10 Best ASPM Tools in 2025: Unify Application Security and Gain Full Code-to-Cloud Visibility
Application Security Posture Management (ASPM) tools help DevSecOps teams secure applications throughout the software lifecycle, from initial code to cloud deployment.
According to Cloud Security Alliance (CSA), only 23 % of organizations have full visibility into their cloud environment, and 77 % experience less-than-optimal transparency in security posture. It also says that Gartner predicts that by 2026, over 40% of organizations developing cloud-native apps will adopt Application Security Posture Management (ASPM) to unify vulnerability management across the SDLC.
This shift is about more than just working efficiently. It’s about gaining the visibility organizations need to stay secure as threats keep changing. ASPM helps teams stay aligned and ready for new risks. This guide will help you reach that end-state by exploring the top 10 ASPM tools available in the market, detailing their pros, cons, pricing, and best use cases.
For more tips on securing your applications, check out the Plexicus blog.
Why Listen to Us ?
We have hundreds of DevSecOps teams that secure their application, APIs, and infrastructure use Plexicus.
Plexicus is positioned as the first AI-native remediation platform, bringing a unique approach to application security. By combining secret detection, SAST, SCA, and API vulnerability scanning in one comprehensive platform, Plexicus makes it easier to see and manage vulnerabilities effectively. Plexicus builds security products and is trusted by engineering and security teams worldwide.
“Plexicus has become an essential part of our security toolkit. It’s like having an expert security engineer available 24/7” - Jennifer Lee, CTO Quasar Cyber Security.
ASPM Tools Comparison Table
| Tool | Core Capabilities | Strength |
|---|---|---|
| Plexicus ASPM | SAST, SCA, DAST, Secrets, Cloud Config | Unified AI-driven workflow |
| Cycode | ASPM + SCM integration | Deep DevSecOps visibility |
| Apiiro | ASPM + Risk Prioritization | Code-to-cloud context |
| Wiz | ASPM + Cloud Security Posture Mgmt (CSPM) | Full cloud-native visibility |
| ArmorCode | ASPM + Vulnerability orchestration | Great for enterprise workflows |
| Kondukto | ASPM + Security Orchestration | Centralized vulnerability workflow |
| Checkmarx One | ASPM + Developer-centric AppSec platform | Enterprise unified AppSec |
| Aikido Security | SAST + SCA + IaC | Easy setup, all-in-one security |
| Backslash Security | Code-level ASPM for cloud-native apps | Deep code context |
| Legit Security | AI-Native ASPM | Lightweight, automation-focused |
Best ASPM (Application Security Posture Management) Tools to Check to Secure Your Application
1. Plexicus ASPM
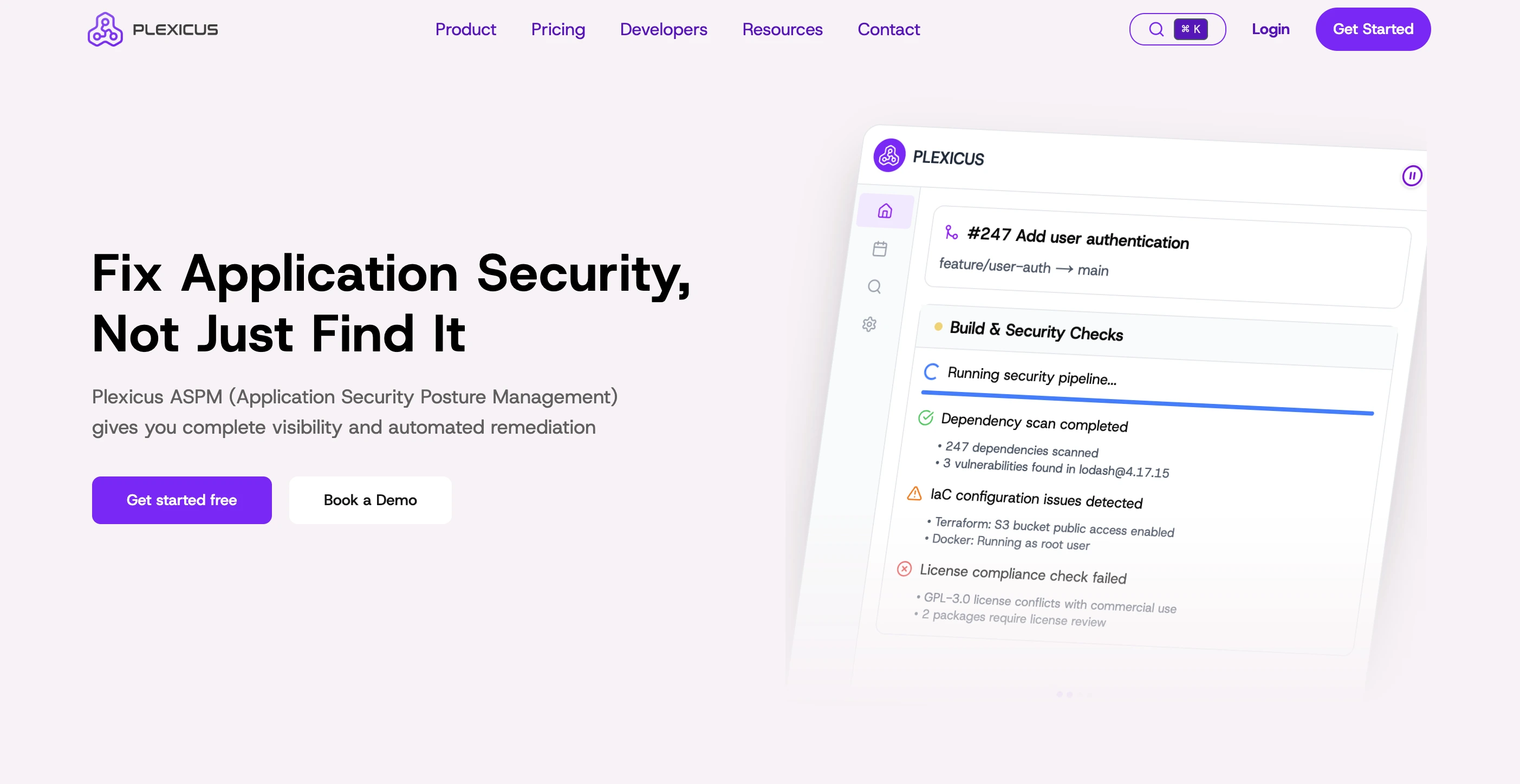
Plexicus ASPM is a unified Application Security Posture Management platform designed to help the devsecops team manage code-to-cloud security efficiently.
Unlike siloed tools, Plexicus unifies SAST, SCA, DAST, secret scanning, API vulnerability scanner, and cloud configuration checks, all within a single workflow.
Plexicus ASPM also provides continuous monitoring, risk prioritization, and automated remediation across your software supply chain. It also integrates with developer tools such as GitHub, GitLab, CI/CD pipelines, and more to allow developers to work easily with their existing tech stack.
Key Features:
- Unified scanning across code, dependencies, infrastructure, and APIs: The platform performs static code analysis, dependency (SCA) scanning, infrastructure-as-code (IaC) checks, secrets detection, and API vulnerability scanning all from one interface.
- AI-Powered Remediation: The “Codex Remedium” agent automatically generates secure code fixes, pull requests, unit tests, and documentation, enabling developers to fix issues with one click.
- Shift-Left Security Integration: Seamlessly integrates with GitHub, GitLab, Bitbucket, and CI/CD pipelines so developers catch vulnerabilities early, before production.
- License Compliance & SBOM Management: Automatically generate and maintain Software Bill of Materials SBOM, enforce license compliance, and detect vulnerable open-source libraries.
- Continuous Vulnerability Solution: Real‐time monitoring and dynamic risk scoring using proprietary algorithms that factor in public data, asset impact, and threat intelligence.
Pros:
- Brings multiple AppSec domains (SAST, SCA, DAST, API, cloud/IaC) into one platform, reducing tool-sprawl and simplifying workflows.
- A developer-first workflow with AI-driven remediation greatly reduces time to fix and dependence on manual security triage.
- It is built for modern software supply chain environments, including microservices, third-party libraries, APIs, and serverless, covering everything from code to deployment.
Cons:
- As a comprehensive platform, mature organisations might need to customise integrations to cover very legacy or specialised systems.
- Because of its broad capability, teams may require slightly more time to ramp up configuration and fully adopt automation workflows.
Pricing:
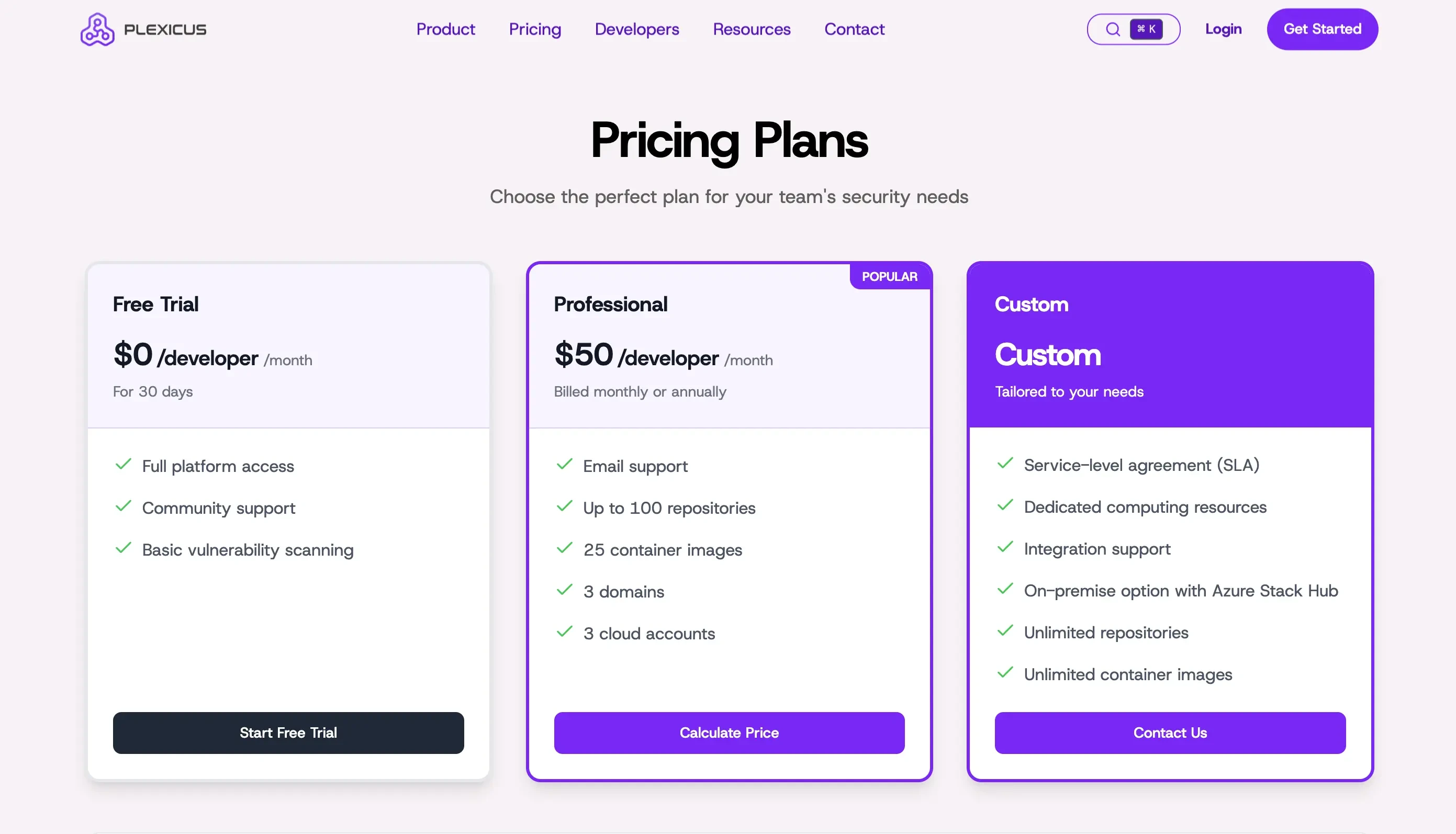
- Free tier available for 30 days
- USD $50/developer
- Custom enterprise pricing (contact Plexicus for a quote)
Best For:
Engineering and security teams that are looking to consolidate their AppSec stack, move away from fragmented tools, automate remediation, and gain unified visibility across code, dependencies, infrastructure, and runtime.
Why It Stands Out:
Most tools only handle one or two tasks, like SCA or API scanning. Plexicus ASPM covers the whole process, from finding issues to fixing them, so developers and security teams can work together. Its AI assistant helps cut down on false positives and speeds up fixes, making it easier for teams to adopt and release updates quickly without losing security.
2. Cycode
Cycode is a mature Application Security Posture Management (ASPM) platform designed to give organizations end-to-end visibility, prioritization, and remediation across their software development lifecycle, from code to cloud.
Key Features:
- Real-time application security posture management that connects code, CI/CD pipelines, build infrastructure, and runtime assets.
- Risk Intelligence Graph (RIG): correlates vulnerabilities, pipeline data, and runtime context to assign risk scores and trace attack paths.
- Native scanning plus ConnectorX architecture: Cycode can use its own scanners (SAST, SCA, IaC, secrets) and ingest findings from 100+ third-party tools.
- Developer-friendly workflow support: integrates with GitHub, GitLab, Bitbucket, Jira, and produces context-rich fix guidance.
Pros:
- Strong for large ‘software factory’ environments, teams with many repositories, CI/CD pipelines, and multiple scanning tools.
- Excellent at risk prioritization and reducing alert noise by tying issues to business-impact and exploitability.
- Designed for modern SecDevOps workflows: reduces hand-off friction between development and security.
Cons:
- Due to its extensive capabilities, the onboarding and configuration may be more involved than simpler tools.
- Pricing and tier details are less publicly transparent (enterprise quote only).
Pricing: Custom quote (enterprise pricing), not publicly listed.
Best for: Mid-to-large enterprises with complex DevSecOps pipelines, many scanning tools already deployed, and a need for unified posture management.
3. Apiiro
Apiiro provides a modern Application Security Posture Management (ASPM) platform that focuses on connecting code, pipelines, and runtime context into one risk-aware system.
Apiiro uses patented Deep Code Analysis (DCA) to build a unified “software graph” that maps code changes to deployed environments. It then uses that context for prioritization and automated remediation.
Key Features:
- Deep inventory of code, open-source dependencies, APIs, and runtime assets via DCA.
- Ingestion of findings from third-party scanners and correlation into one platform for deduplication and prioritization.
- Risk-based remediation workflows that tie vulnerabilities to code owners, business context and runtime impact.
- Integration with both SCM/CI/CD pipelines and IT/ITSM systems (e.g., ServiceNow) for bridging DevSecOps and enterprise response.
Pros:
- Context-rich: By mapping software from code to runtime, Apiiro helps fill the visibility gap that many AppSec teams face.
- Developer-friendly: Integrates into code workflows (SCM, build) to catch issues earlier and provide actionable insight.
- Enterprise scale: Proven traction in large organizations, with a reported 275% growth in new business in 2024 for its ASPM platform.
Cons:
- Enterprise-oriented: Pricing and setup tend to cater to larger organizations; smaller teams may find it more complex.
- Learning curve: Because of its depth and context capabilities, onboarding may require more time and coordination across teams.
Pricing:
- Not publicly listed, custom enterprise pricing required.
Best for:
Organizations that have multiple AppSec tools (SAST, DAST, SCA, secrets, pipelines) and need a unified platform to correlate findings, contextualize risk, and automate prioritization and remediation across the software delivery lifecycle.
4. Wiz
Wiz is a leading application security posture management (ASPM) platform that integrates code, pipelines, cloud infrastructure, and runtime into a unified security graph.
Key Features:
- Code-to-cloud visibility links source code, CI/CD pipelines, cloud resources, and runtime assets into a single inventory.
- Context-driven risk prioritization assesses vulnerabilities based on reachability, exposure, data sensitivity, and attack path potential.
- Unified policy engine and remediation workflows support consistent security rules across code, infrastructure, and runtime.
- Comprehensive third-party scanner ingestion ingests SAST, DAST, SCA results into its Security Graph for correlation.
Pros:
- Strong for cloud-native, hybrid, and multi-cloud environments
- Excellent at operationalizing ASPM across DevSecOps teams
- Reduces alert noise by focusing on exploitable issues rather than just severity
Cons:
- Pricing is generally targeted at enterprise-scale companies.
- Some organisations may find it more focused on cloud/risk-graph than pure SAST pipelines.
Pricing: Custom enterprise quotes
Best for: Organisations seeking code-to-cloud risk visibility with a mature ASPM platform designed for modern, distributed environments.
5. ArmorCode
ArmorCode ASPM Platform is an enterprise-grade Application Security Posture Management (ASPM) platform that unifies findings from applications, infrastructure, cloud, containers, and the software supply chain into a single governance layer. It enables organizations to centralize vulnerability management, correlate risks across tool-chains, and automate remediation workflows.
Key Features:
- Aggregates data across 285+ integrations (apps, infrastructure, cloud) and normalizes over 25-40 billion processed findings.
- AI-driven correlation and remediation, the “Anya” agent supports natural-language queries, deduplication, and action-recommendations.
- Independent governance layer: vendor-agnostic tool ingestion, risk-scoring, workflow orchestration, and executive-level dashboards.
- Software Supply Chain & SBOM support: tracks dependencies, misconfigurations, third-party exposures across build and runtime.
Pros:
- Ideal for large, complex organizations needing broad visibility across code, cloud & infrastructure.
- Powerful automation means fewer false positives and faster remediation cycles for security and development teams.
Cons:
- Onboarding and configuration can be intensive, less suitable for very small teams without mature AppSec practices.
- Pricing is custom / enterprise only; smaller teams may find the entry cost high.
- Because it’s designed as an orchestration/governance layer rather than a single scanner, it depends on your existing tech stack and integration readiness.
Pricing:
- Custom enterprise pricing. No publicly listed fixed tier.
Best for:
Enterprises and security teams that already have multiple scanning tools, complex pipelines or hybrid cloud environments, and require a unified posture management and automation layer to fully align AppSec with DevSecOps and business risk.
6. Kondukto
Kondukto is an enterprise-grade Application Security Posture Management (ASPM) platform that centralizes vulnerability data from across your AppSec toolchain. It enables organizations to unify, orchestrate, and automate their security workflow, moving from tool noise to actionable insights.
Key Features:
- Aggregation and normalization of findings from SAST, SCA, DAST, IaC, containers, and SBOM sources, so all security data lives in one platform.
- Comprehensive integrations and a “Bring Your Own Data” model that supports more than 100 scanners and security tools.
- Robust automation and orchestration workflows: ticket creation, notifications (Slack, Teams, Email), automatic triage and suppression rules.
- SBOM management and risk tracking for open-source components, giving visibility into where vulnerable or unlicensed code lives in your portfolio.
- Role-based dashboards with organizational, product-level, and project-level views, so CISOs, AppSec teams, and developers each see what matters most.
Pros:
- Great for large, complex engineering organisations with many vulnerability scanners and security tools, they get a “single pane of glass” view.
- Strong automation reduces manual triage and helps streamline DevSecOps workflows.
- Flexible architecture: supports cloud or on-prem deployments, making it suitable for hybrid environments.
Cons:
- Implementation and onboarding may require more effort than simpler point-solutions, especially for smaller teams or orgs without a mature AppSec practice.
- Pricing is custom-quote only (not publicly listed), making initial evaluation less transparent.
- Because of its breadth, some features may overlap with existing tools in the stack, so a clear consolidation strategy is needed.
Pricing:
- Custom enterprise pricing (quote-based), not publicly published.
Best for:
Large enterprises or organisations with mature DevSecOps pipelines that are already using multiple AppSec tools and want to unify their vulnerability posture, prioritise risk, automate workflows and embed security across the SDLC.
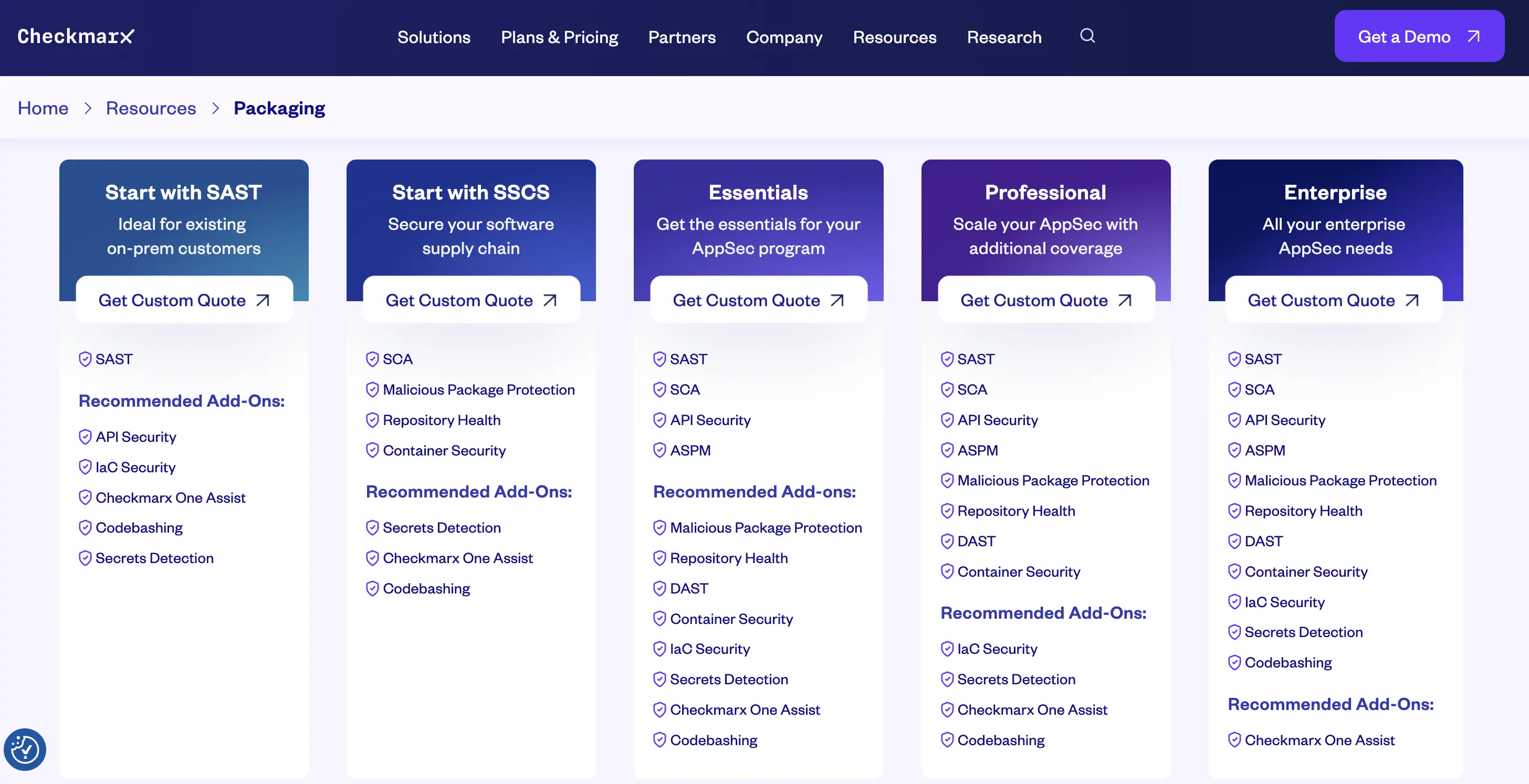
7. Checkmarx One ASPM
Checkmarx One’s ASPM platform delivers enterprise-grade application security posture management by consolidating and correlating data from across your AppSec toolchain, covering SAST, SCA, DAST, API security, IaC, container scanning, and more.
It provides aggregated application risk scores, correlates findings from non-Checkmarx tools via SARIF ingestion, and brings runtime and cloud context into its risk prioritization workflows.
Key Features:
- Application Risk Management: Aggregated risk scores per application, ranked by business impact and exploitability.
- Bring Your Own Results: Ingests external AppSec tools’ output (via SARIF/CLI) so you don’t need to rip and replace your existing scanners.
- Code-to-Cloud Visibility: Captures vulnerability data across pre-production, runtime, and cloud environments.
- Seamless Developer Workflow Integration: Integrated into IDEs, cloud tools, and ticketing systems, and supports 50+ languages and 100+ frameworks.
- Policy and Compliance Engine: Customizable internal policy management helps align AppSec workflows with business & regulatory requirements.
Pros:
- Strong enterprise fit with broad AppSec coverage across multiple domains (code, cloud, supply-chain).
- Advanced integration allowing legacy and modern scanner data to coexist, reducing tool-sprawl.
- Developer-friendly features (IDE plugins, automated risk prioritization) make it easier to scale AppSec across teams.
Cons:
- Pricing is enterprise-custom and not publicly listed; smaller teams may find it cost-prohibitive.
- Broad functionality may introduce setup and integration overhead—teams need AppSec maturity to get full value.
- Some smaller orgs might not need the full breadth of capabilities and may benefit from more streamlined tools.
Pricing:
- Custom enterprise quotes only.
Best for:
Large-scale organizations with mature DevSecOps practices that require a unified, enterprise-ready ASPM platform to manage application security posture across code, cloud, and runtime.
8. Aikido Security
Aikido Security is an all-in-one Application Security Posture Management (ASPM) platform designed especially for startups and mid-sized development teams. It combines SAST, SCA, IaC/configuration scanning, container and cloud posture checks, and secret detection, all from a single interface. According to its website, it targets teams who want “to secure your code, cloud, and runtime in one central system.”
Key Features:
- Unified scanning across code, dependencies, containers, IaC, and cloud resources.
- Developer-friendly workflow with auto-triage and “one-click” remediation suggestions.
- Fast onboarding and lean deployment: integrates with GitHub, GitLab, Bitbucket, Slack, Jira, and much of the CI/CD ecosystem.
- Transparent pricing and free plan: includes code + secrets scanning tools; paid tiers scale with number of repositories, containers, cloud accounts.
Pros:
- Rapid onboarding makes it ideal for smaller teams or fast-moving startups.
- Strong developer UX focuses on reducing noise and enabling fix-first workflows (AutoTriage, GUI integration).
- Affordable pricing with clear tiers and a free plan, making ASPM accessible.
Cons:
- While it covers many AppSec domains, comparably fewer enterprise-grade controls or integrations than legacy platforms.
- Customisation may be more limited for very large enterprises with complex legacy systems.
- Does not always expose the full depth of runtime/cloud risk analytics compared to enterprise-focused solutions.
Pricing:
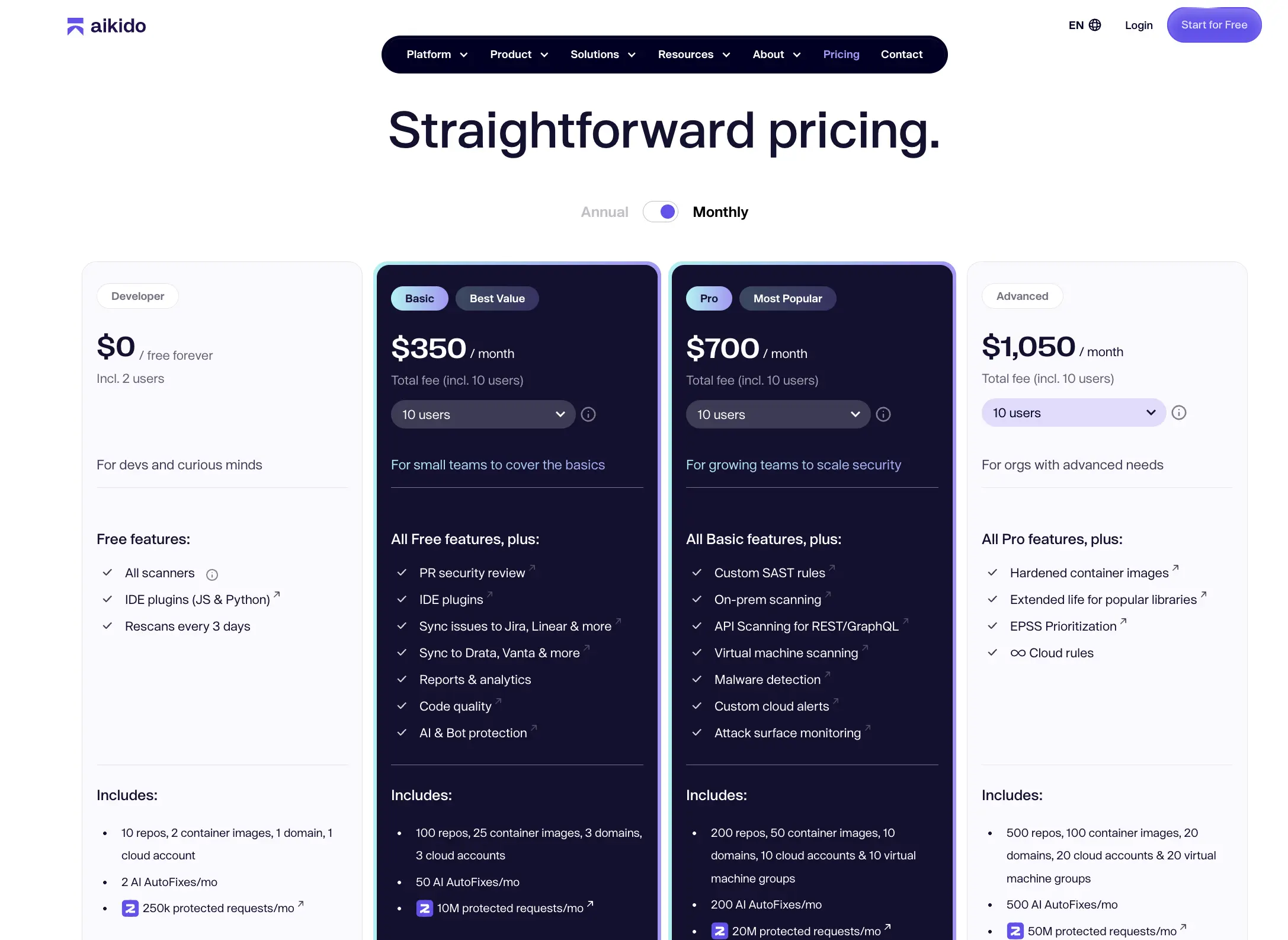
- Free tier available
- Paid plans start at approximately $350/month per user.
Best for:
Startups, scale-ups, and mid-sized DevSecOps teams who want to embed ASPM early, unify their scanning tool-chain, and remediate vulnerabilities quickly without heavy overhead or complex enterprise processes.
9. Backslash Security
Backslash Security offers a powerful ASPM (Application Security Posture Management) platform with a strong emphasis on reachability and exploitability analysis, enabling product-security, AppSec, and engineering teams to uncover critical code flows and high-risk vulnerabilities across code, dependencies, and cloud native contexts.
Their website also highlights a focus on “vibe-coding” and securing AI-driven development ecosystems (IDE agents, prompt rules, AI coding workflows), making it explicitly relevant for teams using Gen-AI / agent-assisted coding.
Key Features:
- In-depth reachability & toxic flow analysis: identifies vulnerabilities that are actually exploitable and reachable rather than surface findings.
- Comprehensive ingestion of findings from SAST, SCA, SBOM, secrets detection, and VEX (Vulnerability Exploitability Exchange).
- Application-centric dashboards with cloud context, linking code-based risk to deployment/runtime posture.
- Automation workflows: assigns issues to the correct developer, includes evidence paths, and integrates with CI/CD/hybrid toolchains.
Pros:
- Excellent for organisations dealing with complex cloud/AI/code pipelines where reachability and context matter more than raw vulnerability counts.
- Designed explicitly for modern development practices (including AI-assisted code / “vibe coding”), ideal when dev teams are using many tools, agents, LLMs, etc.
- Strong prioritisation logic helps reduce alert fatigue and focus effort on high-impact issues.
Cons:
- Because it is oriented toward enterprise-scale and modern development ecosystems, smaller teams or legacy stacks may find the setup more involved.
- Pricing is custom/enterprise-only, so entry-costs may be higher than simpler ASPM tools.
- Some feature sets are very specialised (e.g., “vibe coding security”) and may be overkill for teams not using those workflows.
Pricing:
- Custom enterprise quote only (public pricing not published).
Best for:
Large enterprises, product-security teams, or organisations with mature DevSecOps pipelines and modern development stacks (microservices, open-source heavy, Gen-AI/agent-driven workflows) that need deep contextual ASPM coverage rather than simple scan aggregation.
10. Legit Security
Legit Security is an AI-native Application Security Posture Management (ASPM) platform built for modern software factories. It automates discovery, prioritization, and remediation of AppSec risks across code, dependencies, pipelines, and cloud environments.
Key Features:
- Code-to-Cloud Coverage: Integrates with all systems and AppSec testing tools used in development and deployment to provide a centralized view of vulnerabilities, misconfigurations, secrets, and AI-generated code.
- AppSec Orchestration, Correlation & De-Duplication: Aggregates scan results (SAST, SCA, DAST, secrets) and correlates or deduplicates findings to highlight only those that matter.
- Root Cause Remediation: Identifies single remediation actions that address multiple issues at once, minimizing developer effort and accelerating risk reduction.
- Contextualized Risk Scoring: Uses AI to evaluate business impact, compliance, GenAI code usage, APIs, internet accessibility, and other factors to prioritize fixes that align with business risk.
- AI Discovery & Guardrails: Detects AI-generated code, enforces security guardrails around GenAI usage, and integrates with AI coding assistants—addressing risks from “vibe-coding” workflows.
Pros:
- Excellent for organizations adopting AI/LLM-assisted development or dealing with complex pipelines, dependencies, and modern dev workflows.
- Strong prioritization logic and developer-friendly workflows, reducing alert noise and enabling faster action.
- Supports full software supply-chain visibility, secrets detection, and contextual remediation.
Cons:
- Geared toward medium to large teams, smaller teams may find the platform more comprehensive than necessary.
- Pricing is custom and not public; it may require a higher budget commitment.
- Onboarding and integration may be more involved due to the breadth of coverage and features.
Pricing:
Custom enterprise quotes. Public base tier price not published.
Best for:
DevSecOps teams and product-security organizations that need to embed posture management into modern development workflows (“vibe-coding”), secure AI-generated code, manage complex tool ecosystems, and reduce time from detection to remediation.
Secure Code to Cloud with Plexicus ASPM
ASPM tools are the next leap in Application Security Management, clarifying fragmented AppSec pipelines.
They unify insights, automate response, and provide real-time visibility, transforming security from a reactive cost center to a proactive advantage.
While other ASPM platforms focus on orchestration or enterprise governance, Plexicus ASPM takes a developer-first, AI-driven approach, designed to make AppSec faster, smarter, and easier to adopt.
1. Unified Code-to-Cloud Security in One Platform
Most organizations juggle multiple tools: SAST for code, SCA for dependencies, DAST for runtime, and separate dashboards for secrets or APIs.
Plexicus unifies all of them in one continuous workflow, giving complete visibility across code, dependencies, infrastructure, and runtime.
2. AI-Powered Remediation Engine (“Codex Remedium”)
Instead of stopping at detection, Plexicus helps teams fix vulnerabilities automatically.
The AI agent can generate secure code patches, pull requests, and documentation, cutting mean-time-to-remediate (MTTR) by up to 80%.
3. Built for Developers, Loved by Security Teams
Unlike legacy security platforms that disrupt developer flow, Plexicus integrates seamlessly with GitHub, GitLab, Bitbucket, and CI/CD pipelines.
Developers get actionable fixes inside their workflow, no context-switching, no friction.
4. Real-Time Risk Intelligence
Plexicus brings together threat intelligence, asset exposure, and exploit data to create dynamic risk scores. This helps teams focus on real, exploitable risks instead of just what looks severe in reports.
5. Security that Scales with You
From startups to enterprises, Plexicus offers flexible pricing and deployment options, with a free tier for small teams and enterprise automation for larger orgs.
It grows with your AppSec maturity, not against it.
In short:
Plexicus ASPM helps you cut down on extra tools, fix issues faster with AI, and see everything from code to cloud,all while keeping your developers moving quickly. Start with a quick win: scan one of your repositories in just five minutes to see the power of Plexicus for yourself. Experience seamless integration and immediate insights, and take the first step toward enhancing your application security. Try it free today.
FAQ
1. What is ASPM?
ASPM (Application Security Posture Management) is a unified approach to managing application security findings across the SDLC.
2. How is ASPM different from SAST or SCA?
SAST and SCA focus on scanning specific code aspects, while ASPM unifies results, adds context, and prioritizes remediation.
3. Do I need ASPM if I already use multiple security tools?
Yes. ASPM consolidates fragmented reports and helps prioritize vulnerabilities effectively.
4. Is ASPM only for enterprises?
No, tools like Plexicus make ASPM accessible to startups and SMBs with free SAST and AI-driven automation.