CVSS (Common Vulnerability Scoring System)
TL;DR
CVSS is a standard way to say how bad a security bug is. It gives each vulnerability a score from 0 to 10 so teams know what to fix first.
Think of it like this:
- 0.0 → No problem
- 10.0 → Drop everything and fix it now
What Is CVSS?
CVSS is a free, widely used scoring system for security vulnerabilities. It’s maintained by an industry group called FIRST, and it’s used by pretty much everyone in security.
Every vulnerability gets a number between 0.0 and 10.0 based on things like:
- How easy it is to exploit
- Whether it can be attacked remotely
- How much damage can it cause?
In simple terms:CVSS is a thermometer for software bugs.
Why CVSS Matters
Without CVSS, everyone would describe severity differently. One vendor might say a bug is “critical,” while another calls it “medium.” CVSS gives everyone a shared language.
It matters because:
- It tells teams what to fix firstMost companies set rules like: “Anything above 9.0 must be fixed within 48 hours.”
- It’s used by vulnerability databasesThe National Vulnerability Database (NVD) assigns CVSS scores to almost every CVE, which lets tools automatically sort thousands of issues.
- It removes guessworkInstead of arguing about how bad a bug feels, CVSS forces you to look at concrete factors like exploitability and impact.
How CVSS Works
CVSS has three types of scores. Most of the time, you’ll only see the first one.
1. Base Score (the one everyone uses)
This measures how bad the vulnerability is by itself, no matter where it’s deployed.
It looks at questions like:
- Can this be exploited over the internet?
- Is it easy or hard to pull off?
- Does the attacker need a login?
- Do they need to trick a user?
- What happens if it’s exploited? (data theft, system takeover, downtime)
This is the score you usually see in CVE listings.
2. Temporal Score (sometimes used)
This adjusts the score based on what’s happening right now.
For example:
- Is there public exploit code? (Score goes up)
- Is there a patch available? (Score goes down)
3. Environmental Score (advanced, optional)
This tailors the score to your environment.
For example:
- Is the system internal only? (Less severe)
- Does it hold customer data? (More severe)
A Real Example: Log4j
Log4j (Log4Shell) is one of the most famous vulnerabilities ever.
Its CVSS score was 10.0 (Critical).
Why?
- It could be exploited remotely
- It required no login
- It was easy to exploit
- It allowed full system compromise
Who Uses CVSS?
- Software vendors to explain how serious a bug is
- Security teams to focus on the most dangerous issues
- Auditors to check whether vulnerabilities are fixed on time
CVSS Score Ranges (v3.1)
Here’s how the numbers usually translate:
- 0.0 → No issue
- 0.1–3.9 → Low (fix later)
- 4.0–6.9 → Medium (fix soon)
- 7.0–8.9 → High (fix urgently)
- 9.0–10.0 → Critical (fix immediately)
Best Practices (Important)
- Don’t rely on CVSS aloneCVSS measures severity, not risk. A critical bug on a server that’s turned off is not a real threat.
- Combine CVSS with likelihoodPair CVSS with EPSS to see which bugs are actually likely to be exploited.
- Adjust for your environmentA bug on a test server isn’t the same as a bug on a production database.
- Know the versionsCVSS v4.0 exists, but v3.1 is still the most commonly used today.
Avoid Alert Fatigue
Finding security issues is only useful if your team knows what to fix first. Dumping hundreds of alerts on engineers doesn’t improve security; it creates alert fatigue
Plexicus helps by ranking vulnerabilities so your team can focus on what actually matters. Instead of treating every issue the same, Plexicus uses a few simple metrics to guide prioritization.
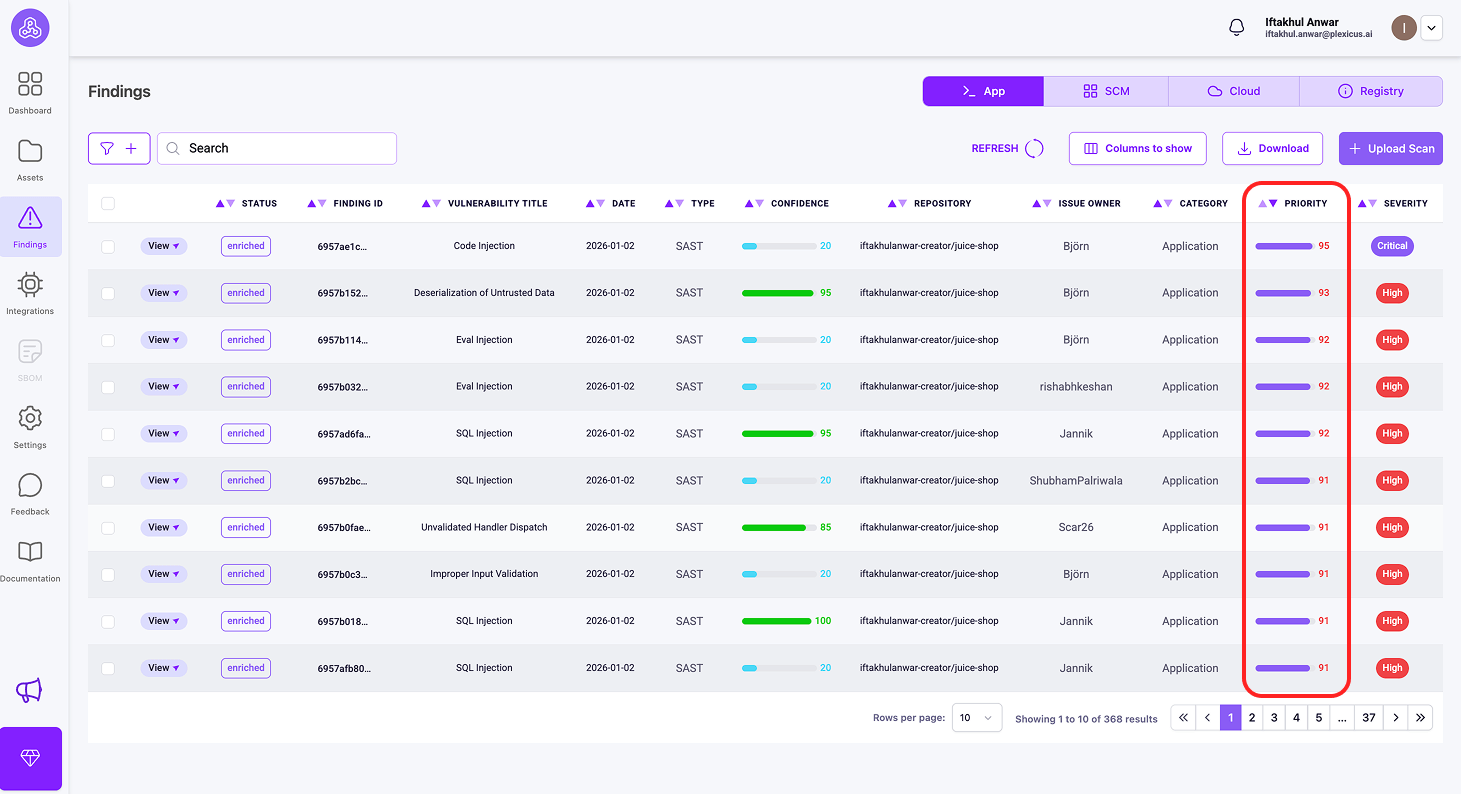
1) Priority
What it means: How urgent this issue really is
Priority is a score from 0 to 100 that rolls everything into one number:
- Technical severity (CVSS v4)
- Business impact
- How likely is it to be exploited
This is your action list. Sort by Priority and start from the top.
- Priority 85 → Drop everything and fix this now
- Priority 45 → Important, but it can wait until the next sprint
Example
A SQL injection issue in an internal tool that:
- Is only accessible via the company VPN
- Does not store sensitive data
Scores:
- CVSS v4: 8.2 (technically serious)
- Business Impact: 45 (internal tool, limited exposure)
- Exploit Availability: 30 (requires login)
- Priority: 48
Why Priority Matters
If you only looked at the CVSS score, you might panic because 8.2 sounds scary. Priority puts the issue in context and says:“This is real, but not urgent. Fix it next sprint.”
That keeps teams focused on real risk instead of reacting to every high CVSS score.
2) Impact
What it means: How bad things get if this is exploited
Impact is scored from 0 to 100 and reflects the business consequences, not just the technical ones. It looks at things like:
- Is customer data involved?
- Is this system critical to operations?
- Are there compliance or regulatory risks?
Example
- SQL injection in a public customer database → Impact 95
- The same issue in an internal test environment → Impact 30
Same bug, very different business risk.
3) EPSS
What it means: How likely attackers are to exploit this
EPSS predicts the chance that a vulnerability will be exploited in the real world within the next 30 days. It ranges from 0.0 to 1.0.
Example
- An old vulnerability with CVSS 9.0 but no active attacks → EPSS 0.01
- A newer vulnerability with CVSS 6.0 that attackers are actively using → EPSS 0.85
EPSS helps you focus on what attackers care about right now, not just what looks bad on paper.
How to Use These Metrics in Plexicus
- Connect your repository and wait for the scan to finish
- Go to the Findings page
- Sort and filter by Priority to decide what to fix first
Related Terms
- CVE (Common Vulnerabilities and Exposures)
- EPSS (Exploit Prediction Scoring System)
- Vulnerability Management
- NVD (National Vulnerability Database)
CVSS FAQ
What’s the highest CVSS score?
10.0. It means the bug is easy to exploit and causes major damage.
Is a 9.0 always worse than a 7.0?
On paper, yes. In reality, not always. A 7.0 that’s actively exploited can be more dangerous than a 9.0 that no one is using.
Who sets the CVSS score?
Usually, the software vendor or the NVD. Sometimes security researchers do.
Can I change a CVSS score internally?
Yes. Many teams adjust scores to reflect their real-world setup, especially if they have strong protections in place.