It offers one-click actions (like bumping a dependency version) and AI-generated suggestions that developers review and apply themselves.
Plexicus is different by design. It’s built for autonomous remediation - its AI (Codex Remedium) actually writes the fix in an isolated Docker sandbox, creates a branch, and opens a pull request for review. The PR is then validated in your existing CI/CD pipelines (such as GitHub Actions) to ensure there are no regressions before merging.
2. Can Plexicus and Jit be used together?
Yes, and that’s pretty common. Many teams use Jit as their “control panel” to run and organize multiple scanners, then rely on Plexicus to actually clear the remediation backlog. Since both tools integrate with GitHub and GitLab and are API-first, they work well side by side. Jit gives you visibility, and Plexicus does the heavy lifting.
3. Which one helps more with passing a SOC 2 audit?
It depends on what stage you’re at:
- Jit is usually better for getting compliant fast. Its security-as-code setup helps teams quickly spin up the required scanners, especially for startups facing their first SOC 2 audit.
- Plexicus shines once you’re already compliant. Automatically fixing vulnerabilities helps prevent issues from sitting open too long and pushing you out of compliance during ongoing audits.
4. How do they deal with false positives?
Both try to reduce noise, but in different ways:
- Plexicus detects false positives through analyzing code context - distinguishing test files, documentation, and examples from production code. If it can’t identify where to fix an issue, it’s likely a false positive and can be automatically suppressed.
- Jit focuses on context. It checks whether a resource is internet-facing or handles sensitive data, and then decides whether an alert is truly critical or merely informational.
5. What about multi-cloud support?
- Plexicus supports all major cloud providers, including AWS, GCP, Azure, and Oracle Cloud (OCI), making it a strong option for teams with complex or mixed environments.
- Jit covers AWS, Azure, and GCP well, but its cloud security focus is primarily on infrastructure-as-code (such as Terraform and CloudFormation) rather than deep runtime protection.

