Best API Security Tools in 2025: Protect Your APIs from Vulnerabilities
Discover top API security tools to detect vulnerabilities, stop API attacks, and protect your applications with advanced scanning and testing.

APIs (Application Programming Interfaces) have become the backbone of modern applications, powering everything from mobile apps, web frontends, microservices, and third-party integrations.
As organizations adopt cloud, SaaS, and microservices architectures, the number of exposed APIs keeps growing exponentially. This rapid expansion creates more entry points for attackers, making API security one of the most critical aspects of application protection today.
The consequences are significant; the cost of such breaches is not just theoretical. According to a recent study, the average cost of a data breach resulting from an API vulnerability is estimated to be around $3.92 million.
Imagine a future where your web applications run flawlessly without interruptions from security breaches. Picture your team’s confidence in launching new features, knowing that your APIs are fortified against vulnerabilities. This guide will help you reach that end-state by exploring the top 10 API security scanning tools, detailing their pros, cons, pricing, and best use cases.
Before diving into our recommendations, let’s explore why robust API security tools have become indispensable. For more tips on securing your APIs or web applications, check out the Plexicus blog.
Need API Security Tools to Secure Your Application?
If you use APIs to grow your business, whether for digital adoption, partner integration, or customer access, your applications become more exposed. In these cases, API security tools are vital. Misconfigurations can lead to:
- Data exposure (e.g., leaking customer PII)
- Broken authentication (attackers impersonating users)
- Injection attacks (SQLi, command injection, etc.)
- Business logic abuse (bypassing limits or controls)
The right API security scanning tools can help you detect vulnerabilities early and protect your APIs against attackers.
Why Listen to Us? Before reviewing our top tool picks, here’s why our expertise matters:
We helped hundreds of DevSecOps teams to secure their application, APIs, and infrastructure.
Our Application Security Posture Management (ASPM) platform unifies SAST, SCA, API security, secret detection, and cloud security in one place. Trusted by engineering and security teams worldwide, Plexicus helps organizations save time, reduce false positives, and remediate issues faster with AI-assisted fixes.
Quick Comparison Table
| Tool | Description | Pricing | Best For | Pros | Cons |
|---|---|---|---|---|---|
| Plexicus ASPM | Unified platform covering API, code, dependency, cloud/IaC security with AI-driven remediation. | Custom pricing; $50/dev/month; 30-day free trial | Teams needing all-in-one security (API + code + cloud) | Broad coverage, AI remediation reduces manual work | Complex for API-only needs |
| Salt Security | AI-powered full API lifecycle security focusing on runtime protection and shadow API discovery. | Enterprise only; from $36K to $100K+/year | Large enterprises with runtime and governance needs | Strong runtime threat detection, shadow API identification | Enterprise pricing; setup complexity |
| 42Crunch | End-to-end API security with contract auditing, runtime micro-firewall, developer-centric. | Free tier; paid from $15/user/month; custom enterprise pricing | Dev teams aiming for shift-left API security | Full lifecycle coverage; reduces false positives | Advanced runtime features costlier |
| Akamai API Security | Complete API protection platform from discovery to runtime with global scale. | Custom enterprise pricing | Large enterprises with high-volume APIs | Comprehensive, Gen AI/LLM support | Enterprise pricing; complex deployment |
| Cequence Unified API Protection | API lifecycle security including discovery, compliance, runtime threat detection. | Custom pricing; about $52.5K/year for 5M API calls | Large orgs with complex API ecosystems and compliance | Full lifecycle, shadow API detection | Expensive; significant deployment effort |
| Traceable API Security | AI/ML-powered API security with posture management, contextual testing, runtime defense. | Custom pricing; $20K-$70K/month tiers | Large orgs with extensive, high-traffic API estates | Behavioral analytics, AI-driven detection | High cost; complex setup |
| Wallarm | Cloud-native API security covering discovery, testing, runtime protection. | Free tier; enterprise from ~$50K/year | Large or enterprise organizations with diverse APIs | Supports modern protocols, scalable | Enterprise pricing, complex setup |
| Imperva API Security | API discovery, classification, risk-based enforcement, runtime monitoring integrated with WAF. | Custom pricing; enterprise focus | Regulated industries with large, complex APIs | Deep integration with WAAP/WAF, flexible deployment | Setup complexity; less focus on shift-left testing |
| APIsec | Automated API vulnerability testing focused on logic flaws, integrated into CI/CD. | Free tier; $650-$2,600/month | Dev/mid-sized teams needing shift-left testing | Strong logic flaw detection, developer friendly | Limited runtime protection |
| Akto API Security | Continuous discovery, testing, runtime posture monitoring, CI/CD integration. | Free tier; plans from $990-$6,990/month | DevSecOps and mid-sized teams needing continuous posture | Broad API protocol support, developer friendly | Less enterprise runtime analytics, newer vendor |
1. Plexicus
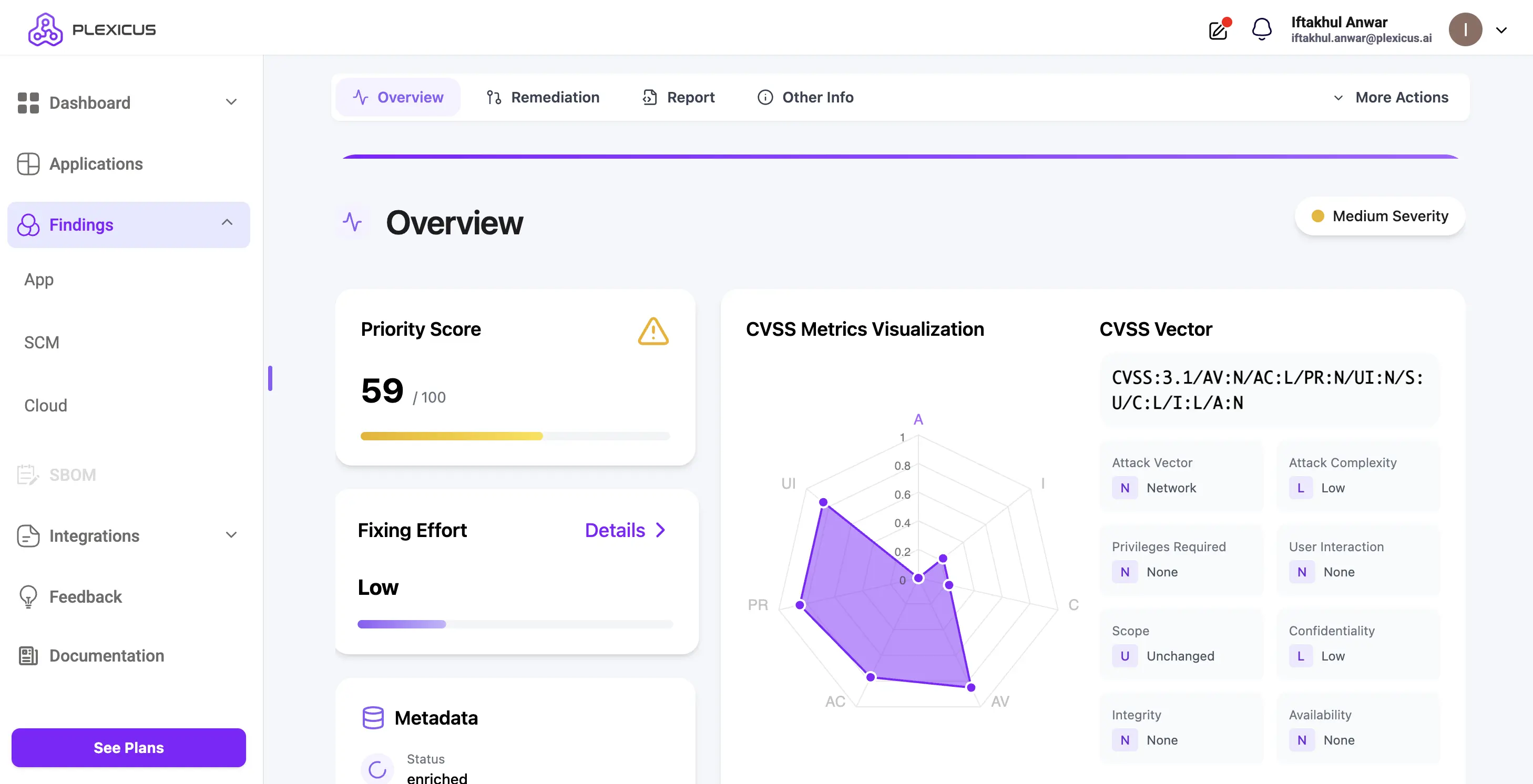
Comprehensive Security in One Platform, Plexicus ASPM is not just a simple API or SCA tool; it’s an Application Security Posture Management (ASPM) platform that unifies multiple security disciplines under one roof. It delivers unified visibility across code, dependencies, infrastructure, and APIs, and then leverages an AI-powered remediation engine to help your team fix vulnerabilities automatically, rather than just flag them.
Key Features:
- AI-Powered Remediation: The platform generates secure code fixes, unit tests, and documentation to automate the fix process.
- Unified Analysis: Static Code Analysis (SAST), Secrets Detection, Dependency (SCA) scanning, Infrastructure-as-Code (IaC) security, and API Vulnerability Scanning all in one platform.
- API Vulnerability Scanner: Specifically highlights discovering, analyzing, and protecting API endpoints against common attack vectors.
- Easy Integration: Built to plug into existing workflows (GitHub, GitLab, Bitbucket, AWS, CI/CD pipelines) with minimal disruption.
Pros:
- A truly unified platform, combining API vulnerability testing, application code security, supply-chain (SCA) scanning, and cloud/IaC security in one solution
- AI-driven remediation reduces manual work, speeds up fixes, and lowers developer overhead.
- Ideal for teams that want coverage from development to runtime, helping you catch issues early and manage risks throughout the application lifecycle.
- Affordable enough compared to other enterprise-oriented platforms
Cons:
- The breadth of coverage means it may feel more complex than a simple API scanner for teams with only one concern.
Price:
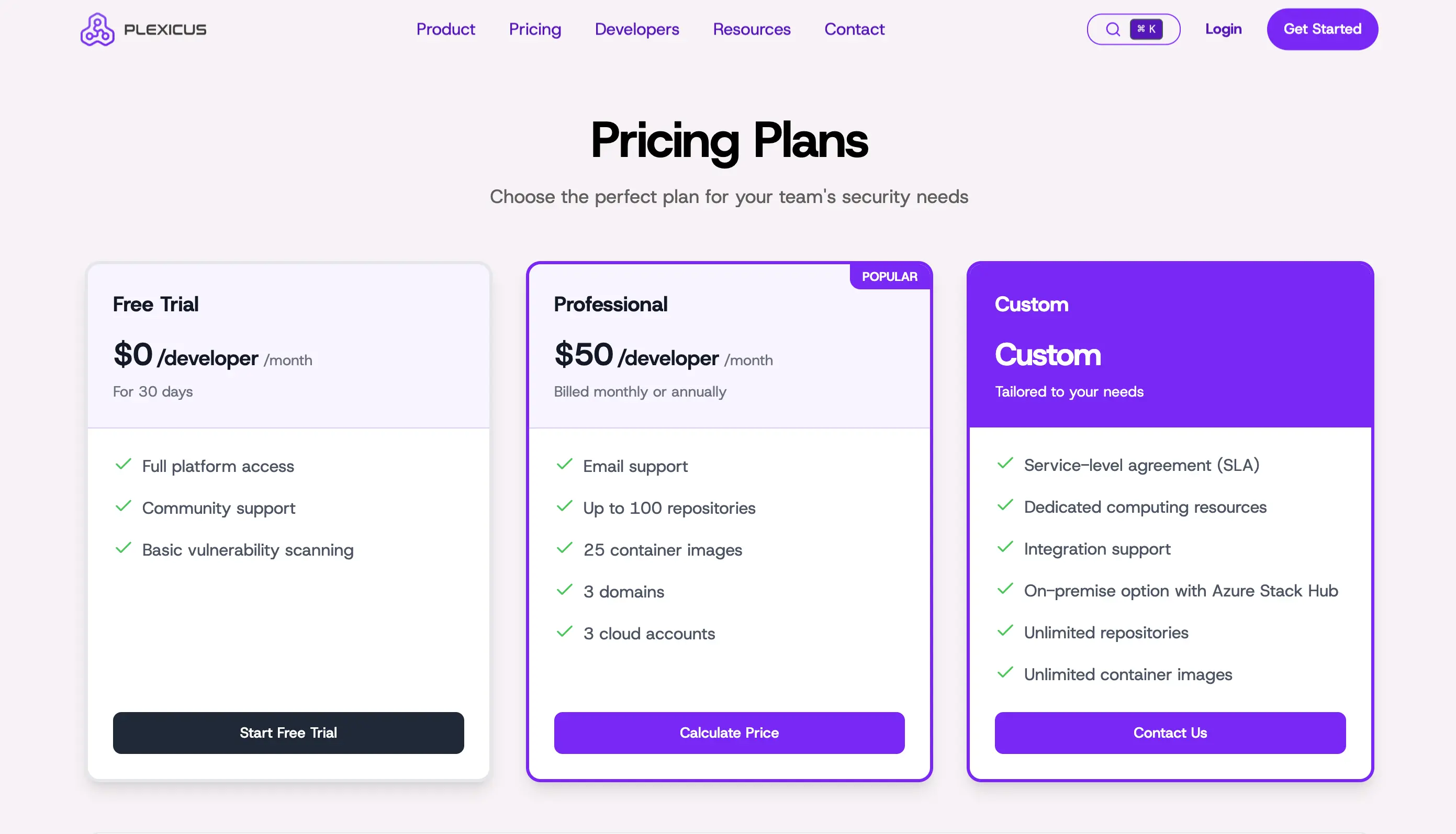
- Free trial for 30 days
- USD $50/developer
- Custom enterprise pricing (contact Plexicus for a quote)
Best for:
- Security and development teams looking for a single, scalable platform that unifies API scanning, application code security, dependency analysis, and cloud/IaC posture management
2. Salt Security
Salt Security offers an AI-infused solution built for the full API lifecycle, helping you secure APIs from discovery to runtime threat protection. Its platform is designed to identify all APIs (including shadow and zombie APIs), uncover sensitive data paths, detect business logic attacks, and enforce API posture and governance across modern applications.
Key Features:
- API discovery: automatically map internal, external, and third-party APIs, including those not managed by gateways.
- Runtime anomaly detection: AI/ML models monitor API traffic and detect behavioral attacks like BOLA (Broken Object Level Authorization) and logic abuse.
- Posture & compliance management: Track sensitive data in motion, enforce policies, and meet standards like PCI, HIPAA, and GDPR.
- Shadow/zombie API risk reduction: Identify and eliminate undiscovered APIs that may introduce risk.
- Cloud-scale deployment: Designed to scale with high API volumes and integrates with major cloud providers like AWS.
Pros:
- Excellent coverage of runtime API threats and behavioral attacks, not just standard vulnerability scanning.
- Strong visibility into hidden APIs and unmonitored endpoints.
- Positioned for large enterprises and complex API environments.
Cons:
- Pricing is not publicly transparent, primarily for enterprise-level contracts.
- Set up and tuning required for high-volume traffic and complex integrations.
- Less focused on early “shift-left” API security testing compared to some developer-centric tools.
Price:
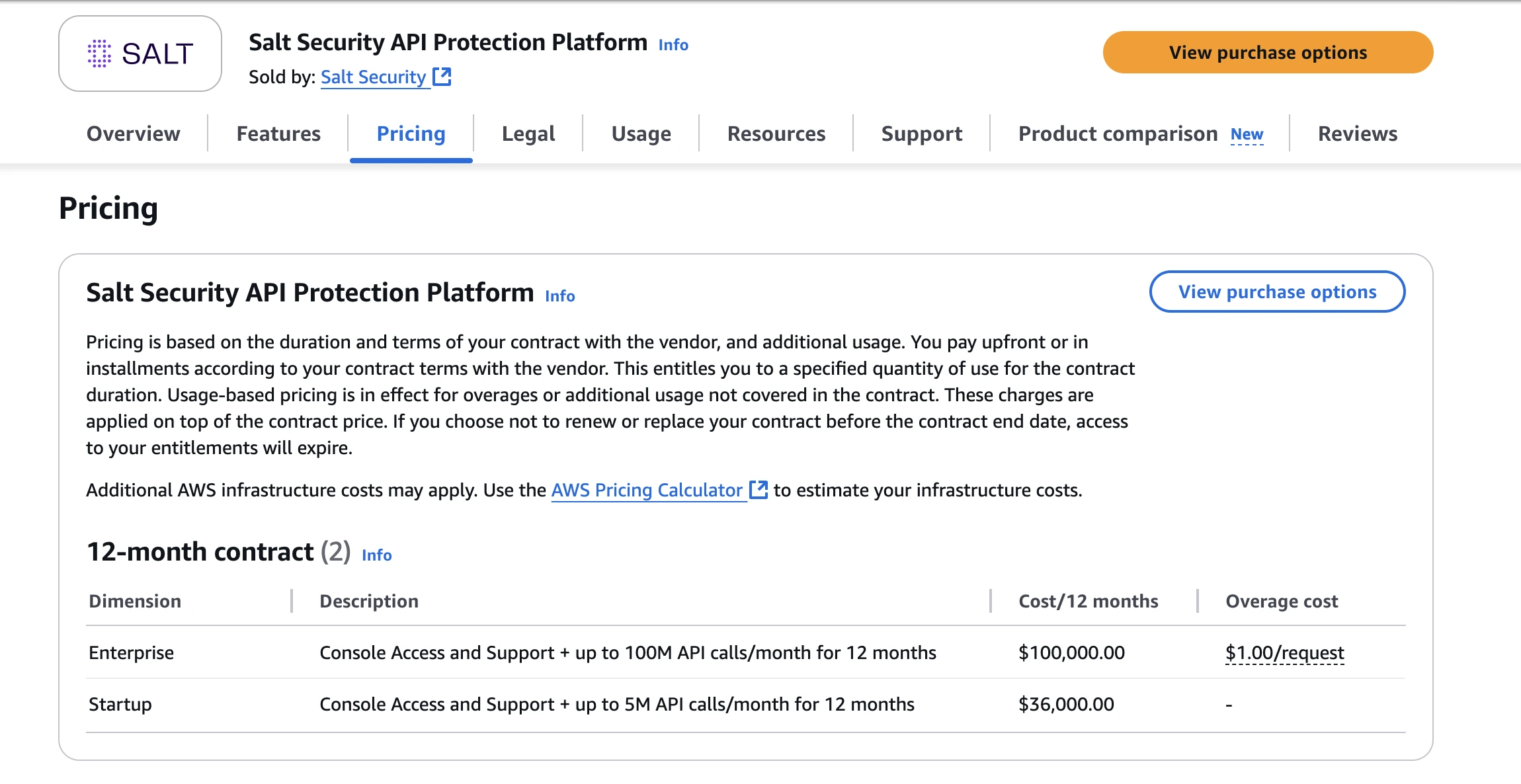
- Enterprise only (custom contract).
- Mention from AWS Marketplace:
- US$36,000/year for up to 5 M API calls/month;
- US$100,000/year for up to 100 M API calls/month.
Best for:
Large organizations with extensive API attacks, high traffic volumes, or shadow API issues. Ideal for teams needing runtime monitoring and governance across cloud-native ecosystems.
3. 42Crunch
42Crunch is an end-to-end API-security platform that help you to secure your application from design to runtime. It combines API security testing, contract validation, and runtime protection. It enables organizations to embed security into the API lifecycle via IDE and CI/CD integrations, while enforcing governance through OpenAPI/Swagger-driven policies.
Key Features:
- API contract auditing (OpenAPI/Swagger) with 300+ security checks.
- Conformance scanning of live endpoints for vulnerabilities and deviation from specifications.
- Runtime API micro-firewall (“API Protect”) enforcing a whitelist model from contract definitions, detecting shadow/zombie APIs.
- Developer-centric integrations: IDE extensions (VS Code, IntelliJ, Eclipse) and CI/CD workflows.
- Governance & API inventory: Automatically discover APIs, catalog them, and enforce policies across distributed teams.
Pros:
- Strong “shift-left” capabilities via contract auditing + developer tools
- Covers full lifecycle: development → deployment → runtime
- Reduces false positives thanks to contract-based enforcement
- Suitable for enterprises with heavy API usage
Cons:
- Some runtime protection features in higher tiers (micro-firewall, full enforcement) may require a larger investment.
- Single‐user or small team tiers may offer limited endpoint/scan volumes.
- For smaller/less mature API teams, the breadth of features might be more than needed.
Price:
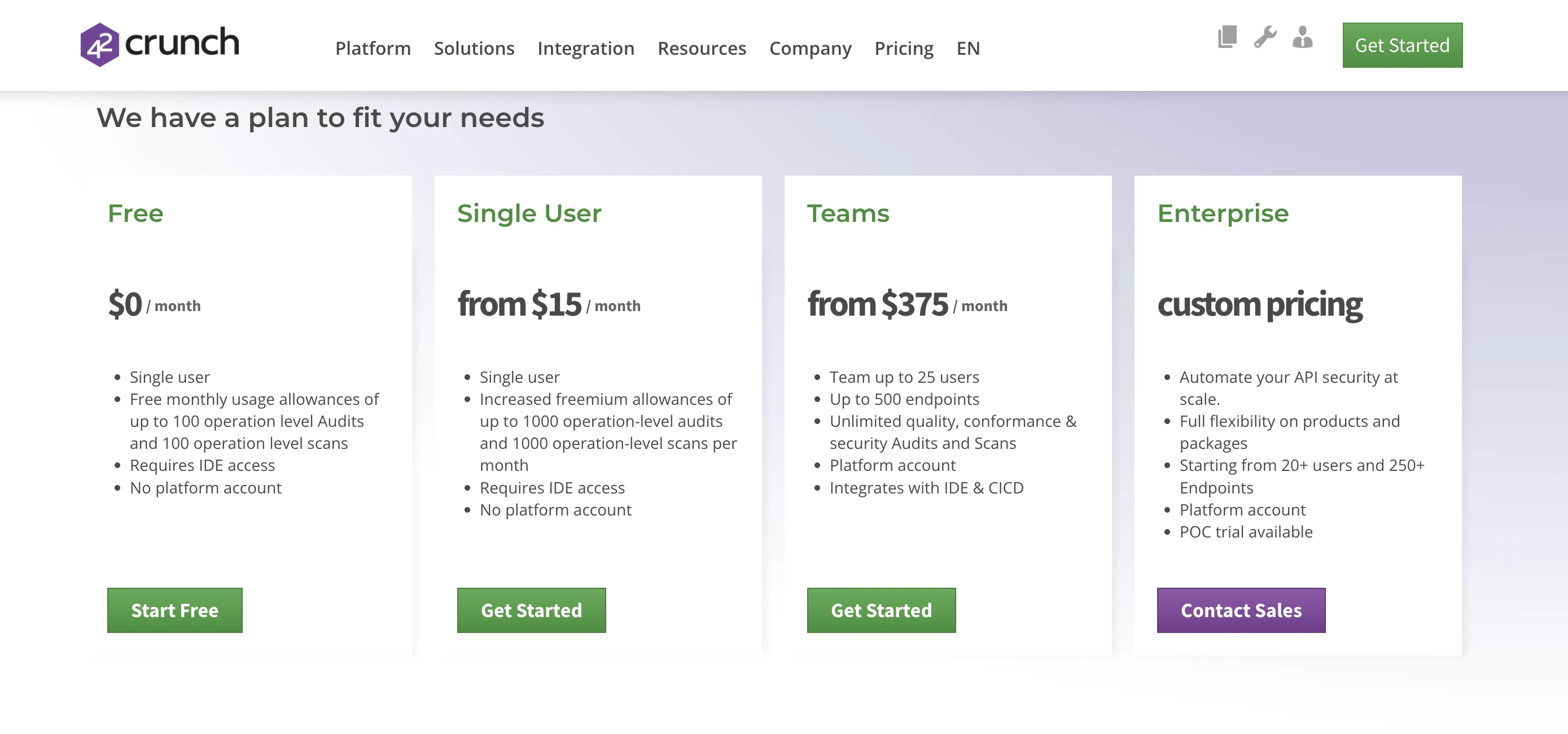
- Free tier: $0/month for a single user, with up to 100 operation audits and 100 operation scans per month.
- Single User Paid Tier: Starting at ~$15/month (per user) for increased usage.
- Team Tier: From ~$375/month (up to ~25 users and ~500 endpoints).
- Enterprise Tier: Custom pricing for larger usage, full-scale deployment.
Best for:
Development teams and enterprises that want a comprehensive API security solution with strong developer workflow integration and robust runtime enforcement of API contracts.
4. Akamai API Security
Akamai API security is an end-to-end API protection platform that helps you secure your APIs from discovery, testing, runtime monitoring, and remediation.
It helps organizations discover and inventory all APIs, including legacy, shadow, and AI/LLM, then evaluate vulnerabilities, monitor live traffic behavior to find anomalies, and enable an automated response workflow to secure your APIs
Key Features:
- Automatic discovery and classification of APIs, including shadow or zombie endpoints.
- Vulnerability scanning and misconfiguration audits aligned with OWASP API Top-10.
- Runtime behavioral and anomaly monitoring for API abuse, business-logic attacks, and data exfiltration.
- Integration into CI/CD pipelines for shift-left testing as well as runtime protection through connectors and edge services.
- Platform-agnostic deployment (cloud, hybrid, on-prem), with seamless integration into existing API gateways, CDNs, and WAAP solutions.
Pros:
- Comprehensive solution: from API design/testing to discovery and runtime security.
- Enterprise-grade with global scale and a strong track record for high-traffic, mission-critical APIs.
- Designed to address modern threats, including Gen AI/LLM endpoints, business logic abuse, and shadow API attack surfaces.
Cons:
- Pricing is enterprise-only and not publicly transparent, which may place it out of reach for smaller teams or early-stage startups.
- Deployment and tuning can require significant effort for large, complex API environments.
- More focused on runtime and enterprise portfolio than lightweight shift-left testing for small teams.
Price:
- Custom pricing (contact Akamai for a quote)
Best for:
Large enterprises and organizations with extensive API ecosystems (including partner/public APIs, Gen AI/LLM integrations, shadow APIs, and high volumes of API traffic) that require 24/7 monitoring, discovery, and advanced protection.
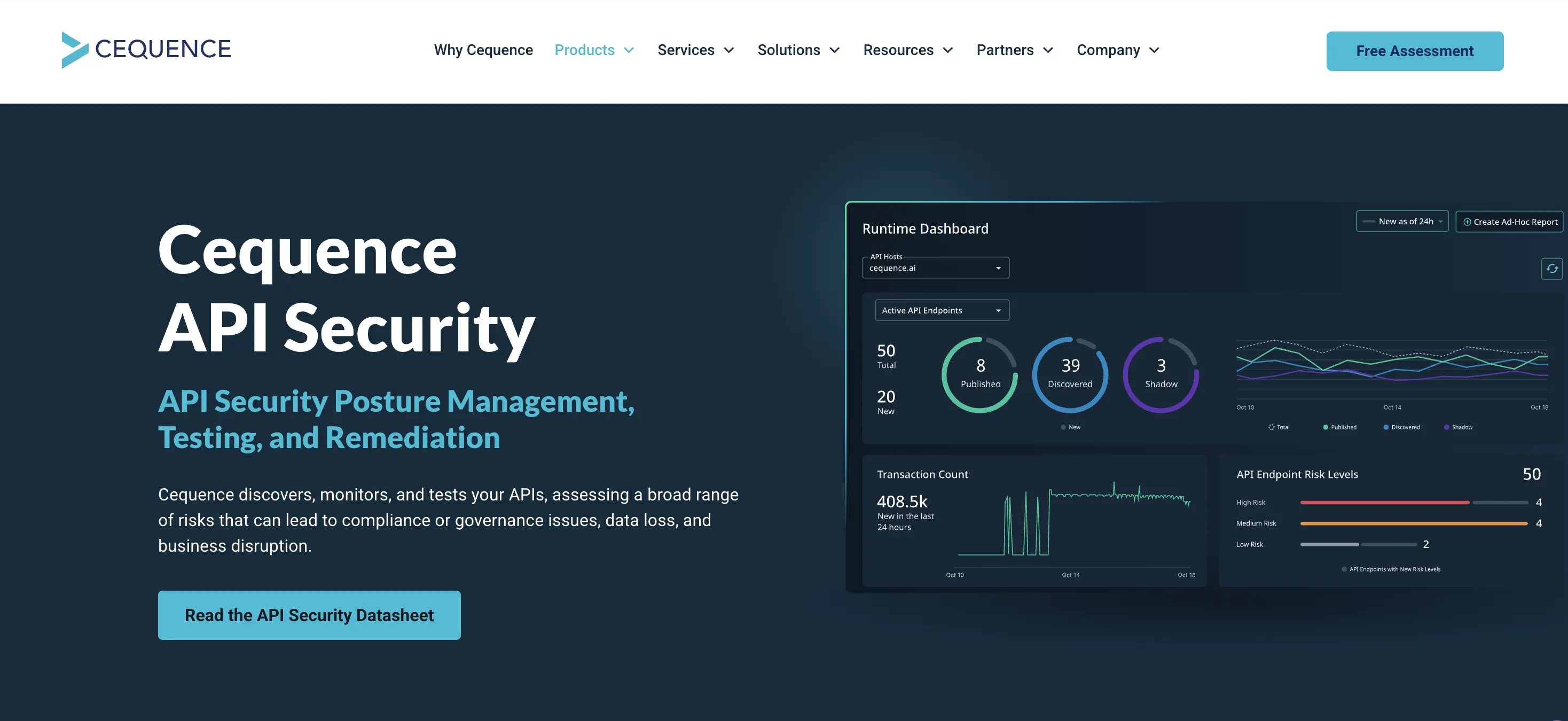
5. Cequence Unified API Protection
Cequence Unified API Protection is a platform that spans the full API lifecycle, discovery, compliance/testing, and runtime protection. Help your organization to protect APIs from attacks, fraud, and business-logic abuse.
Key Features:
- API discovery & inventory: Automatically find internal, external, undocumented (“shadow”) APIs and generate specifications if missing.
- API security testing: Enables pre-production testing of APIs for vulnerabilities (e.g., misconfigurations, coding errors) and can integrate into CI/CD.
- Runtime threat detection & protection: Uses ML/behavioural analysis to identify business-logic abuse, credential stuffing, data exfiltration, and can apply blocking, rate-limiting, or deception responses.
- Compliance & governance: Monitors APIs against internal policies and regulatory frameworks (e.g., PCI, GDPR) and provides API risk classification.
- Flexible deployment: SaaS, on-premise, hybrid; minimal instrumentation required to deploy; can scale to protect billions of API calls per day.
Pros:
- Covers every phase of the API security lifecycle (design, test, runtime) rather than only one segment.
- Strong at detecting hidden risks like shadow APIs and abuse of legitimate endpoints.
- Enterprise-grade scale and flexibility with multiple deployment models.
Cons:
- Pricing is not publicly detailed, primarily for enterprise contracts, which may be costly for smaller teams.
- Initial setup and tuning may require significant effort, especially for complex API ecosystems.
- For teams focused solely on pre-deployment API testing, some features may be more than needed.
Price:
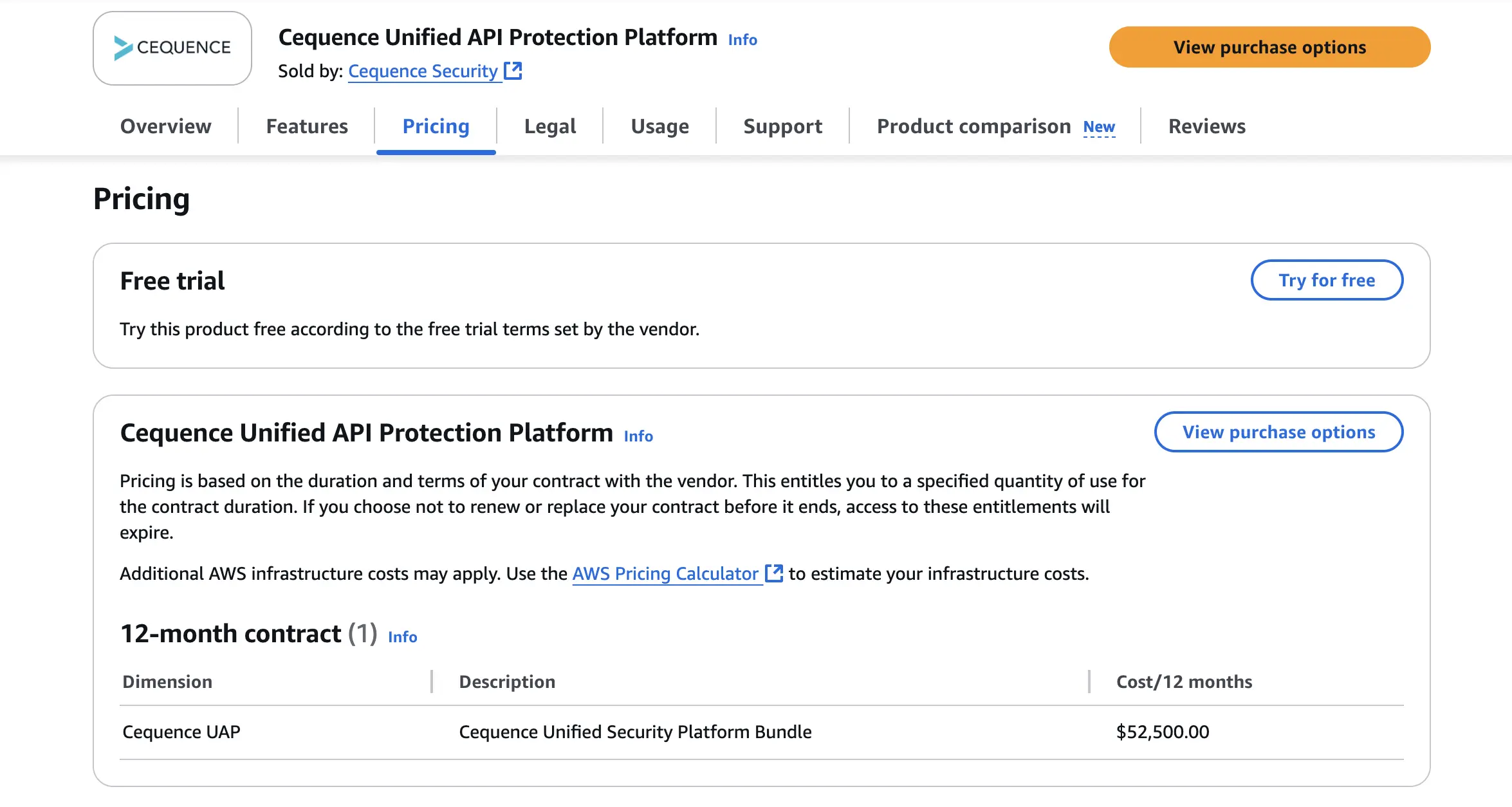
- Custom enterprise pricing;
- The AWS Marketplace listing shows about US $52,500/year for a 12-month contract covering up to 5 million API calls/month.
Best for:
Large organizations with complex API ecosystems, public, partner, internal-facing heavy traffic, bot/API abuse, shadow API risks, or regulated requirements that demand full-lifecycle API security protection.
6. Traceable API Security Platform
Traceable is an enterprise-grade API security platform that spans the entire API lifecycle, from discovery and posture management, through pre-production testing, to runtime threat detection and protection. It gives organizations full visibility into their API landscape (including internal, partner, shadow, and third-party APIs) and then uses context-aware AI/ML analytics to detect anomalies, expose data flows, and block abuse.

Key Features:
- API Discovery & Inventory: Automatically discover all APIs, public, internal, undocumented, partner-facing, and build a full catalog of the API estate.
- API Posture Management: Assign risk scores to APIs based on exposure, data sensitivity, traffic patterns and known vulnerabilities.
- Contextual API Security Testing: Use real traffic data (without requiring spec files) to test for vulnerabilities before production and reduce false positives.
- Runtime Threat Detection & Protection: Monitor API activity, detect patterns of abuse (business logic attacks, data exfiltration, bot/API fraud), and block threats in real time.
- Generative AI & Shadow API Protection: Includes capabilities to protect generative-AI/API integrations and discover “shadow” or “ghost” endpoints that lack governance.
Pros:
- Comprehensive coverage: from design/testing to runtime protection, not just a single slice of API security.
- Deep contextual analytics: learns API behavior & data flows to differentiate true threats from noise.
- Enterprise-scale: built for large API estates with hybrid cloud/on-prem deployments.
Cons:
- Pricing is enterprise-only and custom, and may be out of reach for smaller teams.
- Complex setup: full benefit requires proper deployment, traffic capture, or agent integration, which may add time/effort.
- Developer-centric shift-left testing may be less mature compared to tools built purely for API developers.
Price:
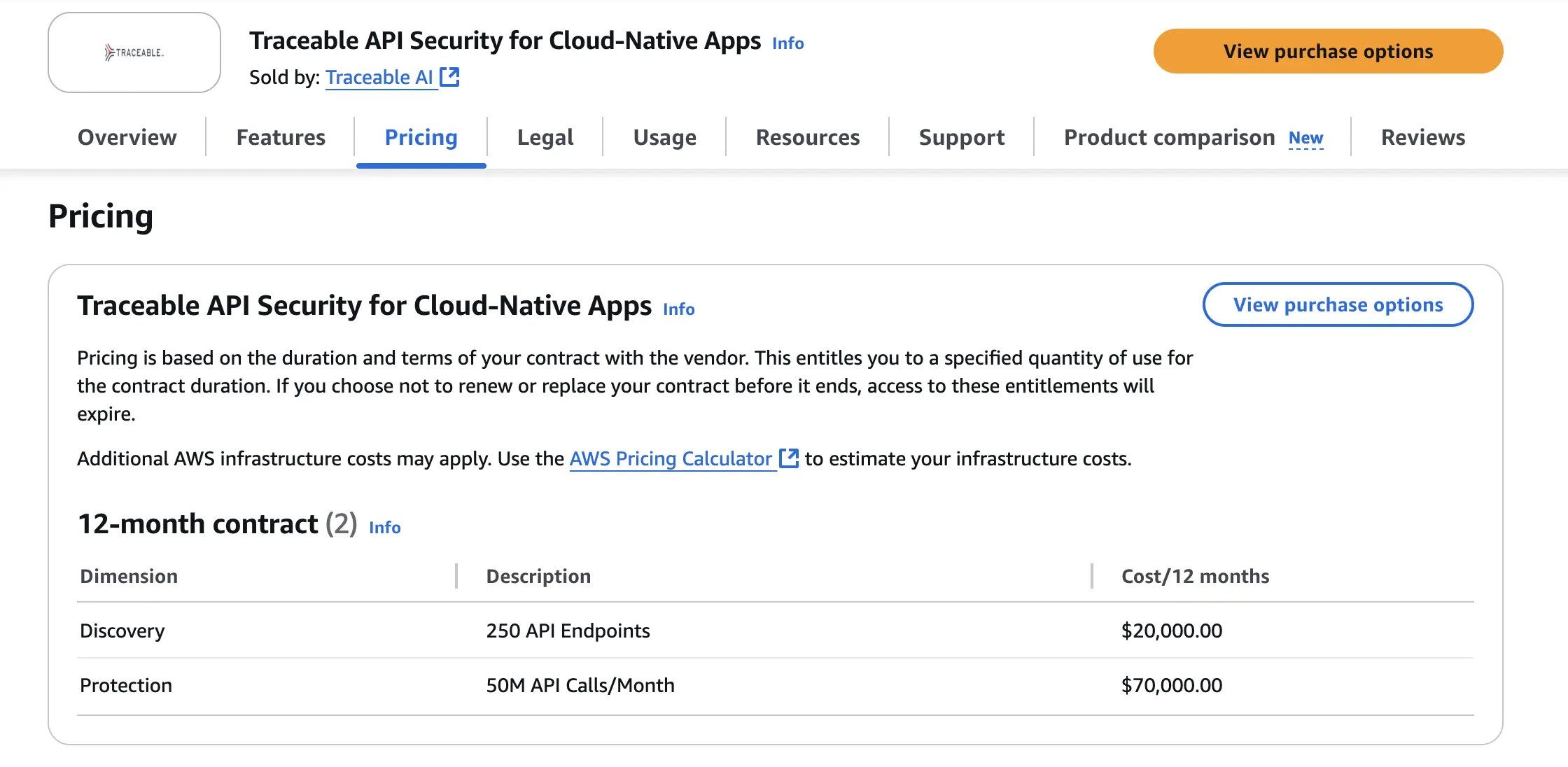
- Custom enterprise licensing; contact the vendor for a quote.
- USD $20,000/month for discovery, limited to 250 API Endpoints
- USD $70,000/month for protection, limited to 50M API calls/month
Best for:
Large organizations with extensive, high-traffic API ecosystems, especially those dealing with partner APIs, internal microservices, generative AI endpoints, and needing full-lifecycle support (discovery → testing → runtime).
7. Wallarm API Security Platform
Wallarm offers a unified API security platform that spans from discovery, testing, to runtime protection of APIs, microservices, and AI-driven endpoints. It’s designed for modern, cloud-native architectures and supports REST, GraphQL, gRPC, and WebSockets across hybrid and multi-cloud environments.
Key Features:
- API Discovery & Inventory: Automatically identify public, private, and undocumented (shadow/zombie) APIs with ongoing traffic-based updates.
- Runtime Threat Detection & Protection: Uses ML/behavioral analytics to detect business-logic abuse, bot/API attacks, OWASP API Top 10 threats, and provides real-time blocking.
- API Security Testing: Integrates into CI/CD pipelines, automates security scans of APIs and agents, and performs vulnerability testing both in development and production.
- Multi-Environment Deployment: Supports inline edge deployment, sidecar proxies, hybrid clouds including AWS, GCP, Azure, Kubernetes, and on-premises data centers.
- Free Tier & Usage Based Pricing: Free tier supports up to 500 K requests/month, including full features for select protocols; enterprise contracts scale to hundreds of millions of requests.
Pros:
- Comprehensive API security coverage: design, testing, runtime, and monitoring.
- Scales to large enterprise API portfolios with complex traffic patterns.
- Deployment flexibility and strong support for modern protocols (GraphQL, gRPC).
Cons:
- Pricing is primarily enterprise-level and not transparent for SMBs.
- Implementation and tuning may require significant effort for complex environments.
- Might offer more capability than needed for small teams focused only on pre-deployment API tests.
Price:
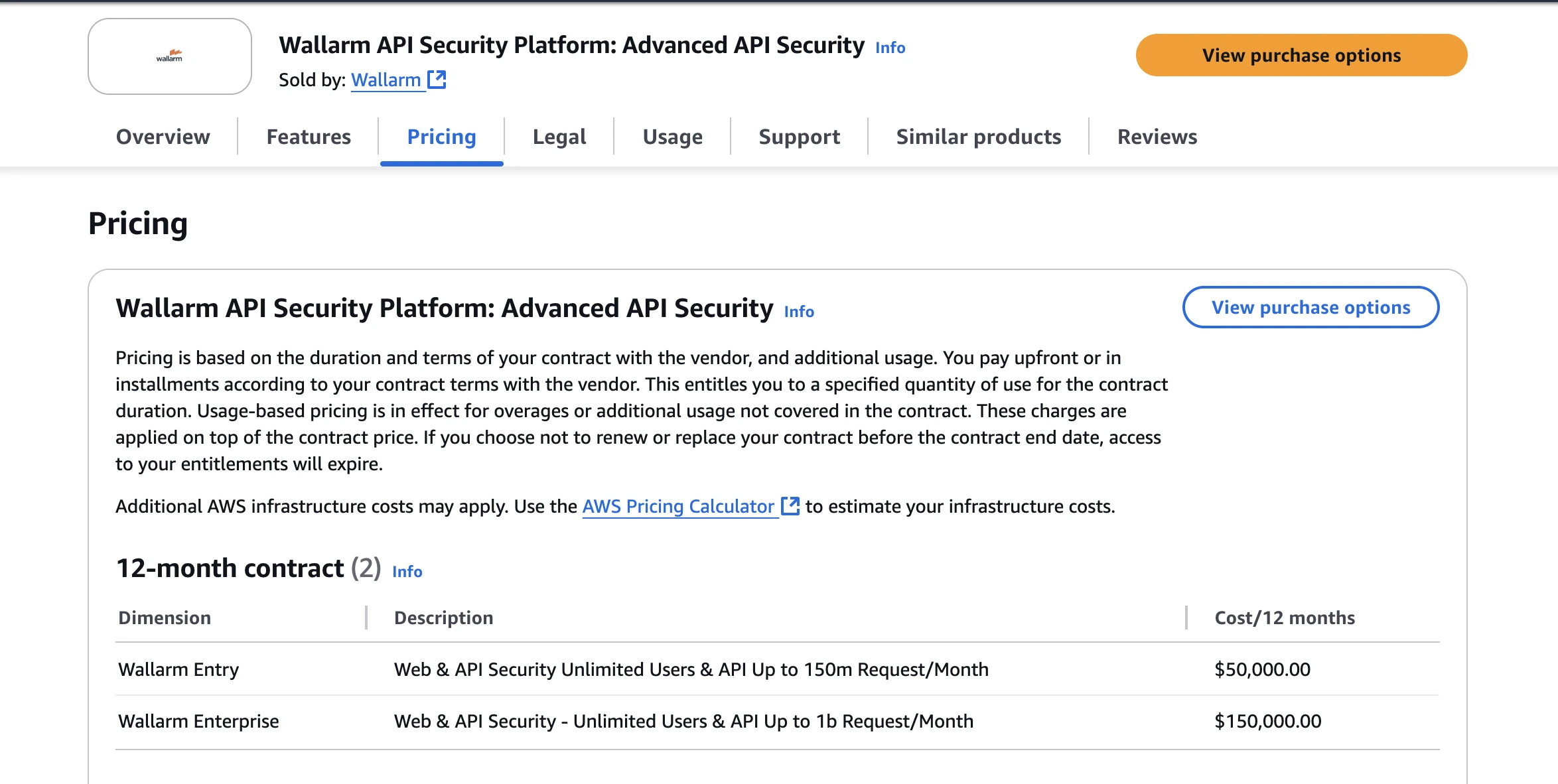
- Free tier: up to 500K requests/month with core features.
- Entry enterprise tier: e.g., ~$50,000/year for up to ~150 million requests/month per AWS Marketplace listing.
- Median contract value based on 24 real purchases: ~$90,000/month-year.
Best for:
Large or enterprise organizations with extensive API ecosystems (public, partner, internal), high-volume traffic, and a need for full-lifecycle API protection, including discovery, runtime defense, and DevSecOps integration.
8. Imperva API Security
Imperva API Security provides end-to-end protection for public, private, and shadow APIs. It offers continuous visibility into the full API estate, automatically discovering and classifying endpoints, while enforcing risk-based policies and monitoring live API traffic to detect and block threats.
Key Features:
- API Discovery & Classification: Automatically identify all APIs (including undocumented ones) across microservices, gateways, and cloud environments.
- Risk-Based API Inventory: Classify APIs by sensitivity, exposure, and usage, enabling prioritised protection.
- Contract & Schema Enforcement: Ensure that API traffic aligns with declared specifications (OpenAPI/Swagger) and block unexpected endpoints.
- Runtime Traffic Monitoring & Threat Analytics: Continuously monitor API calls, detect anomalies and abuse (e.g., data exfiltration, business logic misuse), and integrate with WAAP/WAF.
- Flexible Deployment Options: Available as cloud-managed or self-managed, compatible with major API gateways (Kong, Azure APIM, Apigee), and supports sidecar/agent deployment for hybrid/edge environments.
Pros:
- Offers enterprise-grade API protection covering discovery → risk assessment → runtime defense.
- Deep integration with Imperva’s broader WAAP/WAF ecosystem for unified web & API protection.
- Flexibility in deployment (cloud or on-prem) suits regulated or hybrid environments.
Cons:
- Pricing is not publicly listed, targeted at enterprise deployments with potentially a high budget.
- High complexity: Setup and tuning (especially for traffic monitoring and schema enforcement) may require a strong security/programming team.
- Shift-left or developer-centric “pre-deployment” testing capabilities are less emphasized compared to developer-first tools.
Price:
- Custom enterprise pricing (contact sales)
- Available as an add-on to Imperva Cloud WAF (Web Application Firewall) or as a standalone
Best for:
Large organisations or regulated industries with expansive API estates (including public partner APIs, internal microservices, and third-party/integration APIs) that require full-lifecycle visibility, risk-based enforcement, and production-grade runtime protection.
9. APIsec
APIsec is a dedicated API-security testing platform specializing in automated vulnerability discovery and testing of APIs. It focuses on uncovering logic-based flaws, broken authorizations, and API misuse beyond standard vulnerability scanning. The platform is designed for integration into CI/CD pipelines and supports continuous testing of API endpoints.
Key Features:
- Automated generation of thousands of test cases tailored to a given API architecture (via scanner containers) to find vulnerabilities.
- Full coverage of the OWASP API Security Top 10 risks, including business-logic flaws (e.g., BOLA, mass assignment).
- Continuous testing integration: Runs scans as part of CI/CD, auto-generates tickets for findings, and provides detailed reports for dev/security teams.
- Supports API endpoint specs (OpenAPI/Swagger, Postman collections) and offers free demo/assessment options.
- Developer-friendly onboarding and dashboard for visibility into API security posture. Reviewers note its ease of integration.
Pros:
- Focused purely on API-security testing, delivers depth in API logic-flaw detection.
- Strong integration with DevSecOps pipelines: ideal for teams wanting shift-left API security.
- Transparent pricing tiers at lower usage levels, helping smaller teams evaluate without an enterprise cost barrier.
Cons:
- Scope is narrower than full lifecycle API security platforms — focuses mostly on testing, less on runtime protection or discovery of shadow APIs.
- Steep learning curve for advanced configuration.
- It may lack some enterprise-scale features (runtime anomaly monitoring, large API traffic management) when compared to larger vendors.
Price:
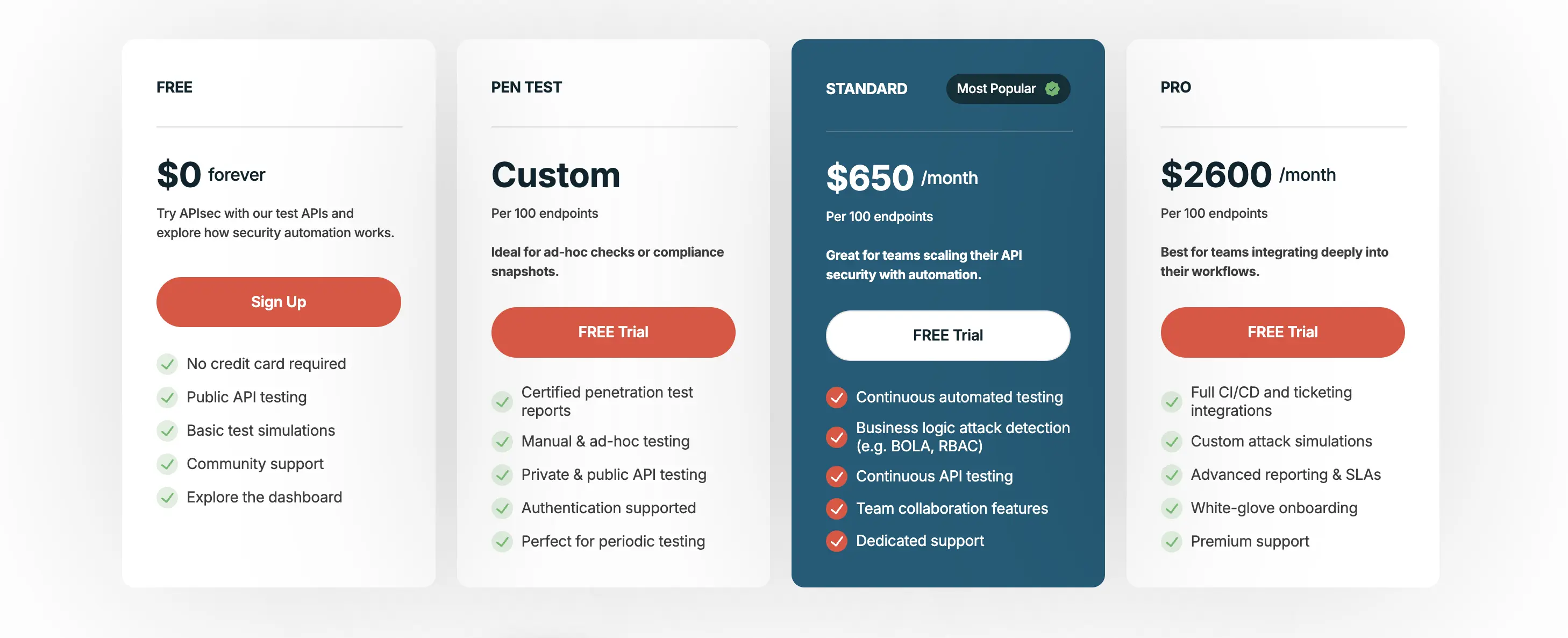
- Free tier: Free for basic usage.
- Standard Edition: US$650/month per 100 endpoints
- Pro Edition: US$2,600/month per 100 endpoints
Best for:
Development and mid-sized security teams that want robust API vulnerability scanning and logic-flaw detection embedded into CI/CD, without needing full-scale enterprise runtime API-protection infrastructure.
10. Akto API Security Tool
Akto is a modern API security platform built for teams who want to integrate vulnerability detection throughout the API lifecycle, from discovery and testing to runtime posture monitoring. It focuses on continuous API inventory, automated tests, and CI/CD workflow integration.
Key Features:
- API Discovery & Inventory: Automatically discovers public, private, internal, and partner APIs (including shadow or zombie APIs) using 50+ traffic and code connectors.
- Continuous API Security Testing: Uses a large library (1000+ tests) to detect OWASP API Top 10 risks, broken auth, business logic flaws, etc., integrated into CI/CD.
- Runtime API Posture Monitoring: Tracks exposed APIs, misconfigurations, sensitive-data exposure, and risk scoring based on traffic patterns and vulnerabilities.
- DevSecOps Integration: Easily integrates with your development pipelines, supports REST, GraphQL, gRPC, and SOAP, and supports both shift-left and runtime testing.
Pros:
- Enables broad API-security coverage (discovery + testing + posture) rather than just one slice.
- Developer and CI/CD friendly: good fit for teams that want to embed API security early.
- Transparent emphasis on modern API types (GraphQL, gRPC) and business logic flaws.
Cons:
- Less emphasis on large-scale enterprise runtime analytics compared to the highest-tier vendors.
- Pricing and tiers may require a quote or custom contract for high-volume usage.
- As a relative newcomer, fewer large legacy enterprise references compared to bigger vendors.
Price:
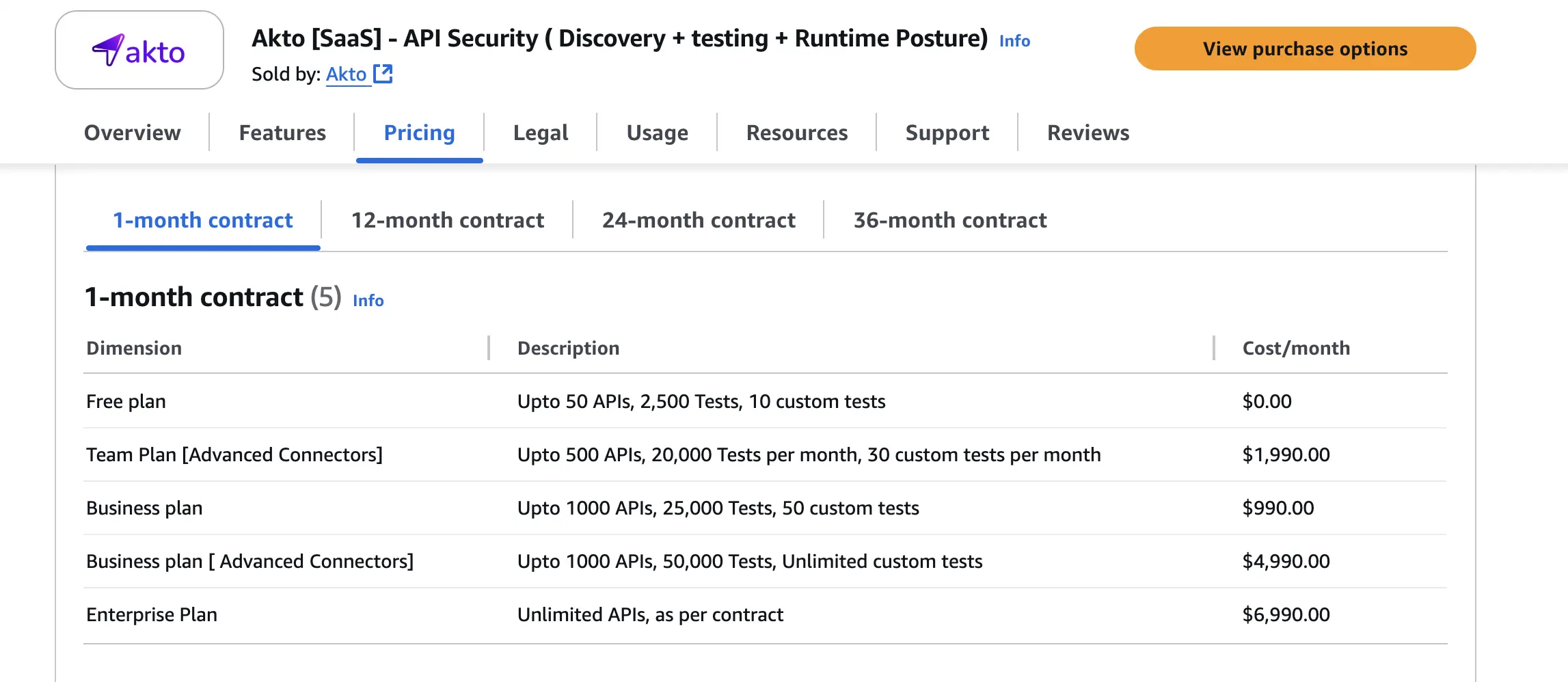
- Free tier available; uses a usage-based/licensed model via marketplaces (SaaS) per contract.
- Team Plan [Advanced Connectors] :
- $1,990/month
- Up to 500 APIs, 20,000 Tests per month, 30 custom tests per month
- Business plan :
- $990/month
- Up to 1000 APIs, 25,000 Tests, 50 custom tests
- Business plan [ Advanced Connectors]
- $4,990/month
- Up to 1000 APIs, 50,000 Tests, Unlimited custom tests
- Enterprise plan :
- $6,990/month.
- Unlimited APIs, as per contract
Best for:
Development, DevSecOps, and mid-sized security teams looking for embedded API security testing and continuous API-posture visibility without investing in large-scale enterprise-only solutions.
Secure Your APIs from attackers with Plexicus ASPM (Application Security Posture Management).
API security has become crucial recently in modern applications that have API to communicate with other applications, either internal or for external use cases.
However, common API security tools can only detect vulnerabilities in APIs; meanwhile, the surface of attack is beyond that.
Plexicus ASPM bridges this critical gap by not only securing your API, but it also unifying API Security, Secret Detection, Dependencies scanning,Infrastructure-as-Code Security, and AI remediation in one place to make comprehensive application security instead of using a siloed application security tool.
Ready to secure your end-to-end application ? Start Plexicus ASPM for free