Top 10 Sysdig Alternatives: From Deep Forensics to Automated Fixing
Sysdig has been recognized for its strong kernel event coverage. It is built on Falco’s open-source foundation and is a favorite among SOC teams who need detailed visibility into Linux kernels or Kubernetes pods.
As organizations approach 2026, the security landscape will have changed. While Sysdig remains strong at detecting breaches, many teams now face a new gap: fixing the underlying issues. With over 159 CVEs exploited in Q1 2025 alone[2] and the growing volume of AI-generated code, the backlog from simple alerts is growing.
[2] Source: “159 CVEs Exploited in Q1 2025, 28.3% Within 24 Hours of Disclosure.”The Hacker News, citing VulnCheck research.https://thehackernews.com/2025/04/159-cves-exploited-in-q1-2025-283.html.Accessed 31 Dec. 2025.
As you consider your toolset, remember that reporting attacks isn’t enough; effective security now demands tools that help you close the loop with actionable fixes. Decision-makers should prioritize solutions with robust remediation capabilities to align with the evolving security needs. By focusing on tools that not only detect but also automate and streamline fixes, organizations can significantly reduce their exposure to vulnerabilities and enhance their overall security posture.
Why Trust Us?
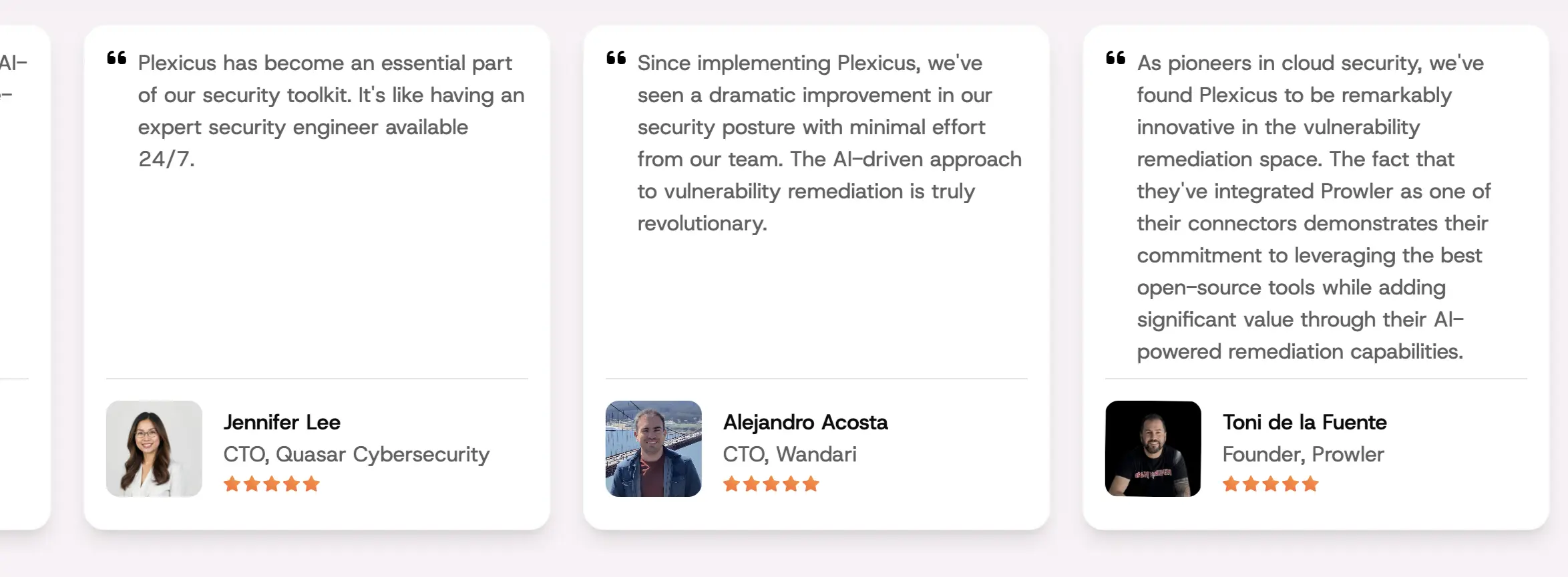
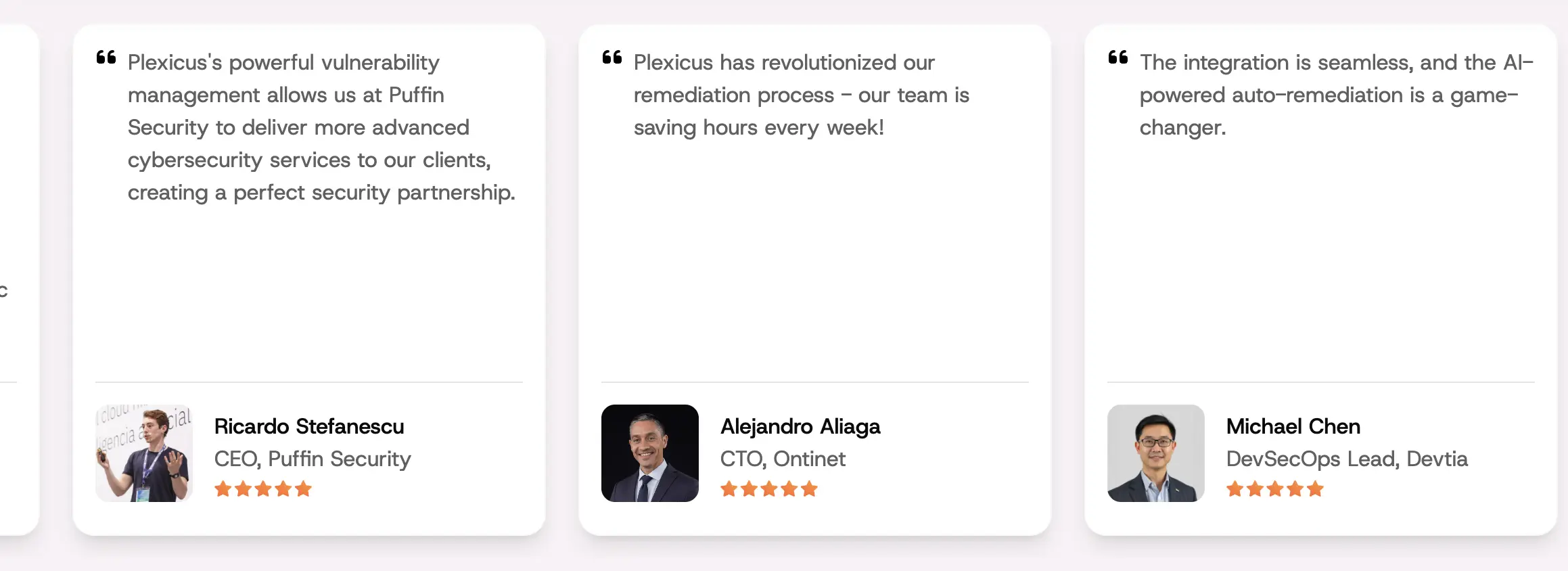
At Plexicus, we focus on Remediation. To bridge the gap from alerting to resolution, we believe detection is largely solved, but fixing issues is where many companies struggle. Now, with 41% of code generated by AI [1], the security debt is too great for manual review. We judge any tool’s success by how quickly it fixes problems (MTTR), not just how many alerts it sends.
[1] Source: “AI Coding Assistant Statistics: Trends, Usage & Market Data.” Second Talent, www.secondtalent.com/resources/ai-coding-assistant-statistics/. Accessed 31 Dec. 2025.
We also collaborate closely with various companies, ranging from innovative startups to established enterprises, to enhance our remediation capabilities with Plexicus. These partnerships allow us to integrate a diverse range of insights and technological advancements into our solutions, enabling more efficient and customized remediation outcomes. By partnering with industry leaders, we provide our clients with unique value propositions, such as quicker response times and tailored security measures, setting Plexicus apart in the competitive market.
At a Glance: Top 10 Sysdig Alternatives for 2026
| Platform | Best For | Core Differentiator | Setup Type |
|---|---|---|---|
| Plexicus | Rapid Remediation | AI-Powered “Click-to-Fix” | Agentless (OIDC) |
| Aqua Security | K8s Hardening | Full-lifecycle image assurance | Hybrid |
| Prisma Cloud | Compliance | Unified Policy-as-Code | Hybrid |
| Wiz | Cloud Visibility | The Security Graph | Agentless |
| AccuKnox | Zero Trust | KubeArmor-based enforcement | Agent-based |
| CrowdStrike | Threat Intel | Single-agent EDR + Cloud | Agent-based |
| Falco (OSS) | DIY Runtime | The original open-source core | Agent-based |
| Orca Security | Agentless Depth | SideScanning technology | Agentless |
| Lacework | Anomalies | Polygraph behavioral mapping | Agentless |
| Snyk | Developer Flow | Native IDE & PR integration | Integration |
1. Plexicus (The Remediation Leader)
Plexicus is the optimal solution for teams overwhelmed by persistent alerts. While Sysdig reveals incidents, Plexicus ensures incidents are resolved by providing effective code fixes.
- Key Features: Codex Remedium is an AI (artificial intelligence) engine that generates functional code patches (updates to fix software vulnerabilities) and Pull Requests (requests to merge code changes) for identified vulnerabilities.
- Core Differentiator: Unlike Sysdig, which focuses on runtime events, Plexicus connects runtime events to the source code. It uses runtime data to prioritize fixes for the code that is truly at risk.
- Pros: Drastically reduces MTTR; provides a “one-click” fix experience for developers; no agent required for core visibility.
- Cons: Does not provide the same level of “kernel-level” forensics as Sysdig for post-incident investigation.
- Select Plexicus to effectively reduce your vulnerability backlog and advance toward automated security. By adopting Plexicus, organizations can not only streamline their remediation processes but also demonstrate significant business impact. With our solution, businesses often experience a tangible reduction in breach-related costs and achieve smoother compliance with regulatory standards, underscoring the return on investment that resonates with leaders focused on business value.
2. Aqua Security
Aqua is a direct competitor to Sysdig, offering a more complete code-to-cloud platform with a strong focus on container integrity.
- Key Features: Dynamic Threat Analysis (DTA; a system that tests threats by running images in a controlled environment called a sandbox); strong admission controllers for Kubernetes (security checks preventing unauthorized deployments).
- Core Differentiator: Superior Image Assurance; it can block unauthorized images from ever running in your cluster.
- Pros: Highly scalable; excellent for high-compliance environments (FSIs, Gov).
- Cons: UI can be modular and complex to navigate.
3. Prisma Cloud (Palo Alto Networks)
Prisma serves as the comprehensive consolidation platform. Choose it for unified management of firewalls, cloud posture, and container runtime.
- Key Features: Unified Policy-as-Code; deep integration with Palo Alto’s threat intelligence.
- Core Differentiator: It is the most comprehensive CNAPP on the market, covering nearly every compliance framework globally.
- Pros: “Single pane of glass” for the entire enterprise.
- Cons: Extremely complex setup; requires dedicated administrators to manage.
4. Wiz
Wiz sets the standard for visibility. It is much easier to deploy across large multi-cloud environments than Sysdig, since it does not use agents.
- Key Features: The Security Graph identifies “Toxic Combinations” (for example, when a vulnerable pod, a self-contained software unit with a public IP address, and an admin-level Identity and Access Management (IAM) role create a risky configuration).
- Core Differentiator: Near-instant deployment; provides immediate value without the friction of kernel sensors.
- Pros: Incredible UI; very low noise.
- Cons: Limited deep runtime protection; cannot kill a malicious process like Sysdig.
5. AccuKnox
AccuKnox stands as the premier solution for enforcing Zero Trust in Kubernetes, leveraging the CNCF-hosted KubeArmor project.
- Key Features: Inline mitigation of threats (blocking attacks in real-time); hard-enforcement of “least privilege” policies (strict access controls that only allow the minimum permissions necessary).
- Core Differentiator: It is designed to block attacks, not just alert on them, using Linux Security Modules (LSMs; tools for enforcing security policies) like AppArmor and SELinux (security frameworks for the Linux operating system).
- Pros: True “Zero Trust” for the cloud; open-source heritage.
- Cons: High technical requirements for policy fine-tuning.
6. CrowdStrike Falcon Cloud Security
CrowdStrike enables cloud security aligned with endpoint protection, with a primary emphasis on advanced threat hunting.
- Key Features: 24/7 Managed Detection and Response (MDR; a security service that provides around-the-clock monitoring and incident response); integrated identity protection (safeguards to prevent unauthorized use of accounts).
- Core Differentiator: Uses the Falcon Agent to correlate cloud workload threats with global endpoint attack patterns.
- Pros: World-class threat intelligence; easy to buy if you’re already a CrowdStrike customer.
- Cons: Very limited “Shift Left” (code/SCA) capabilities compared to Snyk or Plexicus.
7. Falco (Open Source)
If you like Sysdig but don’t want to pay for an enterprise license, you can use Falco directly. Falco is the CNCF-graduated runtime standard.
- Key Features: Real-time kernel-level auditing; highly customizable YAML rules.
- Core Differentiator: 100% free and open-source; huge community-contributed rule library (users can create and share custom detection rules).
- Pros: Infinite flexibility; no vendor lock-in.
- Cons: No dashboard; requires significant engineering to build a custom alerting/response system.
8. Orca Security
Orca pioneered SideScanning technology. Its agentless architecture delves beyond Wiz by analyzing the disk state of virtual machines.
- Key Features: Full-stack visibility into OS, apps, and data; strong Data Security Posture Management (DSPM).
- Core Differentiator: Reads the “block storage” (digital storage used for cloud servers) of your cloud assets to find secrets (hidden sensitive data, like passwords or keys) and vulnerabilities without running code on the host.
- Pros: Zero performance impact on workloads.
- Cons: Lacks the “active response” capabilities of eBPF-based tools like Sysdig.
9. Lacework (FortiCNAPP)
Now part of Fortinet, Lacework is known for its machine learning approach. It does not rely on rules; instead, it learns the behavior of your environment.
- Key Features: Polygraph technology that maps every process interaction (tracks the way software components communicate) to find anomalies (unexpected behavior).
- Core Differentiator: Automated threat detection that requires zero manual rule-writing.
- Pros: Great for finding “Unknown Unknowns” (Zero-days).
- Cons: Can be a “black box”; it’s hard to know why it flagged an alert.
10. Snyk
Snyk is recognized among developers as a top choice. When Sysdig is not adopted by development teams, Snyk consistently delivers.
- Key Features: Native IDE integration; automated PRs for library upgrades.
- Core Differentiator: Lives entirely in the developer workflow, catching bugs before they even reach the cluster.
- Pros: Massive developer adoption (widely used by software engineers); very fast.
- Cons: Its runtime protection (Sysdig’s bread and butter) is still secondary to its AppSec features.
In 2026, security tools that only alert are considered obsolete. Leading platforms must automate remediation to keep pace with emerging threats.
FAQ: The Realities of 2026 Security
Why move away from Sysdig?
Most teams switch because of complexity and cost. Sysdig’s agent-based model is powerful but resource-intensive and expensive to maintain. If you do not need kernel forensics every day, an agentless platform like Plexicus or Wiz is often more efficient.
When considering a transition, it is crucial to evaluate the migration process and how these new tools will integrate into existing workflows. Leaders should assess the potential transition risks and plan to minimize disruption and ensure a smooth integration into their operational practices.
Can Plexicus replace Sysdig’s runtime detection?
Plexicus is engineered for Remediation. It continuously monitors your environment and facilitates the prompt resolution of vulnerabilities identified by tools like Sysdig. In 2026, most teams will deploy an agentless tool for visibility and utilize AI platforms, such as Plexicus, for remediation.
Is agentless security enough for 2026?
Current trends indicate that 28.3% of exploits launch within 24 hours of disclosure [2]. Agentless tools provide instant threat visibility across your cloud infrastructure, often surpassing the value of deep agents deployed on a portion of servers. However, it is important to acknowledge that agentless approaches might have limitations in certain scenarios.
They may not offer the same depth of analysis or ability to interact directly with the host system as agent-based tools. This transparency is crucial for decision-makers, enabling them to make informed, risk-based choices about their security posture.



