Best SCA Tools in 2025 | Software Composition Analysis
Discover the best SCA tools in 2025 for scanning dependencies, managing vulnerabilities, and strengthening app security.

Best SCA Tools in 2025: Scan Dependencies, Secure Your Software Supply Chain
Need SCA Tools to Secure Applications?
Modern applications depend a lot on third-party and open-source libraries. This speeds up development, but it also increases the risk of attacks. Each dependency can introduce issues like unpatched security flaws, risky licenses, or outdated packages. Software Composition Analysis (SCA) tools help address these problems.
Software Composition Analysis (SCA) in cybersecurity helps you identify vulnerable dependencies (external software components with security issues), monitor license usage, and generate SBOMs (Software Bills of Materials, which list all software components in your application). With the right SCA security tool, you can detect vulnerabilities in your dependencies earlier, before attackers exploit them. These tools also help minimize legal risks from problematic licenses.
Why Listen to Us?
At Plexicus, we help organizations of all sizes strengthen their application security. Our platform brings together SAST, SCA, DAST, secrets scanning, and cloud security in one solution. We support companies at every stage to secure their applications.
“As pioneers in cloud security, we’ve found Plexicus to be remarkably innovative in the vulnerability remediation space. The fact that they’ve integrated Prowler as one of their connectors demonstrates their commitment to leveraging the best open-source tools while adding significant value through their AI-powered remediation capabilities”

Jose Fernando Dominguez
CISO, Ironchip
Quick Comparison of the Best SCA Tools in 2025
| Platform | Core Features / Strengths | Integrations | Pricing | Best For | Cons / Limits |
|---|---|---|---|---|---|
| Plexicus ASPM | Unified ASPM: SCA, SAST, DAST, secrets, IaC, cloud scan; AI remediation; SBOM | GitHub, GitLab, Bitbucket, CI/CD | Free trial; $50/mo/developer; Custom | Teams needing full security posture in one | May be overkill for just SCA |
| Snyk Open Source | Developer-first; fast SCA scan; code+container+IaC+license; active updates | IDE, Git, CI/CD | Free; Paid from $25/mo/dev | Dev teams needing code/SCA in pipeline | Can get expensive at scale |
| Mend (WhiteSource) | SCA-focused; compliance; patching; automated updates | Major platforms | ~$1000/year per developer | Enterprises: compliance & scale | Complex UI, expensive for big teams |
| Sonatype Nexus Lifecycle | SCA + repo governance; rich data; integrates with Nexus Repo | Nexus, major tools | Free tier; $135/mo repo; $57.50/user/mo | Large organizations, repo management | Learning curve, cost |
| GitHub Advanced Security | SCA, secrets, code scan, dependency graph; native to GitHub workflows | GitHub | $30/committer/mo (code); $19/mo secrets | GitHub teams wanting native solution | Only for GitHub; pricing per committer |
| JFrog Xray | DevSecOps focus; strong SBOM/license/OSS support; integrates w/ Artifactory | IDE, CLI, Artifactory | $150/mo (Pro, cloud); Enterprise high | Existing JFrog users, artifact managers | Price, best for large/jfrog orgs |
| Black Duck | Deep vulns & license data, policy automation, mature compliance | Major platforms | Quote-based (contact sales) | Large, regulated orgs | Cost, slower adoption for new stacks |
| FOSSA | SCA + SBOM & license automation; developer friendly; scalable | API, CI/CD, major VCS | Free (limited); $23/project/mo Biz; Enterprise | Compliance + scalable SCA clusters | Free is limited, cost scales quick |
| Veracode SCA | Unified platform; advanced vuln detection, reporting, compliance | Various | Contact sales | Enterprise users w/ broad AppSec needs | High price, onboarding more complex |
| OWASP Dependency-Check | Open-source, covers CVEs via NVD, broad tool/plugin support | Maven, Gradle, Jenkins | Free | OSS, small teams, zero-cost needs | Only known CVEs, basic dashboards |
The Top 10 Software Composition Analysis (SCA) Tools
1. Plexicus ASPM
Plexicus ASPM is more than just an SCA tool; it’s a full Application Security Posture Management (ASPM) platform. It unifies SCA, SAST, DAST, secret detection, and cloud misconfiguration scanning in a single solution.
Traditional tools just raise alerts, but Plexicus takes it further with an AI-powered assistant that helps fix vulnerabilities automatically. This reduces security risks and saves developers time by combining different testing methods and automated fixes in one platform.
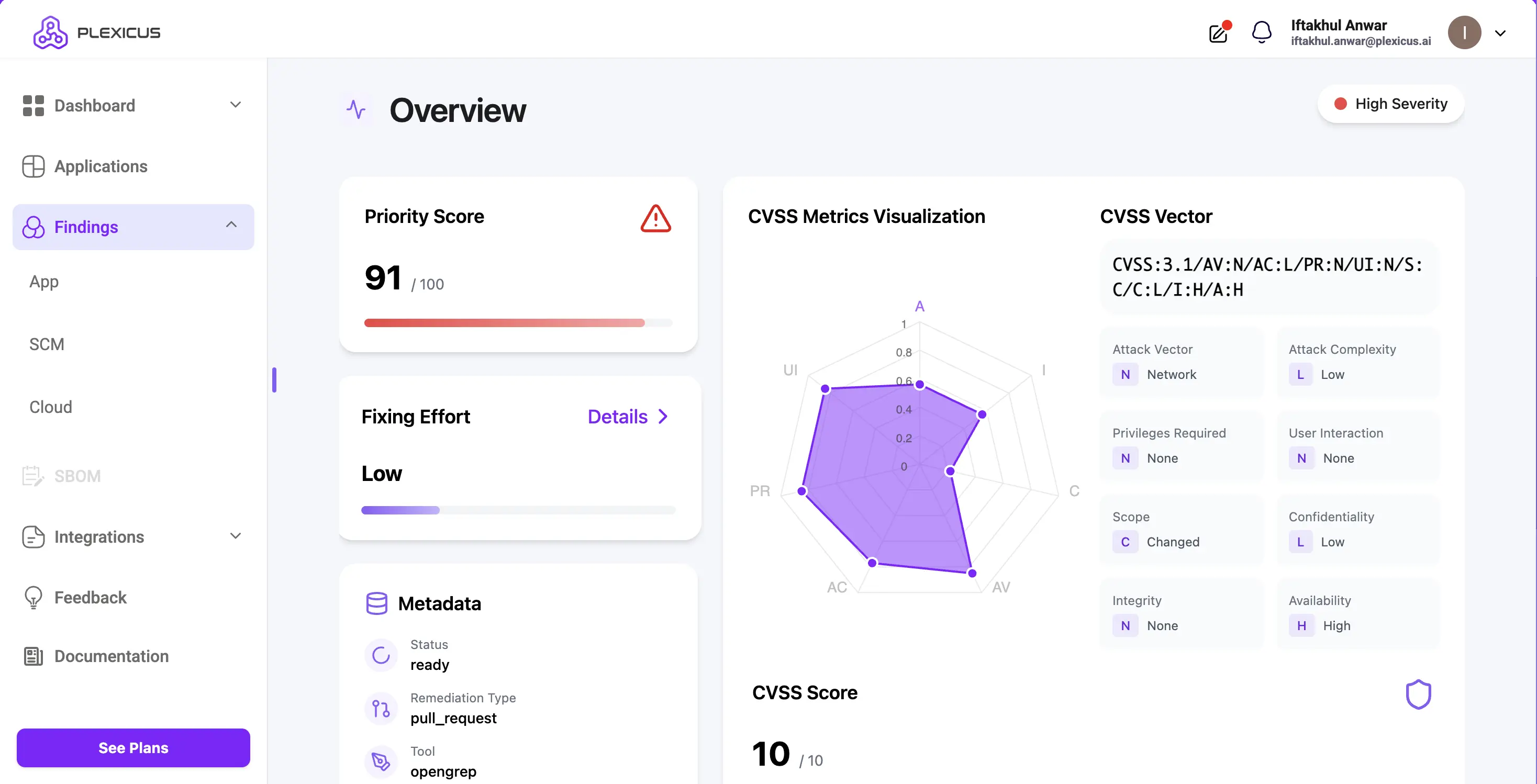
Pros:
- Unified dashboard for all vulnerabilities (not just SCA)
- Prioritization engine reduces noise.
- Native integrations with GitHub, GitLab, Bitbucket, and CI/CD tools
- SBOM generation & license compliance built-in
Cons:
- May feel overkill product if you only want SCA functionality
Pricing:
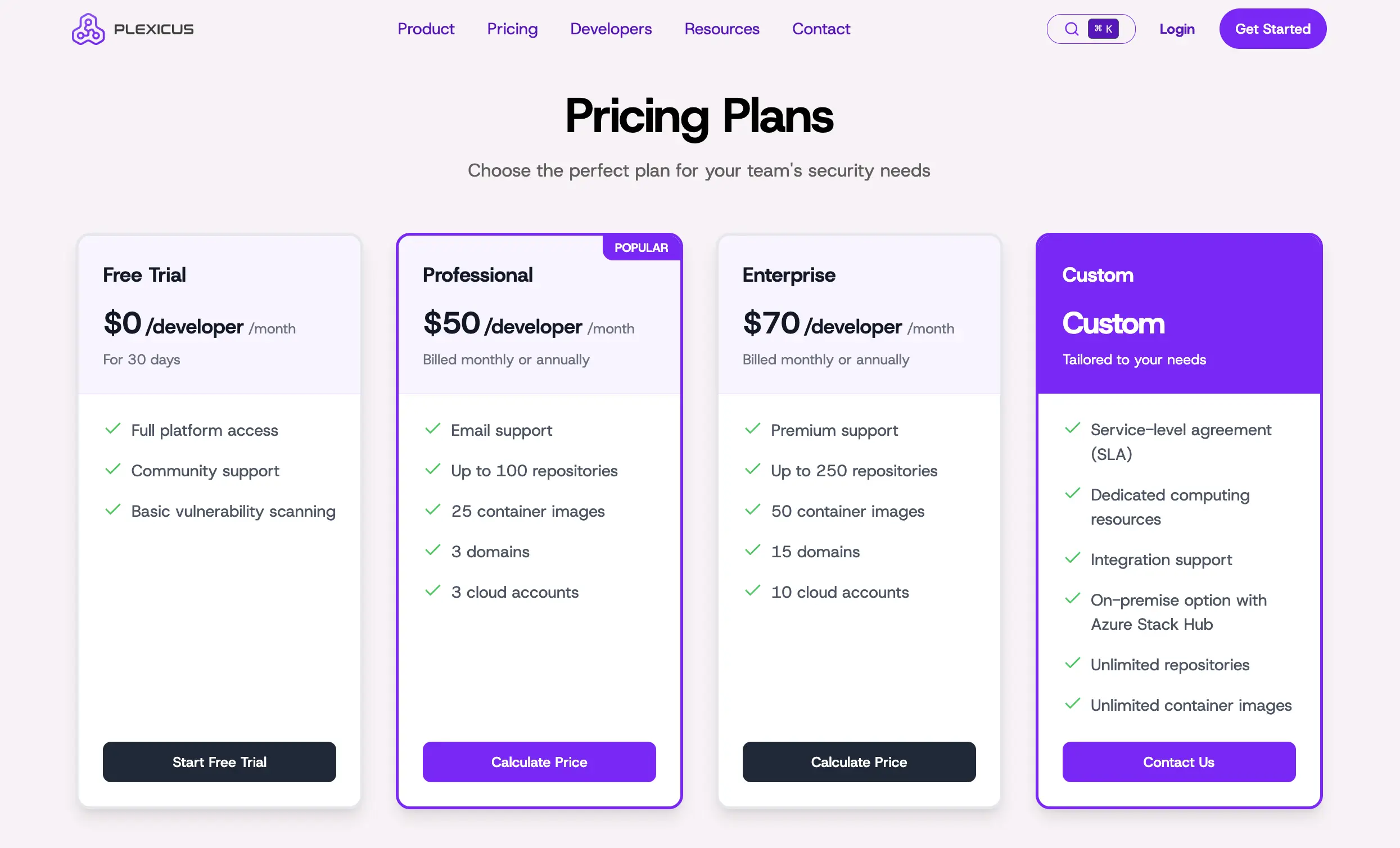
- Free Trial for 30 Days
- $50/month per developer
- Contact sales for a custom tier.
Best for: Teams that want to go beyond SCA with a single security platform.
2. Snyk Open Source
Snyk open-source is a developer-first SCA tool that scans dependencies, flags known vulnerabilities, and integrates with your IDE and CI/CD. Its SCA features are widely used in modern DevOps workflows.
Pros:
- Strong developer experience
- Great integrations (IDE, Git, CI/CD)
- Covers license compliance, container & Infra-as-Code (IaC) scanning
- Large vulnerability database and active updates
Cons:
- Can get costly at scale
- The free plan has limited features.
Pricing:
- Free
- Paid from $25/mo per developer, min 5 developers
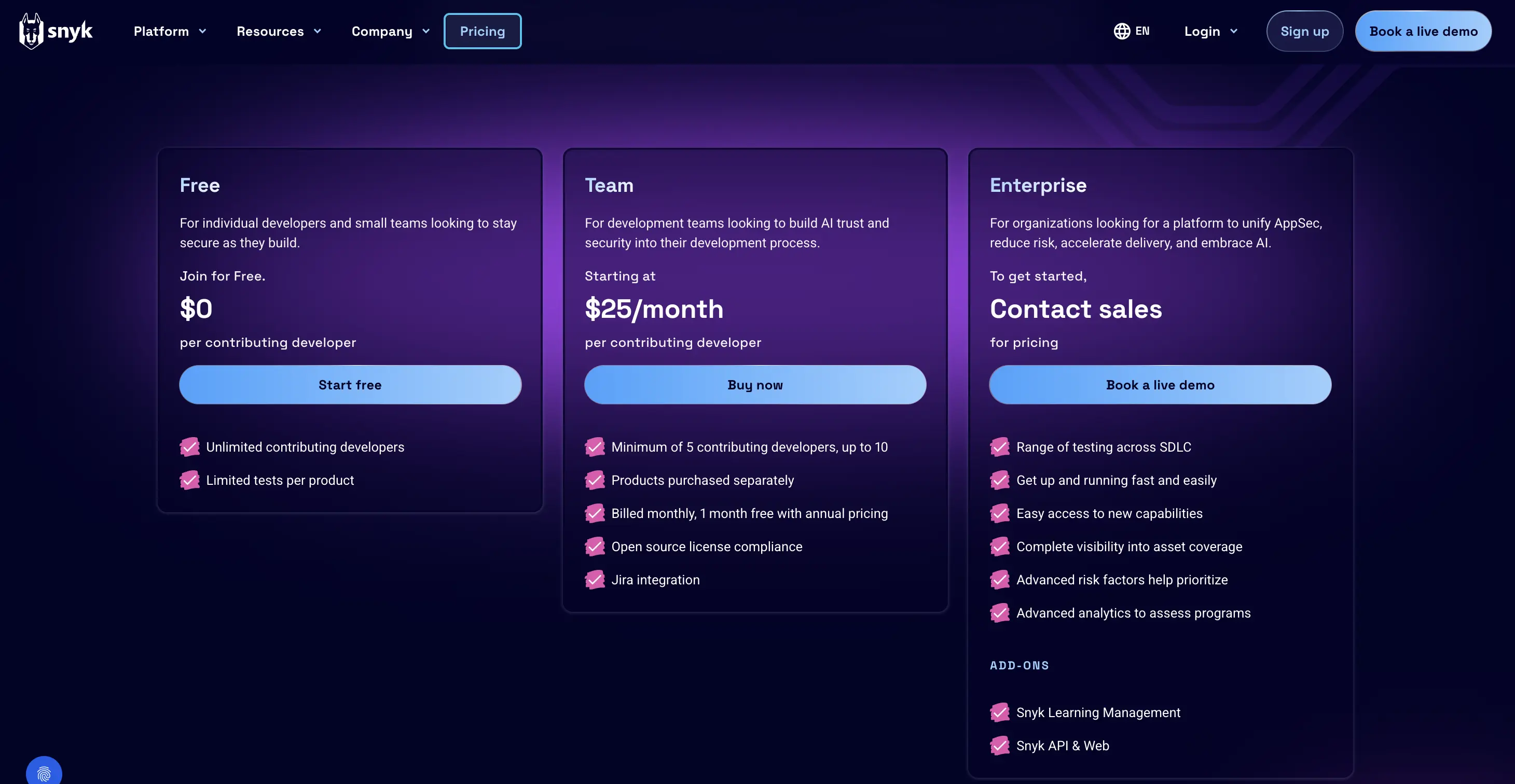
Best for: Developer teams that want a quick code analyzer + SCA in their pipelines.
3. Mend (WhiteSource)
Mend (formerly WhiteSource) specializes in SCA security testing with strong compliance features. Mend provides a holistic SCA solution with license compliance, vulnerability detection, and integration with remediation tools.
Pros:
- Excellent for license compliance
- Automated patching & dependency updates
- Good for enterprise-scale usage
Cons:
- Complex UI
- High cost for the scale team
Pricing: $1,000/year per developer
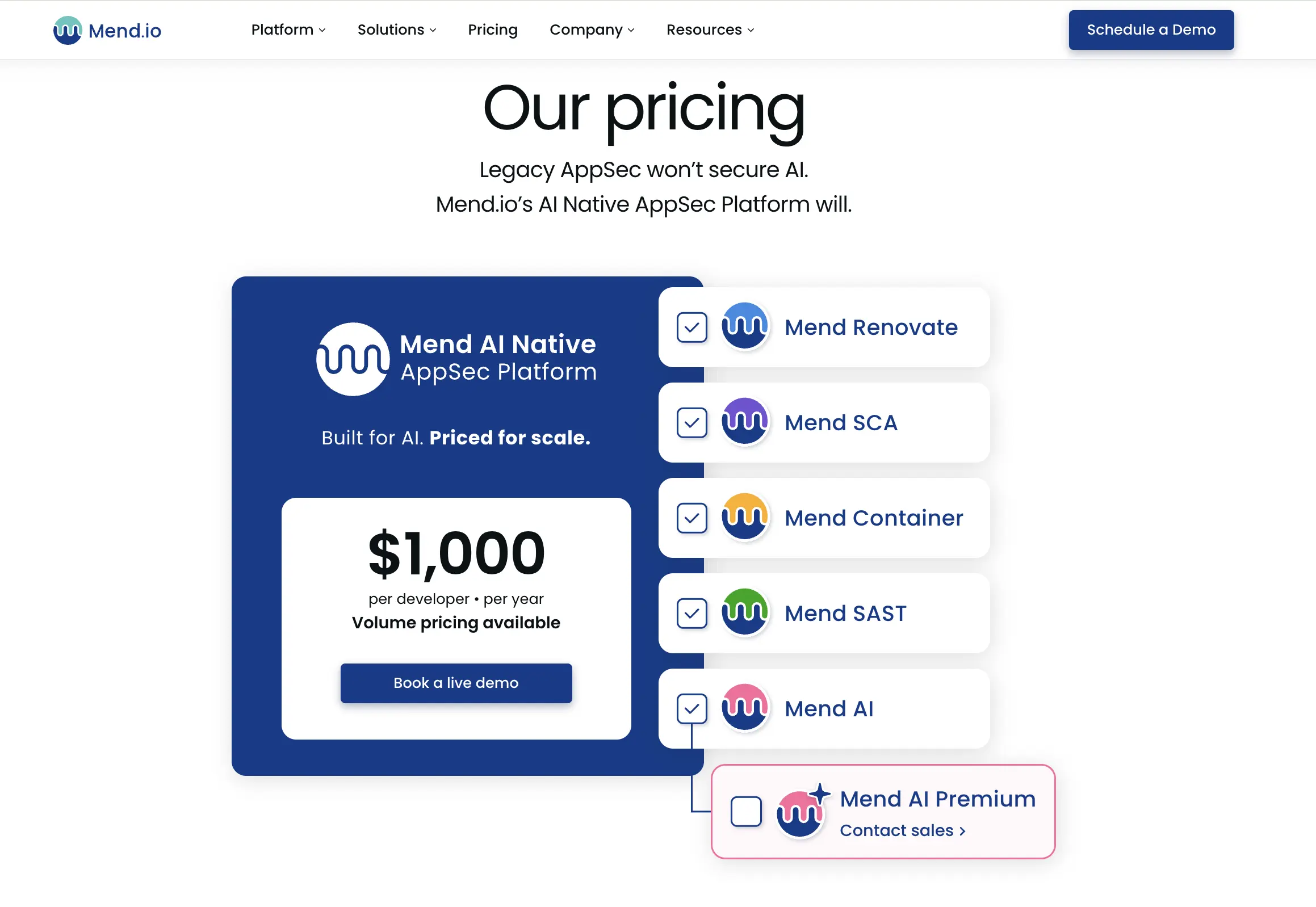
Best for: Large enterprises with compliance-heavy requirements.
4. Sonatype Nexus Lifecycle
One of the Software composition analysis tools that focuses on supply chain governance.
Pros:
- Rich security & license data
- Integrates seamlessly with Nexus Repository
- Good for a large dev organization
Cons:
- Steep learning curve
- It may be overkill for small teams.
Pricing:
- Free tier available for Nexus Repository OSS components.
- Pro plan starts at US$135**/month** for Nexus Repository Pro (cloud) + consumption charges.
- SCA + remediation with Sonatype Lifecycle ~ US$57.50**/user/month** (annual billing).
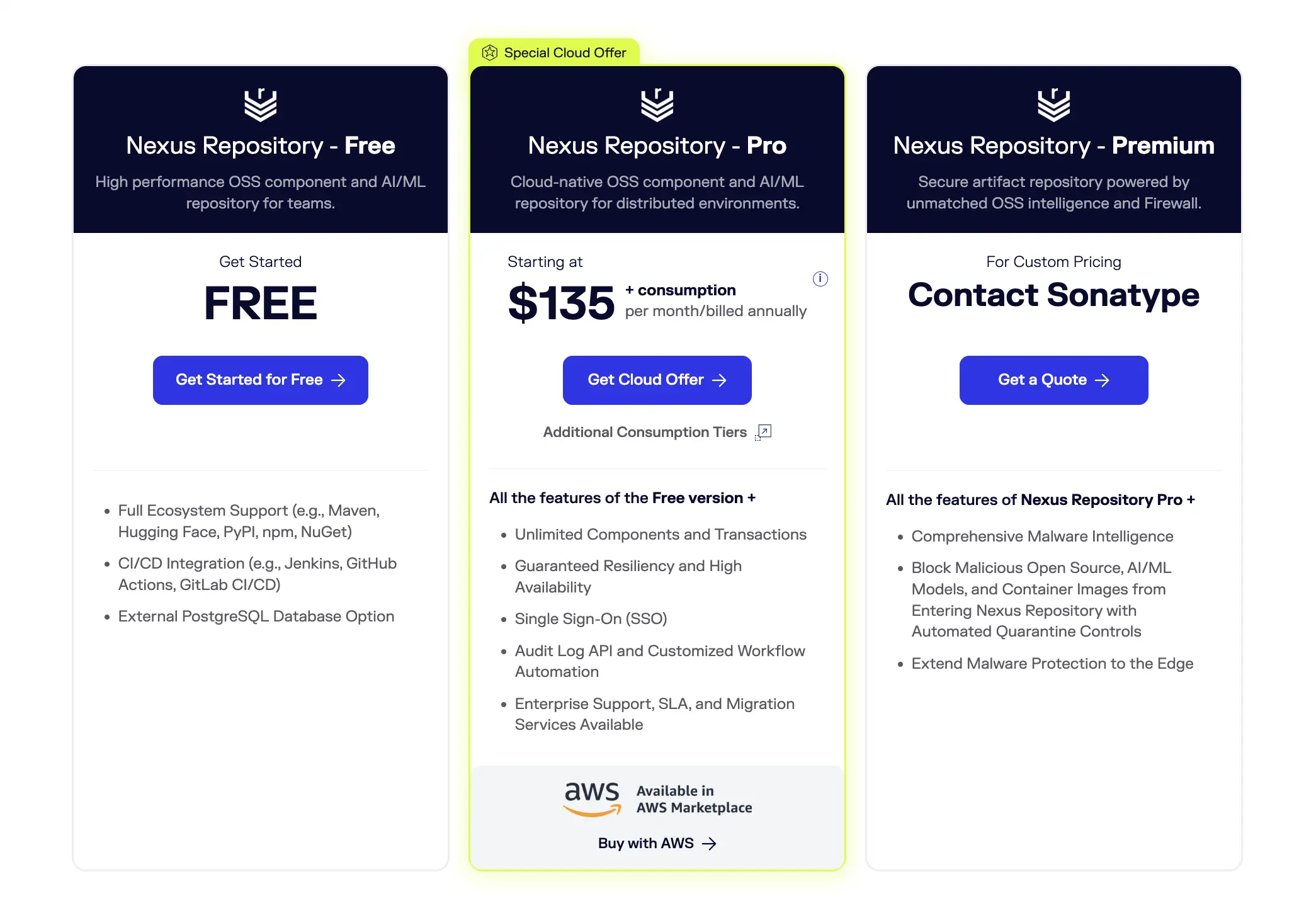
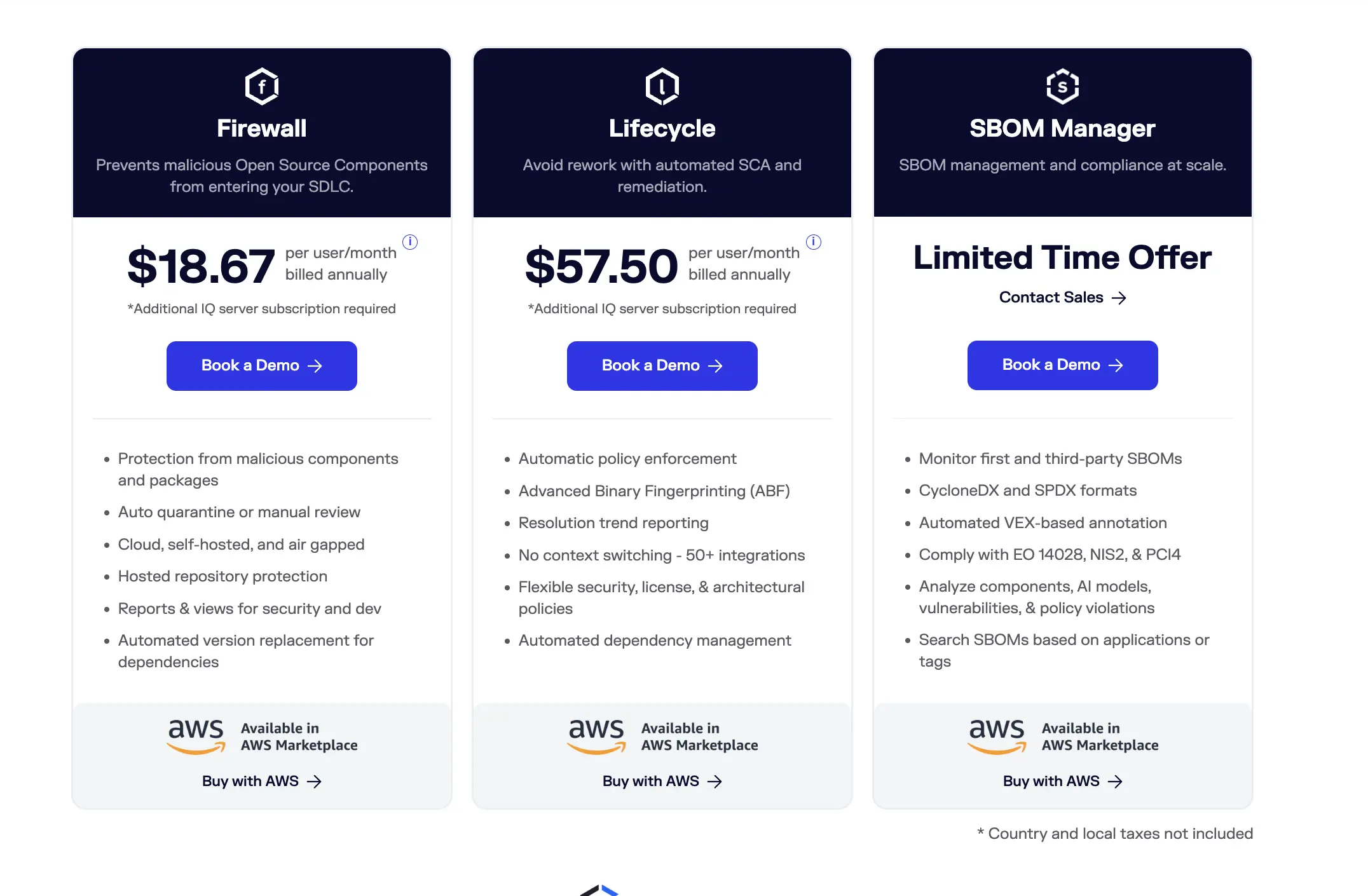
Best for: Organizations needing both SCA security testing and artifact/repository management with strong OSS intelligence.
5. GitHub Advanced Security (GHAS)
GitHub Advanced Security is GitHub’s built-in code and dependency security tooling, which includes software composition analysis (SCA) features like dependency graph, dependency review, secret protection, and code scanning.
Pros:
- Native integration with GitHub repositories and CI/CD workflows.
- Strong for dependency scanning, license checks, and alerts via Dependabot.
- Secret protection and code security are built in as add-ons.
Cons:
- Pricing is per active committer; it can get expensive for large teams.
- Some features are only available on Team or Enterprise plans.
- Less flexibility outside the GitHub ecosystem.
Price:
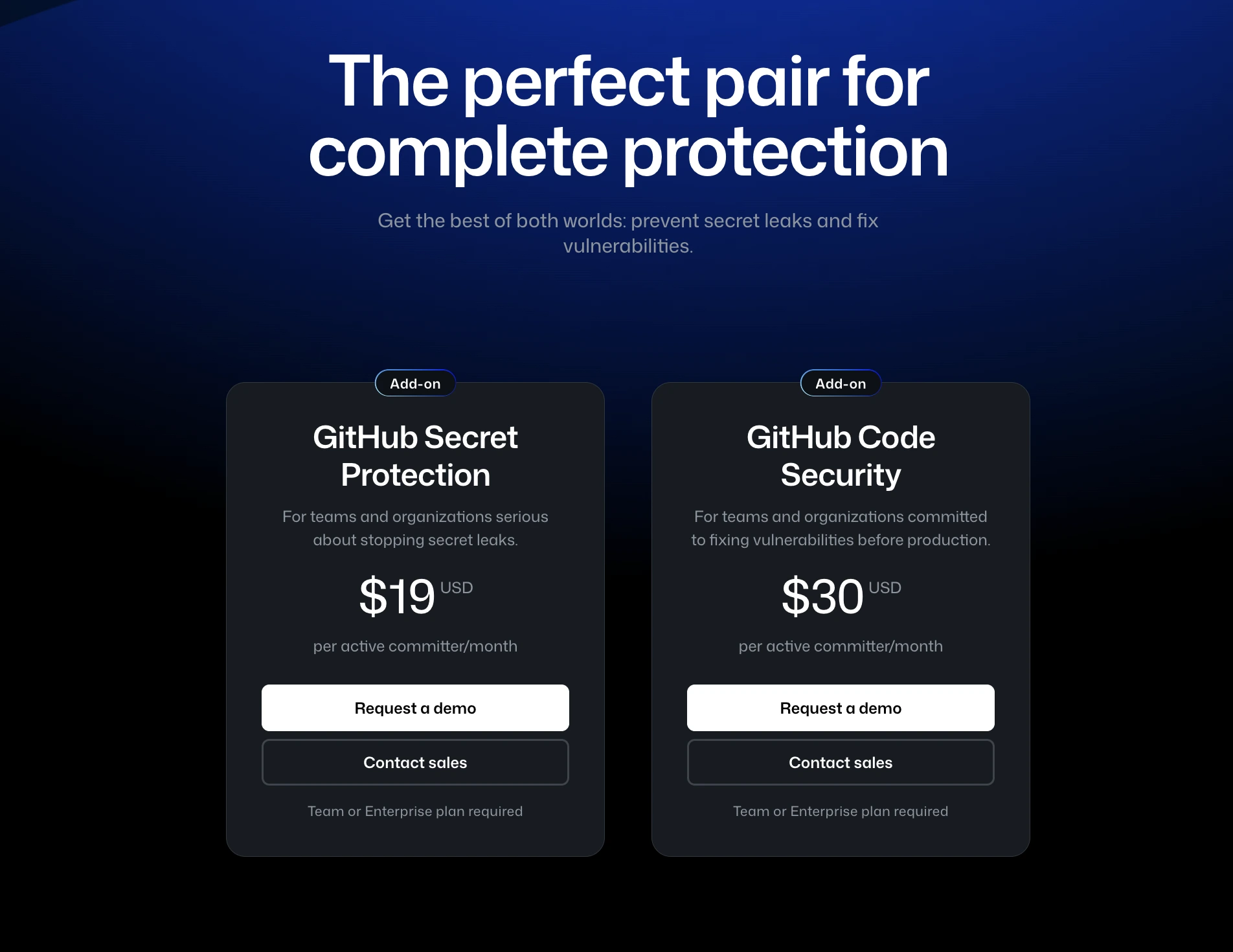
- GitHub Code Security: US$30 per active committer/month (Team or Enterprise required).
- GitHub Secret Protection: US$19 per active committer/month.
Best for: Teams that host code on GitHub and want integrated dependency & secret scanning without managing separate SCA tools.
6. JFrog Xray
JFrog Xray is one of the SCA tools that can help you to identify, prioritize, and remediate security vulnerabilities and license compliance issues in open source software (OSS).
JFrog provides a developer-first approach where they integrate with IDE and CLI to make it easier for developers to run JFrog Xray frictionless.
Pros:
- Strong DevSecOps integration
- SBOM and license scanning
- Powerful when combined with JFrog Artifactory (their universal artifact repository manager)
Cons:
- Best for existing JFrog users
- Higher cost for small teams
Pricing
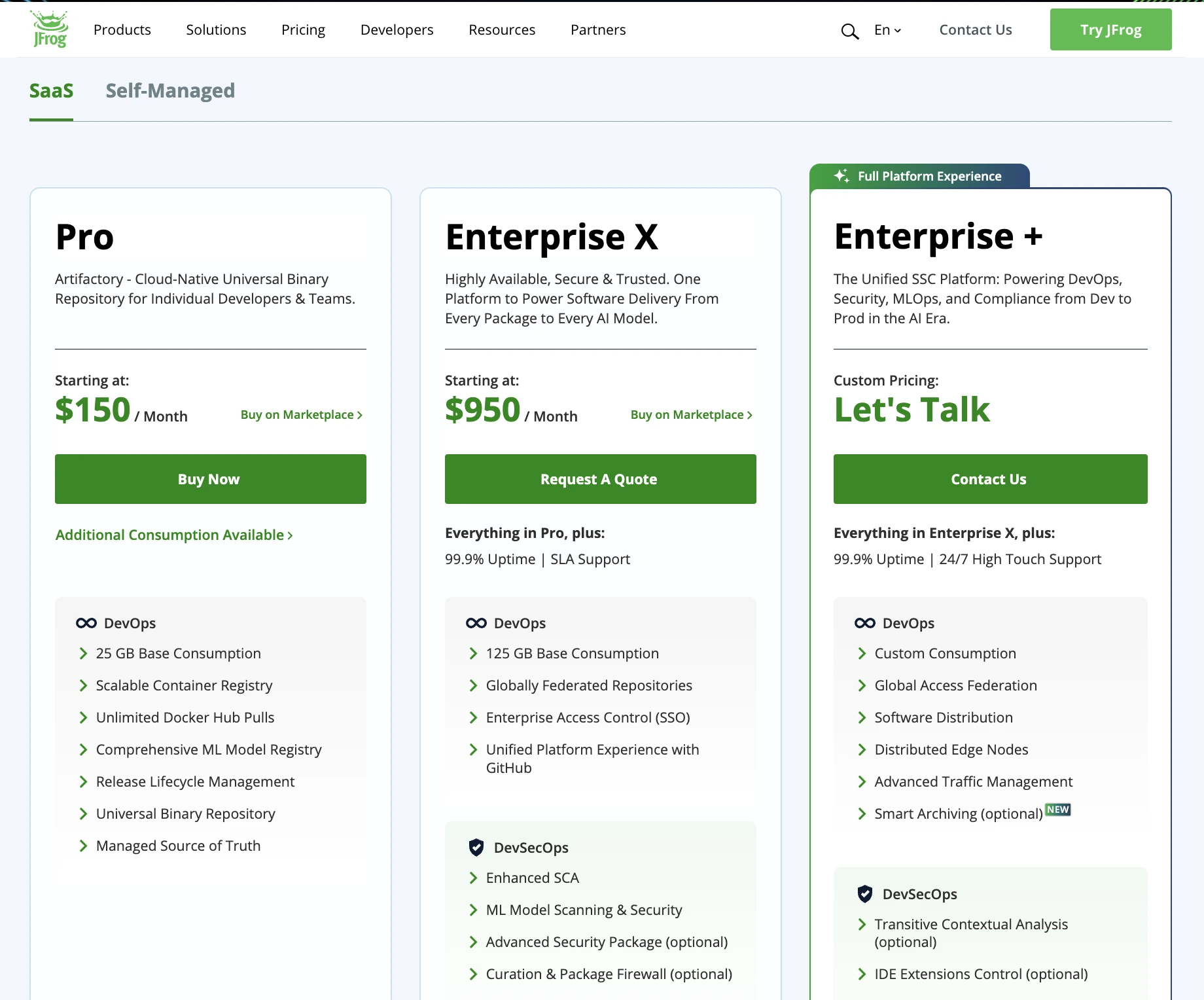
JFrog offers flexible tiers for its software composition analysis (SCA) and artifact management platform. Here’s how the pricing looks:
- Pro: US$150/month (cloud), includes base 25 GB storage / consumption; extra usage cost per GB.
- Enterprise X: US$950/month, more base consumption (125 GB), SLA support, higher availability.
- Pro X (Self-Managed / Enterprise Scale): US$27,000/year, intended for large teams or organizations needing full self-managed capacity.
7. Black Duck
Black Duck is an SCA/security tool with deep open-source vulnerability intelligence, license enforcement, and policy automation.
Pros:
- Extensive vulnerability database
- Strong license compliance and governance features
- Good for large, regulated organizations
Cons:
- Cost requires quoting from vendor.
- Sometimes slower adaptation to new ecosystems compared to newer tools
Price:
- “Get Pricing” model, must contact to sales team.
Best for: Enterprises needing mature, battle-tested open-source security and compliance.
Note : Plexicus ASPM also integrates with Black Duck as one of the SCA tools in the Plexicus ecosystem
8. Fossa
FOSSA is a modern Software Composition Analysis (SCA) platform that focuses on open-source license compliance, vulnerability detection, and dependency management. It provides automated SBOM (Software Bill of Materials) generation, policy enforcement, and developer-friendly integrations.
Pros:
- Free plan available for individuals and small teams
- Strong license compliance and SBOM support
- Automated license & vulnerability scanning in Business/Enterprise tiers
- Developer-centric with API access and CI/CD integrations
Cons:
- Free plan limited to 5 projects and 10 developers
- Advanced features like multi-project reporting, SSO, and RBAC require the Enterprise tier.
- Business plan scales cost per project, which can grow expensive for large portfolios.
Price:
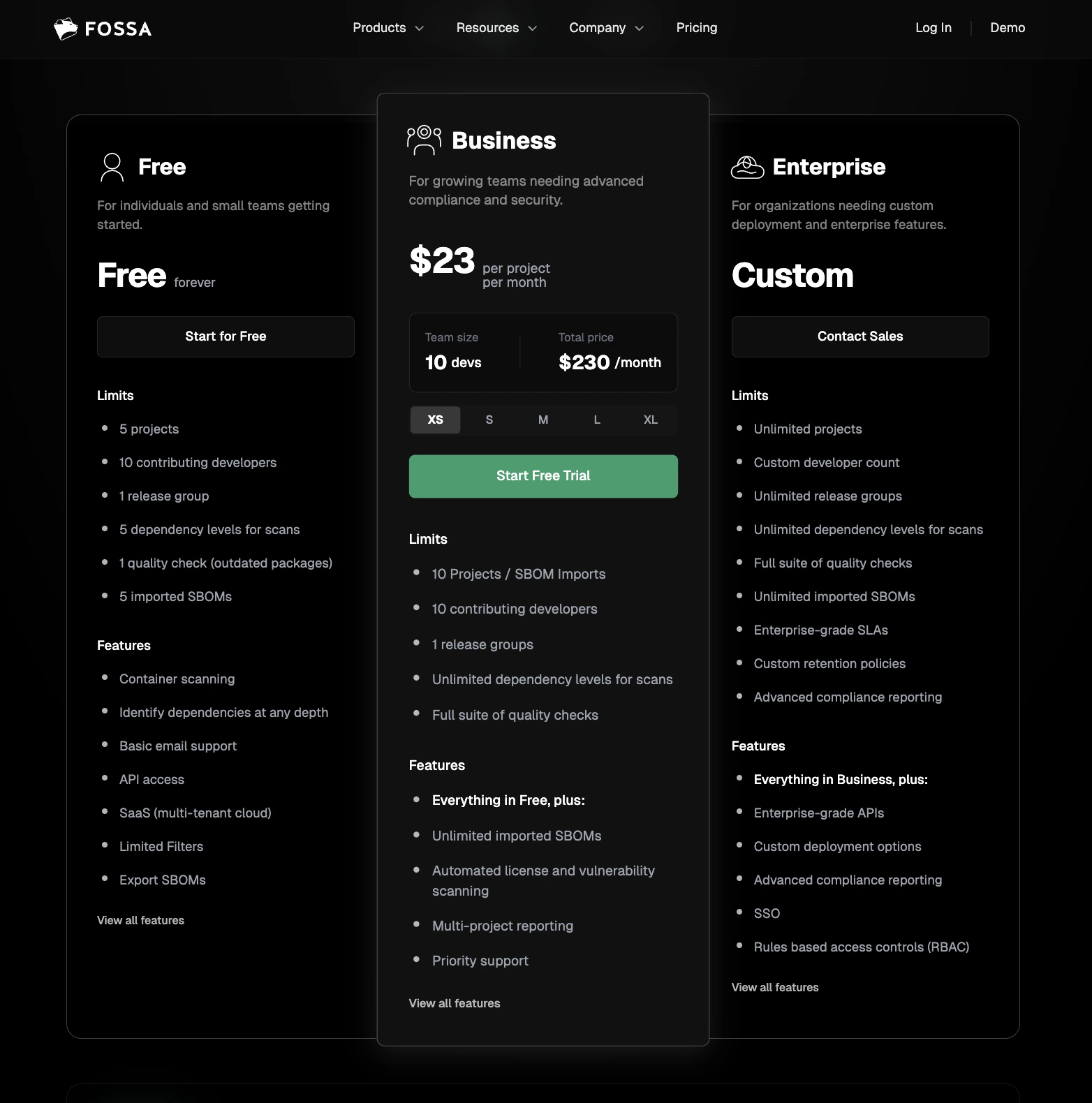
- Free: up to 5 projects and 10 contributing developers
- Business: $23 per project/month (example: $230/month for 10 projects & 10 developers)
- Enterprise: Custom pricing, includes unlimited projects, SSO, RBAC, advanced compliance reporting
Best for: Teams that need open-source license compliance + SBOM automation alongside vulnerability scanning, with scalable options for startups through to large enterprises.
9.Veracode SCA
Veracode SCA is a software composition analysis tool that offers security in your application by identifying and acting on open-source risks with precision, ensuring secure and compliant code. Veracode SCA also scans code to uncover hidden and emerging risks with the proprietary database, including vulnerabilities not yet listed in the National Vulnerability Database (NVD)
Pros:
- Unified platform across different security testing types
- Mature enterprise support, reporting, and compliance features
Cons:
- Pricing tends to be high.
- Onboarding and integration may have a steep learning curve.
Price: Not mentioned on the website; need to contact their sales team
Best for: Organizations already using Veracode’s AppSec tools, wanting to centralize open-source scanning.
10. OWASP Dependency-Check
OWASP Dependency-Check is an open-source SCA (Software Composition Analysis) tool designed to detect publicly disclosed vulnerabilities in a project’s dependencies.
It works by identifying Common Platform Enumeration (CPE) identifiers for libraries, matching them to known CVE entries, and integrating via multiple build tools (Maven, Gradle, Jenkins, etc).
Pros:
- Fully free and open-source, under the Apache 2 license.
- Broad integration support (command-line, CI servers, build plugins: Maven, Gradle, Jenkins, etc.)
- Regular updates via NVD (National Vulnerability Database) and other data feeds.
- Works well for developers wanting to catch known vulnerabilities in dependencies early.
Cons:
- Limited to detecting known vulnerabilities (CVE-based)
- Cannot find custom security issues or business logic flaws.
- Reporting and dashboards are more basic compared to commercial SCA tools; they lack built-in remediation guidance.
- May need tuning: large dependency trees can take time, and occasional false positives or missing CPE mappings.
Price:
- Free (no cost).
Best for:
- Open-source projects, small teams, or anyone needing a zero-cost dependency vulnerability scanner.
- An early stages team that needs to catch known issues in dependencies before moving to paid/commercial SCA tools.
Reduce security risk in your application with the Plexicus Application Security Platform (ASPM)
Choosing the right SCA or SAST tool is only half the battle. Most organizations today face tool sprawl, running separate scanners for SCA, SAST, DAST, secret detection, and cloud misconfigurations. This often leads to duplicated alerts, siloed reports, and security teams drowning in noise.
That’s where Plexicus ASPM comes in. Unlike point-solution SCA tools, Plexicus unifies SCA, SAST, DAST, secret detection, and cloud misconfigurations into a single workflow.
What makes Plexicus different:
- Unified Security Posture Management → Instead of juggling multiple tools, get one dashboard for your entire application security.
- AI-Powered Remediation → Plexicus doesn’t just alert you to issues; it offers automated fixes for vulnerabilities, saving developers hours of manual work.
- Scales With Your Growth → Whether you’re an early-stage startup or a global enterprise, Plexicus adapts to your codebase and compliance requirements.
- Trusted by Organizations → Plexicus already helps companies secure applications in production environments, reducing risk and accelerating time to release.
If you’re evaluating SCA or SAST tools in 2025, it’s worth considering whether a standalone scanner is enough, or if you need a platform that consolidates everything into one intelligent workflow.
With Plexicus ASPM, you don’t just check a compliance box. You stay ahead of vulnerabilities, ship faster, and free your team from security debt. Start securing your application with the Plexicus free plan today.