What Is RBAC (Role-Based Access Control)?
Role-based access control, or RBAC, is a method to manage system security by assigning users to specific roles within an organization. Each role comes with its own set of permissions, which decide what actions users in that role are allowed to take.
Instead of giving permission to every user, you can assign it based on roles (e.g, administrator, developer, analyst, etc).
This approach makes it much easier to manage access in large organizations with many users.

RBAC model visualizing how users connect to roles and permissions for secure access control
Why RBAC Matters in Security
Access control is a key part of cybersecurity. For example, a contractor once downloaded 6 GB of sensitive data because they had too many permissions. Without proper access control, employees or contractors might reach information they shouldn’t, which can lead to data leaks, insider threats, misconfiguration, or even theft.
RBAC supports the principle of least privilege, meaning users only get the access they need. This is a key idea in web application security.
How the RBAC Model Works
The RBAC model typically includes 3 components :
- Roles: These are defined job functions or responsibilities within an organization, such as HR Manager or System Administrator. A role groups together specific permissions needed to perform its tasks.
- Permission - Particular action to perform, such as delete user, modify document, update database, etc.
- Users - Individuals assigned to one or more roles
Example :
- Admin role : can manage users, configure the system, and view logs
- Developer role : can push code, run builds, but cannot manage users
This mechanism ensures consistency and reduces risk compared to managing individual user permissions.
Advantages of RBAC
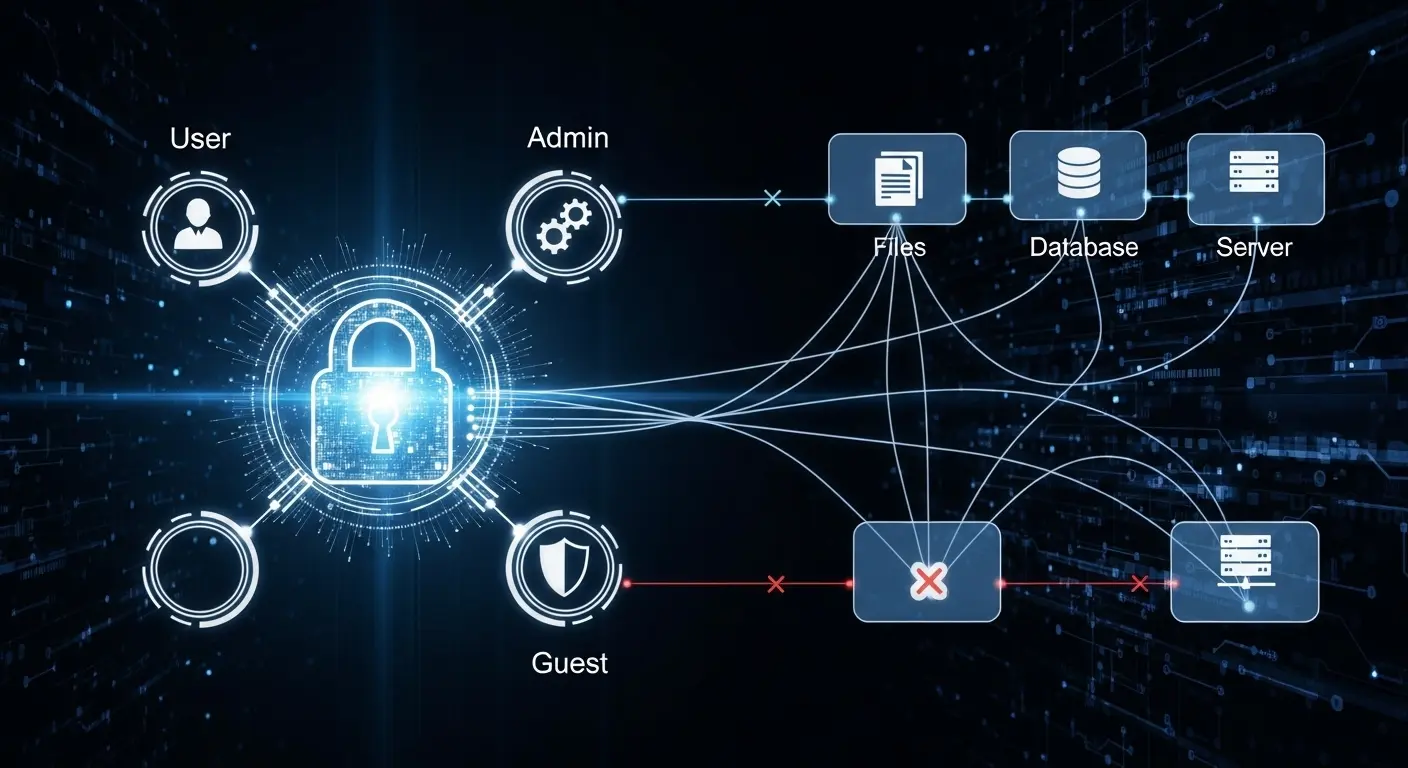
Example of RBAC implementation where users, admins, and guests have different access levels to files, databases, and servers
- Improve security : By implementing least privileges, RBAC can minimize the risk of unauthorized users accessing sensitive data, reducing the attack surface and limiting potential damage from insider threats.
- Scalability an organization grows, it is a problem if you manage permissions individually. RBAC simplifies this process by grouping users based on role and managing permissions for it. It will be easier to compare to manage permissions individually.
- Operational efficiency : RBAC helps organizations to reduce repetitive tasks. The administrator only adjusts the role definition instead of granting or revoking access user by user, which takes time for a large organization.
- Compliance : Many regulatory frameworks, such as GDPR, HIPAA, and PCI DSS, require strict access controls to protect sensitive data. RBAC helps organizations align with these requirements by enforcing structured access rules. Demonstrating role-based access policies not only avoids fines but also builds trust with customers and regulators.
- Auditability: RBAC provides a clear mapping of ‘who accesses what’ to facilitate transparency. However, incomplete RBAC mappings can have serious consequences during an audit.
Common Challenges of RBAC
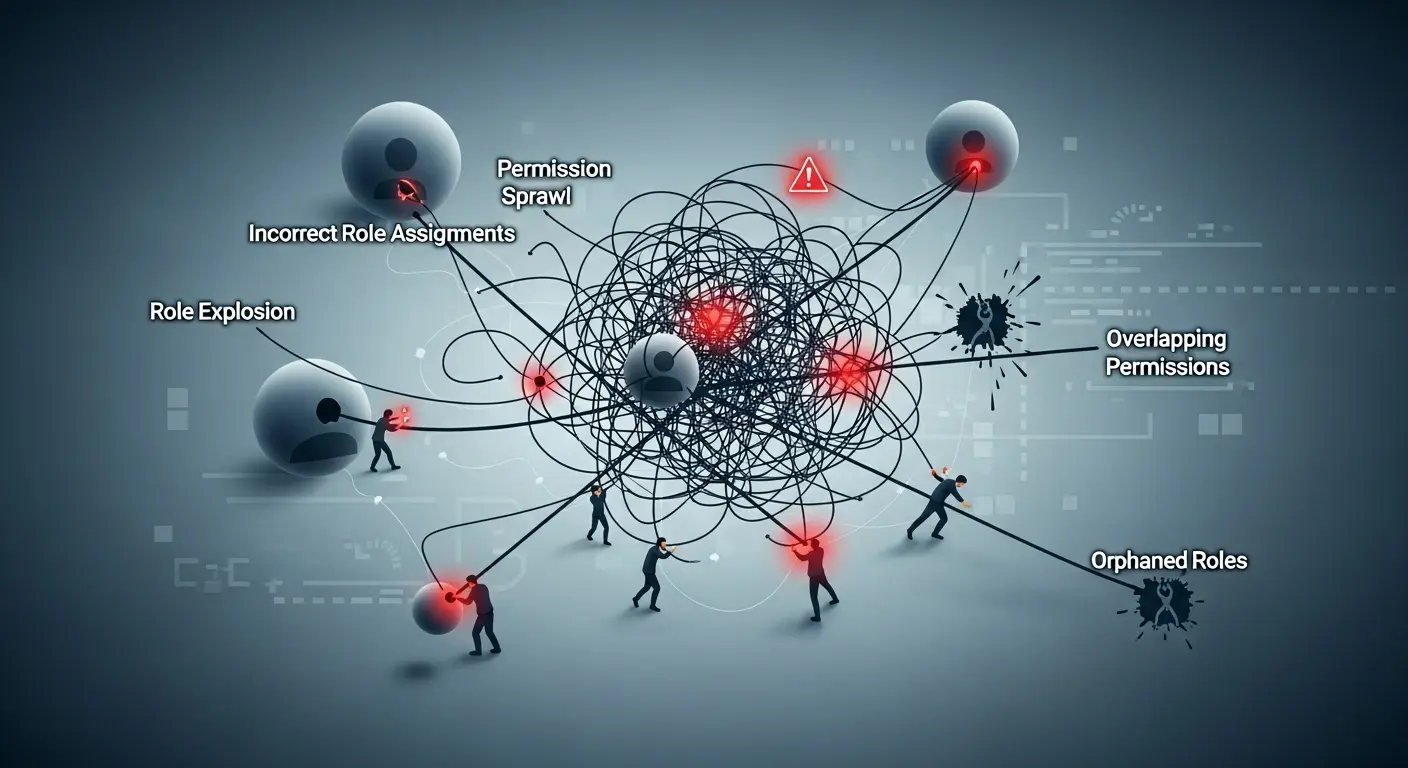
- Role explosion occurs when an organization creates too many very specific roles instead of broader categories, making it hard to maintain. This can lead to problems when the number of roles exceeds the number of employees by about 20 percent, as managing so many roles becomes impractical.
- Rigid structure : RBAC relies strictly on predefined roles, which makes it less flexible in dynamic environments compared to ABAC, where access can adapt based on user, resource, or environmental attributes.
- Maintenance overhead : Roles and permissions must be reviewed and updated regularly to prevent privilege abuse and ensure users don’t have unnecessary access.
- Overlapping permissions: When multiple roles are granted to similar or identical permissions. It will make it harder to audit, create redundancy, and confuse the administrator.
- Permission Sprawl : Over time, there is organizational change, and users accumulate multiple roles. If role assigned to a user is not updated or revoked when the position or responsibilities change, it will make broader access than is necessary, which violates the least privilege principle.
- Orphaned Role : A Role that is not aligned with the current business need or a role not assigned to any user. It can be a blind spot for vulnerabilities if not reviewed regularly.
RBAC vs ABAC
While RBAC is role-focused, Attribute-based Access Control gives user access based on attributes like user, environment, and resources.
| Feature | RBAC | ABAC |
|---|---|---|
| Basis of access | Predefined roles | Attributes (user, resource, environment) |
| Flexibility | Simple but rigid | Very flexible, dynamic |
| Best for | Large organizations with stable roles | Complex, context-aware environments |
Below implementation in web application security
| Access Model | Example Scenario | Who Can Do What | How Access Is Decided |
|---|---|---|---|
| RBAC (Role-Based Access Control) | Project management web app (e.g., Jira/Trello) | - Admin → Create projects, manage users, delete boards- Manager → Create/assign tasks, no project deletion- Employee → Update only their tasks- Guest → View tasks only | Based on predefined roles assigned to users. No contextual conditions. |
| ABAC (Attribute-Based Access Control) | Same project management web app, but with attributes | - Manager → Access tasks only in their department (user attribute) - Employee → View project files only if project is active (resource attribute) - Contractor → Access system only 9 AM–6 PM and from office network (environment attributes) | Based on policies using attributes: user + resource + environment. Context determines access. |
RBAC Best Practices
To implement RBAC effectively, consider the following self-assessment checklist:
- Least privileges: Are roles providing only the necessary access needed for the job?
- Regularly review roles: Do we review roles quarterly to identify and update any unused or outdated roles?
- Avoid role explosion: Are we maintaining broader, but meaningful roles to prevent excessive and detailed role creation?
- Audit access logs: Are access logs checked regularly to ensure that user activities match their defined roles?
- Automate where possible: Are we leveraging Identity and Access Management (IAM) tools to automate routine access management tasks?
How Plexicus ASPM Strengthens RBAC and Access Security
Implementing RBAC is only part of a strong security posture. Modern organizations also need continuous visibility into vulnerabilities, misconfigurations, and access risks across applications and cloud environments.
This is where [Plexicus ASPM] comes in.
- ✅ Unifies security: Combines SCA, secrets detection, API scanning, and more in a single platform.
- ✅ Enforces least privilege: Helps you spot overly permissive access, orphaned roles, and misconfigurations that RBAC alone can’t catch.
- ✅ Supports compliance: Generates audit-ready reports for frameworks like GDPR, HIPAA, and PCI DSS.
- ✅ Scales with growth: Works across complex applications and cloud-native environments without adding friction.
By integrating Plexicus ASPM, teams can move beyond just role assignments to full application security posture management—reducing risk from excessive permissions, misconfigurations, and vulnerable dependencies.
Related Terms
- ABAC (Attribute-Based Access Control)
- IAM (Identity and Access Management)
- Least Privilege Principle
- Zero Trust Security
- Authentication
- Access Control List (ACL)
- Privilege Escalation
- Application Security Posture Management (ASPM)
FAQ: RBAC (Role-Based Access Control)
What does RBAC stand for in security?
RBAC stands for Role-Based Access Control, a security mechanism for managing permissions by grouping users based on role
What is the purpose of RBAC?
The purpose of applying the least privileges, simplify access management and reduce security risks.
What is an example of RBAC?
A hospital gives access patient’s chart to nurses, but only a doctor can create a medical prescription. This is one example of RBAC implementation; even in the real world, it can be applied.
What are the advantages of RBAC?
Simplify user access management, improve security, reduce risks, simplify audit, and provide compliance support.
What’s the difference between RBAC and ABAC?
RBAC manages access based on roles, ABAC based on policies. RBAC is simpler but rigid; ABAC is more complex but gives flexibility