Top 10 SentinelOne Singularity Cloud Alternatives for 2026: From Autonomous Detection to AI Remediation
SentinelOne Singularity Cloud was one of the first in the Autonomous EDR/CWPP field. Its AI-powered agents offer fast, offline protection and have helped many organizations avoid ransomware attacks.
However, as we move into 2026, the bottleneck has shifted from Detection to Throughput. With 131+ new CVEs appearing every day and AI agents shipping code at machine speed, simply “blocking” a threat is no longer enough. To illustrate the risk, consider this scenario: a missed CVE today can be exploited within hours, leading to data breaches costing companies millions in recovery efforts. Modern teams are looking for alternatives that can bridge the “Security-Developer Gap” by providing Automated Remediation to clear the massive backlog of vulnerabilities.
Why Trust Us?
At Plexicus, we believe security is a Throughput Problem. Our expertise is built on high-stakes vulnerability research, including 170+ verified bugs in curl; and we prioritize tools that achieve a 95% reduction in MTTR by replacing manual triage with AI-assisted code fixes. We don’t just alert; we close the ticket.
At a Glance: Top 10 SentinelOne Alternatives for 2026
| Platform | Best For | Core Differentiator | Setup Type |
|---|---|---|---|
| Plexicus | Rapid Remediation | AI-Powered “Click-to-Fix” | Agentless (OIDC) |
| Wiz | Cloud Visibility | The Security Graph | Agentless |
| CrowdStrike | Threat Intelligence | Single-Agent XDR | Agent-based |
| Sysdig Secure | K8s Runtime | eBPF-based Active Blocking | Agent-based |
| Orca Security | Data Security | SideScanning Technology | Agentless |
| Prisma Cloud | Enterprise Compliance | Unified Policy-as-Code | Hybrid |
| AccuKnox | Zero Trust | KubeArmor Inline Mitigation | Agent-based |
| Microsoft Defender | Azure Ecosystem | Native Cloud Integration | Hybrid |
| Aqua Security | Image Assurance | Secure-by-Default Scanning | Hybrid |
| Trend Vision One | Hybrid/Multi-Cloud | Virtual Patching for Legacy | Hybrid |
1. Plexicus
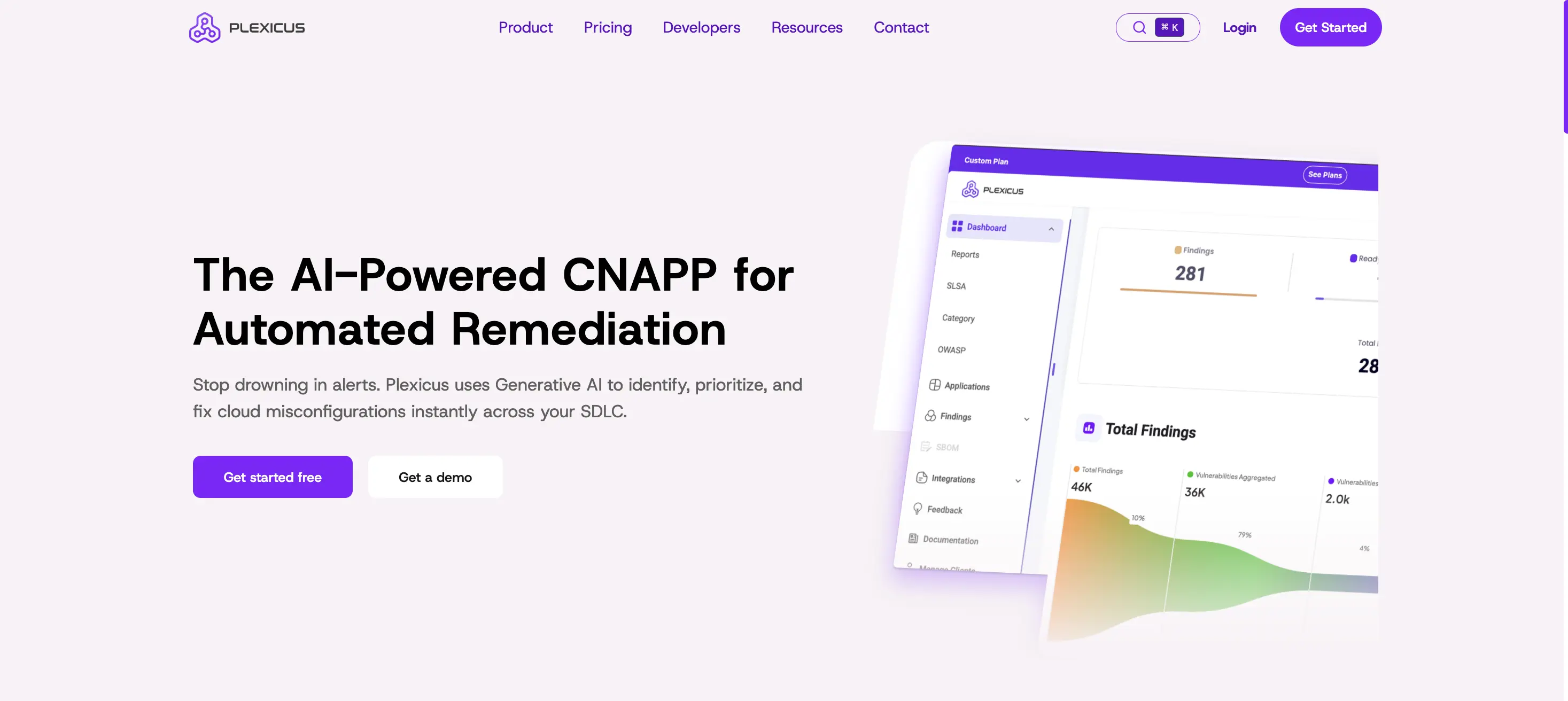
Plexicus addresses the “Time-to-Exploit” gap by replacing manual research with Human-Triggered AI Remediation. While SentinelOne is built for the SOC, Plexicus is built for the Developer-Security partnership.
- Key Features: Codex Remedium is an AI engine that analyzes vulnerabilities and generates functional code patches, pull requests, and unit tests tailored to your specific codebase.
- Core Differentiator: Plexicus moves from “Alerting” to “Orchestrating.” It takes a finding—whether from code or cloud- and provides a one-click remediation path to close the risk.
- Pros: Massive reduction in MTTR; connects Code (ASPM), Container Security, and Cloud (CSPM] in one unified fix workflow; agentless deployment.
- Cons: Production merges still require a human gatekeeper for safety.
- Why Choose It: If your engineering team is the primary bottleneck and you need to automate the “fix” part of security.
2. Wiz
Wiz is the industry-leading agentless alternative. In 2026, it remains the standard for Visibility, using a graph database to show how a cloud vulnerability could lead to a breach.
- Key Features: Agentless scanning; Security Graph identifying “Toxic Combinations” of risk.
- Core Differentiator: Exceptional UI/UX that makes complex cloud-native architectures easy to secure.
- Pros: Fastest “time-to-visibility”; very low management overhead.
- Cons: No runtime process-killing; pricing can scale aggressively with workload volume.
3. CrowdStrike Falcon Cloud Security
CrowdStrike is the most direct rival to SentinelOne. It is favored by teams that want the best Threat Intelligence and a unified agent for both laptop and server.
- Key Features: 24/7 Managed Detection and Response (MDR); single-agent architecture.
- Core Differentiator: Correlation of global threat data from millions of endpoints to block cloud attacks.
- Pros: World-class incident response; strong runtime prevention.
- Cons: Less focus on “Shift Left” (code/SCA) than specialized developer tools.
4. Sysdig Secure
If your stack is heavy on Kubernetes, Sysdig is the standard. It uses eBPF to see attacks inside the kernel as they happen.
- Key Features: Real-time runtime blocking; deep Kubernetes forensics.
- Core Differentiator: Built on the Falco open-source standard, providing the deepest possible visibility into container behavior.
- Pros: Superior runtime prevention; very low performance impact.
- Cons: High technical requirements to manage Falco rules.
5. Orca Security
Orca pioneered SideScanning, which scans your cloud workloads at the block-storage level. It is the best alternative for Data Security (DSPM).
- Key Features: Sensitive data discovery; agentless vulnerability management.
- Core Differentiator: A unified data model that provides full-stack visibility without ever running code on your hosts.
- Pros: Zero friction with DevOps; deep visibility into unmanaged assets.
- Cons: Limited real-time response compared to agent-based EDR.
6. Prisma Cloud (Palo Alto Networks)
Prisma is the “consolidator’s choice.” It is the most comprehensive platform for large enterprises needing 360-degree compliance.
- Key Features: Unified Policy-as-Code; deep integration with Palo Alto’s firewall ecosystem.
- Core Differentiator: Covers every layer of the stack, from IaC scanning to network security firewalls.
- Pros: The safest “Enterprise” choice; covers every compliance framework (SOC2, HIPAA, ISO).
- Cons: Extremely complex; often requires a dedicated security team to manage.
7. AccuKnox
AccuKnox is the leader in Zero Trust runtime security, providing inline threat mitigation through its KubeArmor technology.
- Key Features: Inline mitigation (Network, File, Process); Zero Trust policy enforcement.
- Core Differentiator: It doesn’t just alert; it enforces a “Least Privilege” model at the OS level to stop attacks before they start.
- Pros: Strongest Kubernetes security; open-source-powered transparency.
- Cons: Higher barrier to entry for teams unfamiliar with Zero Trust architecture.
8. Microsoft Defender for Cloud
For Azure-centric organizations, Defender is the native choice that has evolved into a formidable multi-cloud platform.
- Key Features: Integrated security for Azure, AWS, and GCP; automated remediation for cloud misconfigurations.
- Core Differentiator: Deep native integration with Microsoft’s Entra ID and Defender for Endpoint.
- Pros: High cost-efficiency for Microsoft customers; seamless deployment.
- Cons: Multi-cloud features can feel less mature than pure-play rivals.
9. Aqua Security
Aqua is a pioneer in Cloud-Native Application Protection (CNAPP). It is best for teams that want to ensure their container images are “Secure-by-Default.”
- Key Features: Image assurance and signing; dynamic threat analysis in sandboxes.
- Core Differentiator: Deep focus on the build-and-deploy pipeline to prevent malicious code from reaching production.
- Pros: Excellent “Shift Left” integration; robust container security.
- Cons: The Interface can be modular and complex to navigate.
10. Trend Vision One
Trend Micro is the veteran for Hybrid Cloud environments. It is the best choice for organizations that still have significant on-premises legacy systems.
- Key Features: Virtual patching; broad support for legacy OS (e.g., Windows 2008).
- Core Differentiator: Decades of threat data combined with a modern XDR platform for hybrid environments.
- Pros: Unmatched support for mixed infrastructure; reliable, enterprise-grade stability.
- Cons: Can feel heavier and more “legacy” than modern, agentless cloud-native tools.
FAQ: The Realities of 2026 Security
Why switch from SentinelOne Singularity Cloud?
Many teams switch because of Alert Fatigue and Remediation Friction. While SentinelOne is great at blocking, it doesn’t help the developer fix the vulnerable code. Tools like Plexicus bridge that gap.
Does Plexicus replace SentinelOne?
Plexicus focuses on Remediation. While it monitors your environment, its primary value is helping you fix the vulnerabilities that EDR tools like SentinelOne would alert on. In 2026, the goal is to move from “blocking” to “patching” in under 60 seconds.
Is agentless security as safe as SentinelOne’s agent?
In 2026, visibility is protection. Agentless tools (Plexicus, Wiz) give you 100% visibility across your entire multi-cloud instantly. This is often more effective than having deep agents on only the 20% of servers that your team successfully managed to install them on.
Final Thought
The “Software Supply Chain” is the new perimeter. If you are still relying on a tool that just alerts you to threats, you are fighting a machine-speed battle with human-speed tools. You need a platform that accelerates the fix.